List Categories and Listings by F
The FlowMon solution delivers the flow-based (NetFlow/IPFIX) monitoring for all organizations and all networks from 10 Mbps to 10 Gbps. It provides the statistics necessary for network monitoring, security, troubleshooting, IP accounting and billing, capa ...
floppyfw is a router with the advanced firewall-capabilities in Linux that fits on one single floppy disc.
One-way data transfer with optical isolation for uncompromising network security & protection Create boundaries between trusted & untrusted networks by creating a physically secure one-way communication channel. Send data from one secure network ...
3 years Full Time
FortiGate Next-Generation Firewalls deliver enterprise security at any scale with full visibility and threat protection. Organisations can weave security into the hybrid IT architecture and build security-driven networks to achieve: Ultra-fast security ...
FortiWeb, Fortinet’s Web Application Firewall, protects your business-critical web applications from attacks that target known and unknown vulnerabilities. FortiWeb WAFs provide advanced features that defend your web applications and APIs from known and ...
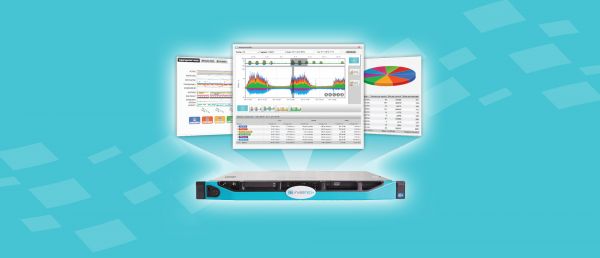
FlowNBA is a complete solution for network monitoring based on NetFlow/IPFIX. Thanks to the used technology it enables complete overview of the network traffic, detailed information about all communications and provides information about who communicates ...
Forensic Explorer analysis software. Suitable for new or experienced investigators, Forensic Explorer combines a flexible and easy to use GUI with advanced sort, filter, keyword search, data recovery and script technology. Quickly process large volumes o ...
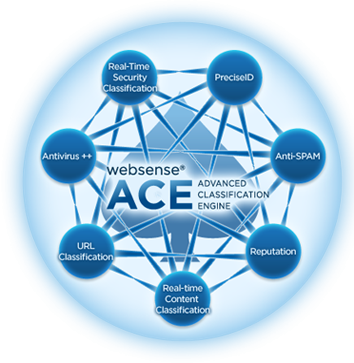
Forcepoint’s Advanced Classification Engine (ACE) delivers optimized threat defenses through deep content inspection of traffic, which is performed in real time. ACE’s eight defense assessment areas enable Forcepoint solutions to protect against emerging ...
Every second of the day, the Forcepoint ThreatSeeker Intelligence scours the vast expanse of online content for potential threats. It’s up to the task. It receives global input from over 155 countries and, working in parallel with Forcepoint ACE, analyzes ...
F-Response is a vendor neutral, patented software utility that enables an investigator to conduct live forensics, Data Recovery, and eDiscovery over an IP network using their tool(s) of choice. F-Response is not another analysis tool. F-Response is a util ...
4 years Full Time
4 years Full Time / 5 years Full Time
4 years Sandwich Course
4 years Full Time / 5 years Sandwich Course
4 years Full Time
3 years Full Time / 4 years Sandwich Course
2 years Full Time
3 years Full Time
File integrity monitoring (FIM) protects sensitive information from theft, loss, and malware. Included as part of the Security Event Manager software suite.