List Categories and Listings by H
This training course offers a collection of live demonstrations featuring a variety of hacking and defensive techniques used by hackers. Tranchulas online labs are available 24×7 for practising the techniques and tools demonstrated by our instructor durin ...
This training course is a series of educational interactive training sessions where the attendees will gain hands-on experience. They will be able to identify security flaws in web applications customised or built for the training course. They will also b ...
Harmony Endpoint provides comprehensive endpoint protection at the highest security level, crucial to avoid security breaches and data compromise. Harmony Endpoint is a complete endpoint security solution built to protect the remote workforce from today’ ...
Phishing Training Designed for People. Built for Enterprise. Cognitive automation enables individual learning paths that motivate people to recognize and report real attacks. 90% of breaches start with email. Focus your training where it's needed most. ...
HCL BigFix is an endpoint management platform which enables the automation of discovery, management and remediation - whether its on premise, virtual, or cloud - regardless of operating system, location or connectivity. Keep all of your endpoints patched ...
AppScan delivers application security testing tools to ensure your business, and your customers, are not vulnerable to attacks. Detect application vulnerabilities before they become a problem, remediate them and ensure compliance with regulations. Four pr ...
HashMyFiles is a small utility that allows you to calculate the MD5 and SHA1 hashs of one or more files on your system. You can easily copy the MD5/SHA1 hashes list into the clopboard, or save them into text/html/xml file. You are also able to launch Has ...
HexBrowser is a tool that identifies file types. It ignores file extensions, and focuses on the signatures that the file contains, so it is able to determine the exact type of file. It now recognises more than 1000 different file formats. HexBrowser show ...
Hacker Guardian PCI Compliance Scanning is designed for Website owners and E-commerce Merchants to secure transactions, in accordance with PCI Standards. HackerGuardian PCI Scanning is a vulnerability assessment scanning solution designed to achieve and ...
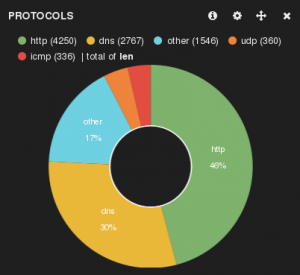
Hakabana is an open source monitoring tool, which allows users to visiualizes Haka network traffic using Kibana and Elasticsearch. It leverages on the Haka framework to capture packets, dissect them and extract various pieces of information from the ...
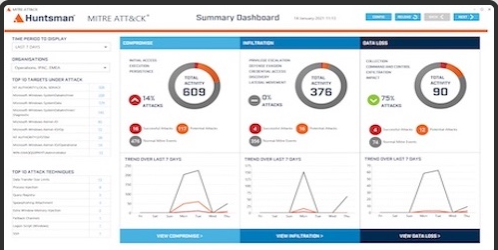
An ‘Always On’ Cyber Security Analytics Tool that deploys from a single SOC platform managed by your team. DEFENCE-GRADE CYBER SECURITY for all organisation types and sizesLIVE MITRE ATT&CK THREAT HEATMAP with easy to access alerts and reportingRESPO ...
HackerTarget.com provides free security scans for websites. You can purchase a Scan Membership, which then removes the scan limits per day. They provide scans using known, Open Source tools, including: * Nmap Port Scan * Nikto Web Scan * OpenVas ...
Hitachi ID Bravura Privilege secures access to elevated privileges. It eliminates shared and static passwords to privileged accounts. It enforces strong authentication and reliable authorization prior to granting access. User access is logged, creating st ...
Hitachi ID Bravura Identity is an integrated solution for managing identities, groups and security entitlements across systems and applications. It ensures that users are granted access quickly, that entitlements are appropriate to business need and that ...
Hitachi ID Bravura Pass is an integrated solution for managing credentials across systems and applications. It simplifies the management of passwords, tokens, smart cards, security questions and biometrics. Bravura Pass lowers IT support cost and imp ...
This training course is a series of educational interactive training sessions where the attendees will gain hands-on experience. They will be able to identify security flaws in web applications customised or built for the training course. They will also b ...
hping2 is an interactive packet costructor and responses analyzer that uses the same CLI of the ping program (but with a lot of extensions). It can be used to performs a lot of tasks, like testing of firewall rules, (spoofed) port scanning, et cetera.
httpry is a specialized packet sniffer designed for displaying and logging HTTP traffic. It is not intended to perform analysis itself, but to capture, parse, and log the traffic for later analysis. It can be run in real-time displaying the traffic as it ...
Free SSL Sniffer We have decided to release a very straightforward free HTTP and HTTPS sniffer (SSL sniffer) for Internet Explorer (versions 6.0 and 7.0) and Mozilla Firefox, in order to demonstrate the abilities of our SSL redirector SDK platfor ...
Hexamail Guard acts as a sentinel for your incoming and outgoing mail. By analyzing each mail received and sent by your organization it intelligently alerts, routes, blocks and audits all email traffic. Features include: Anti-Spam, AntiVirus, Trojan a ...