List Categories and Listings by U
Unicornscan is a new information gathering and correlation engine built for and by members of the security research and testing communities. It was designed to provide an engine that is Scalable, Accurate, Flexible, and Efficient. It is released for the c ...
The USENIX Security Symposium brings together researchers, practitioners, system administrators, system programmers, and others interested in the latest advances in the security of computer systems and networks.
A hands-on course focusing on security of UNIX systems. Hands on sessions will be with Red Hat Linux but the course covers all flavours of UNIX and highlights differences.
This course will give the ultimate comparison of classic Windows attacks directed at Windows 2000 and Windows 2003 networks. Using the unique Foundstone Hands-On approach and an innovative parallel learning technique, you will execute all demonstrations, ...
What Will You Learn? For the advanced security engineer, this course is the pinnacle of the Ultimate Hacking series and is a continuation of the Ultimate Hacking: Hands On course. It encompasses such topics as wireless security, SQL injection techniques, ...
What Will You Learn? Foundstone consultants/instructors bring real-world experience to the classroom to empower you with the skills to assess your security posture and implement effective countermeasures. As always Foundstone brings its consulting experie ...
Unhide is a forensic tool to find hidden processes and TCP/UDP ports by rootkits / LKMs or by another hidden technique. // Unhide (ps) Detecting hidden processes. Implements six techniques * Compare /proc vs /bin/ps output * Compare inf ...
Utilikilts offers a total of 6 different models Standard Models: The Mocker The Spartan The Workman The Survival Special Offerings or Limited Run Offerings: The Tuxedo The Beast (Leather)
UMRA is a complete User Management System that simplifies Active Directory Management across all your systems. While managing user account and authorization processes in Active Directory and adjacent systems, UMRA also offers delegation of user account ma ...
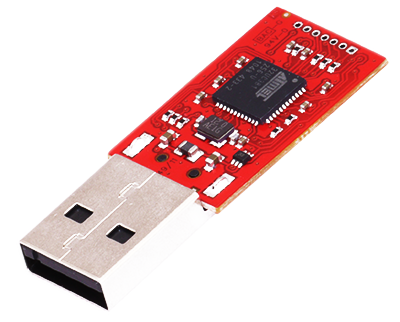
'Since 2010 the USB Rubber Ducky has been a favorite among hackers, penetration testers and IT professionals. With origins as a humble IT automation proof-of-concept using an embedded dev-board, it has grown into a full fledged commercial Keystroke I ...