List Categories and Listings by D
Welcome to the largest underground hacking event in the world. DefCon hosts lots of small, regional meetings, and a DefCon event that coincides with the Black Hat Briefings in Las Vegas.
DefensePro’s behavior-based, self-learning mechanism proactively scans for anomalous network, server and client traffic patterns. When detecting an attack, DefensePro characterizes the attack’s unique behavior, establishes a real-time signature and create ...
DroidBox is developed to offer dynamic analysis of Android applications. The following information is described in the results, generated when analysis is complete: Hashes for the analyzed package Incoming/outgoing network data File read and write op ...
The Deep-Secure Chat Guard is one of our family of Content Inspection Guards. It controls the use of Internet standard chat, to allow an organisation to make use of chat without putting sensitive information or critical business processes at risk.   ...
Data protection does not have to get in the way of business productivity. Forcepoint’s focus on unified policies, user risk, and automation makes data security frictionless and intuitive. Control all your data with one single policyReplace broad, sweepin ...
DB Audit and Security 360 is a complete out-of-the-box database security & auditing solution for Oracle, Sybase, MySQL, DB2 and MS SQL Server. DB Audit allows database and system administrators, security administrators, auditors and operators to track and ...
An extensible network forensic analysis framework. Enables rapid development of plugins to support the dissection of network packet captures. Key features:Robust stream reassemblyIPv4 and IPv6 supportCustom output handlersChainable decoders
Duo Insight is a free phishing assessment tool by Duo Security that allows you to find vulnerable users and devices in minutes and start protecting them right away.
DARKBEAST provides incident responders, threat hunters, investigators, and intelligence analysts with a robust technology to dive into the cybercrime underground and investigate through KELA's cybercrime data lake. Gain visibility into underground operati ...
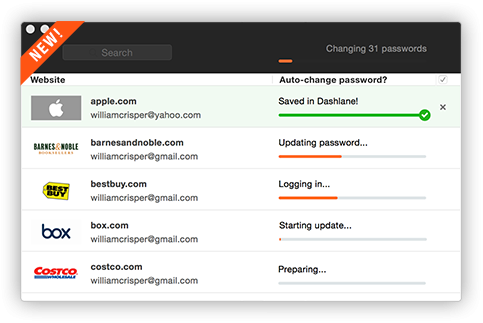
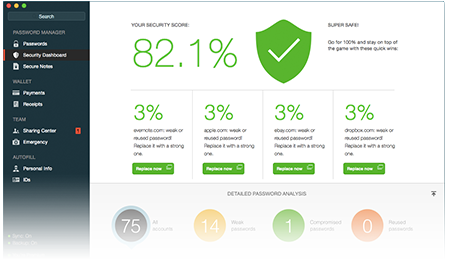
Dashlane fills all your passwords, payments, and personal details wherever you need them, across the web, on any device. Every password, Everywhere Save passwords and logins as you browse. Store an unlimited number of passwords and access them anywhe ...
This product controls network management traffic as it passes between the enterprise networks and the management system. Its self-defending architecture means it can exert the required control without itself becoming vulnerable to attack. Feature ...
Damn Small SQLi Scanner (DSSS) has been made as a PoC where I wanted to show that commercial (SQLi) scanners can be beaten under 100 lines of code. It supports GET and POST parameters, blind/error SQLi tests and advanced comparison of different r ...
Web Guard is an HTTP(s), ICAP and Deep Secure File Sharing (DSFSP) proxy. It uses policy-based rules to detect threats and enforce compliance, accountability and brand protection on Web downloads and uploads as well as Webmail attachments and cross domain ...
4 years Full Time
4 years Sandwich Course
4 years Full Time
3 years Full Time / 4 years Sandwich Course
3 years Full Time / 4 years Sandwich Course
4 years Full Time
DBAPPSecurity Database Auditor(DBAuditor)helps users to enhance the transparency of database monitoring and reduce the cost of manual auditing so as to visualize database running, monitor daily operation, control dangerous operation, audit all activities ...