List Categories and Listings by M
Mac Forensics Training Featured
This forensics training course (3 days) gives delegates a practical understanding of Data structures and potential evidence as produced in Apple Mac OS X environments and Implementing forensic tools on Mac OS X-based file systems. Highlights of this t ...
The Metasploit Framework is a development platform for creating security tools and exploits. The framework is used by network security professionals to perform penetration tests, system administrators to verify patch installations, product vendors to perf ...
This specialist course focuses on the technical aspects of computer system security and systems management. The award is designed to provide up-to-date, relevant and practical information on the technical aspects of computer security. This field is becomi ...
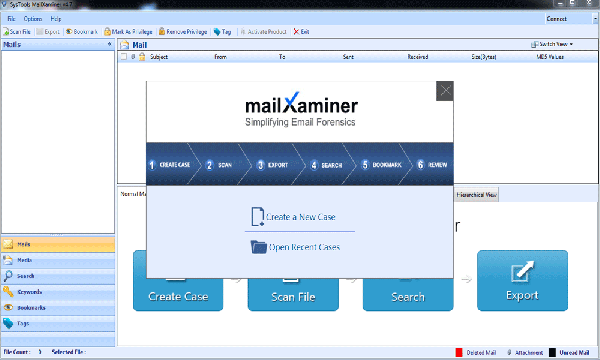
MailXaminer is a comprehensive email examination tool to carry out a thorough analysis of a bunch of emails and its header. With the help of this tool; forensicators can preview more than 20 email file types and perform advanced search operation within th ...
Microsoft Defender is simplified online security that meets you and your family where you are by bringing multiple protections together into a single dashboard. It provides online protection across the devices you and your family use. It offers tips and r ...
Have you ever considered what makes an anti-malware application effective? We at Malwarebytes have created an easy-to-use, simple, and effective anti-malware application. Whether you know it or not your computer is always at risk of becoming infected with ...
ModSecurity is an open source, cross-platform web application firewall (WAF) module. Known as the "Swiss Army Knife" of WAFs, it enables web application defenders to gain visibility into HTTP(S) traffic and provides a power rules language and API to imple ...
McAfee VirusScan Enterprise combines anti-virus, anti-spyware, firewall, and intrusion prevention technologies to stop and remove malicious software. It also extends coverage to new security risks and reduces the cost of responding to outbreaks with low i ...
The Center for Cybersecurity Education and Leadership at Montreat College provides guidance and oversight to our academic program, to the distribution of cyber defense information, and to collaborative efforts in cybersecurity with an emphasis on combinin ...
Endpoint Central (formerly Desktop Central) is a unified endpoint management and security solution that helps in managing servers, laptops, desktops, smartphones, and tablets from a central location. It's a modern take on desktop management that can be sc ...
A free tool that provides a simple, safe and effective mechanism for security teams and administrators to run their own phishing tests inside their organization. Simply install the application on a server or workstation and create a url email/sms/etc. cam ...
Configuration Manager simplifies the complex task of delivering and managing updates to IT systems across the enterprise. Use Configuration Manager to help you with the following systems management activities: Increase IT productivity and effici ...
McAfee Policy Auditor helps you report consistently and accurately against key industry mandates and internal policies across your infrastructure or on specific targeted systems. Policy Auditor is an agent-based IT audit solution that leverages the Securi ...
Network Threat Behavior Analysis monitors and reports unusual network behavior by analyzing traffic from switches and routers from vendors such as Cisco, Juniper Networks, and Extreme Networks. Network Threat Behavior Analysis collects and analyzes traff ...
MOBILedit Forensic is a phone extractor, data analyzer and report generator all in one solution. A powerful 64-bit application using both the physical and logical data acquisition methods, MOBILedit Forensic is excellent for advanced application analyzer, ...
The non-intrusive design of McAfee Database Event Monitor for SIEM supports your expanding compliance auditing and reporting requirements and enhances security operations. While it monitors all database transactions, Database Event Monitor for SIEM provid ...
The McAfee Application Data Monitor appliance decodes an entire application session to Layer 7, providing a full analysis of everything from the underlying protocols and session integrity all the way up to the contents of the application (such as the text ...
With the explosion of smartphones in the workplace, employees have recognized and demanded support for a growing list of new ways to leverage this technology for their work. Faced with the realities of dealing with an increasingly mobile workplace, organi ...
Defeat business email compromise using advanced heuristics, BEC scam analysis, sender authentication enforcement & controls, and domain intelligence to help block typo squatting and identity spoofing.Protect your brand reputation by using automation t ...
The main target of M-ICE are hostbased ID Systems but it is also possible to interoperate with other IDS architectures as long as they use the open and standarized message format IDMEF. The main goal of M-ICE is to fit for every infrastructure and to be h ...