List Categories and Listings by L
Linux and other operating systems face a number of threats in a networked environment. It is possible to secure Linux against these threats. The Leading Edge Linux Security course provides an understanding of the security threats as well as the techniques ...
Powerful security for your online world, with convenience. 1 platform, 3 products to choose from. Whether you need to make managing your passwords a no-brainer, or share files securely with your team members, or keep hackers out of your life, we can make ...
Real-time threat detections across endpoints, data centers, and the cloud. Securing your network against advanced persistent threats (APTs) requires greater visibility to detect actors and their actions so that you can reduce your response time. As threa ...
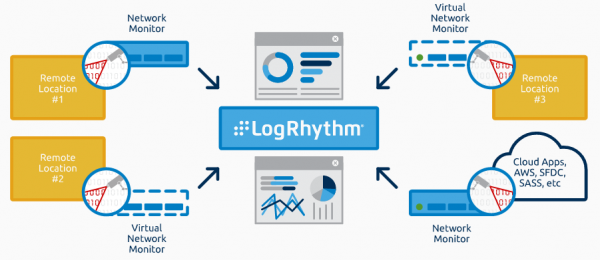
Unleash the power of your SOC with the LogRhythm NextGen SIEM Platform Detect threats earlier and fasterWhen it comes to stopping threats, seconds matter. That’s why we built our NextGen SIEM platform for speed. You’ll quickly identify threats, automate ...
The LUCY Social Engineering Suite and Malware Testing Suite (or CYBERSECURITY CRASH TEST DUMMY) facilitate multiple application areas. They can be used for: – People testing and education – Technology assessments – An inoffensive penetration test sho ...
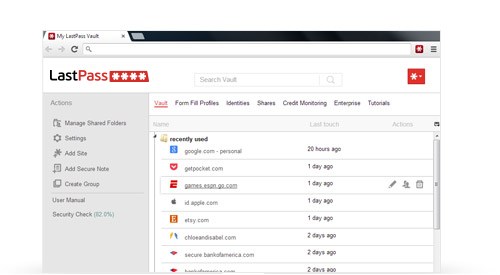
Save as You Go: Download and setup with LastPass in minutes. Once you've created your account, LastPass prompts you to save new sites as you browse - so you'll never lose another password. Hassle-Free Login: After saving a website's username and passwo ...
Application vulnerability mitigation is the next wave of cybersecurity. By analyzing source code, AVM systems are able to scan for, identify, and automatically mitigate application vulnerabilities. This process dramatically increases the security threshol ...
A web application penetration testing tool that can extract data from SQL Server, MySQL, DB2, Oracle, Sybase, Informix, and Postgres. Further, it can crawl a website as a vulnerability scanner looking for sql injection vulnerabilities. Features ...
Security Center network access protection software designed to provide real-time network security monitor for intrusion detection IDS and prevention IPS that helps to protect networks from being vulnerable to unauthorized network connections, malicious ne ...
log2timeline is a framework for automatic creation of a super timeline. The main purpose is to provide a single tool to parse various log files and artifacts found on suspect systems (and supporting systems, such as network equipment) and produce a timeli ...
This fast-paced, hands-on class will teach you how to secure UNIX and lock down Linux to protect a system from compromise. You'll learn how the attacks work and how to use hard-core hardening to defeat the bulk of them. You'll learn how to take your machi ...
Learn how to set up and administer a Linux(TM)-based firewall.
Logsurfer is a program for monitoring system logs in real-time, and reporting on the occurrence of events. It is similar to the well-known swatch program on which it is based, but offers a number of advanced features which swatch does not support. Logsur ...
This course focuses on network security and makes an excellent companion to: Enterprise Linux Security Administration (QLG55) After a detailed discussion of the TCP/IP suite component protocols and Ethernet operation, practice using various tools to ca ...
10-Strike LANState is a network mapping, monitoring, management, and administration software solution for corporate Microsoft Windows networks. LANState generates the network map, which speeds up accessing to remote hosts' properties and resources, and ma ...
This intermediate course is intended for administrators and support personnel who wish to learn the key skills required to implement security on Linux installations. As more servers on the network move to the Linux operating system, security becomes an in ...
After a detailed discussion of the TCP/IP suite component protocols and Ethernet operation, practice using various tools to capture, analyze, and generate Internet Protocol (IP) traffic. Then explore the tools and techniques used to exploit protocol we ...
LayerOne is a computer security conference located in Pasadena, California. We are currently in our third year of operation. We are featuring speakers from all across the globe and on topics ranging from lockpicking and MPLS security to covert data gather ...
The LANenforcer 2024 and 2124 LAN Security Appliances transparently integrate into existing network infrastructures, sitting between existing switches at the access and distribution layers. The LANenforcer Appliance is an ideal solution for organizations ...
LutelWall (formerly known as Lutel Firewall) is high-level linux firewall configuration tool. It uses human-readable and easy to understand configuration to set up Netfilter in most secure way. Its flexibility allows firewall admins build from very simple ...