List Categories and Listings by I
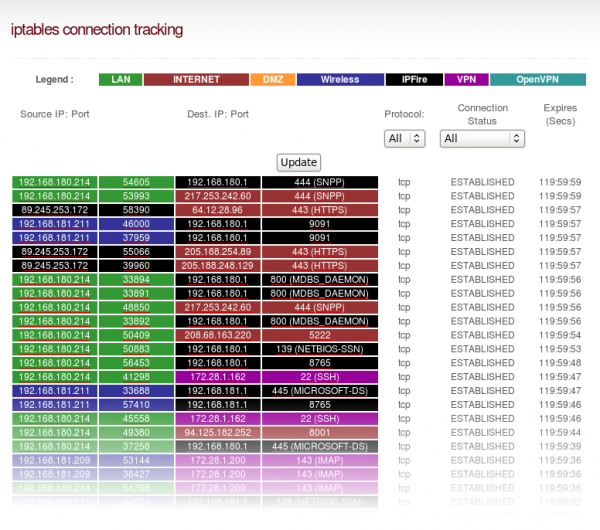
iptables is a generic table structure for the definition of rulesets. Each rule within an IP table consists of a number of classifiers (iptables matches) and one connected action (iptables target).
Since 1980, the IEEE Symposium on Security and Privacy has been the premier forum for presenting developments in computer security and electronic privacy, and for bringing together researchers and practitioners in the field.
This hands-on track offers a practical working knowledge in intrusion detection and traffic analysis, taught by top practitioners/authors in the field. This is the most advanced program in network intrusion detection that has ever been taught. All of the ...
DFLabs IncMan Suite, Collaborative Incident Response and Threat Intelligence PlatformIncMan Suite is a comprehensive CyberSecurity incident and data breach investigation & response platform that simplifies the collaborative management of every k ...
Prepare every employee with phishing simulations and training Stop dreading the day a phishing attack slips past your cyber defenses. Get the peace of mind from knowing your employees are prepared if it happens. Choose from 1,000+ realistic phishing tem ...
Features: Intelligent insights across environments - provides visibility and applies context to on-prem and cloud-based resources; leverages continuous monitoring for a zero trust approach to security. Built-in analytics to accurately detect threats - ...
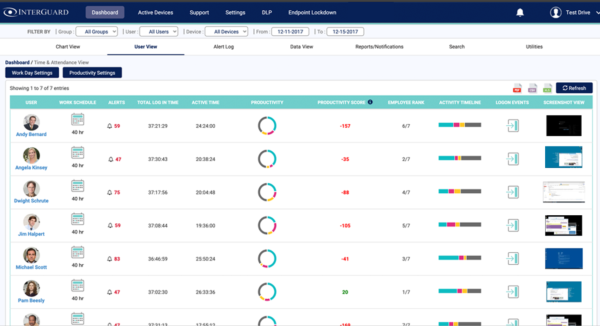
InterGuard’s employee monitoring software lets you track all employees activity from any endpoint - even when they work from home. Monitoring employee computer activity helps you proactively identify which employees are being productive and how much time ...
Code42 Incydr is a SaaS data risk detection tool that locates and mitigates insider threats without disrupting regular operations. It monitors and documents how employees use and share data between their computers and cloud services. All user activity is ...
ImmuniWeb - Web Penetration Testing. ImmuniWeb is a web application security and penetration testing service from High-Tech Bridge. It combines managed vulnerability scanning with manual penetration testing.
Perform full file system and logical acquisition of iPhone, iPad and iPod Touch devices. Image device file system, extract device secrets (passwords, encryption keys and protected data) and decrypt the file system image. Features and Benefits: ...
Ike-scan is a command-line tool that uses the IKE protocol to discover, fingerprint and test IPSec VPN servers. It is available for Linux, Unix, MacOS and Windows under the GPL license.
The iVe Ecosystem is a collection of tools that supports investigators throughout the entire vehicle forensics process with a mobile application for identifying vehicles, a hardware kit for acquiring systems, and forensic software for analyzing data. &nb ...
With IPFire you can easily deploy many variations of it, such as a firewall, a proxy server or a VPN gateway. IPFire forms the base of a secure network. It has the power to segment networks based on their respective security levels and makes it easy to cr ...
IPS Visio Stencils Popular
Stencils for many popular IPS products, including Nitro SIEM (McAfee ESM), Palo Alto Intrusion Prevention, Enterasys (Dragon) Intrusion Prevention, SourceFire, TippingPoint, Juniper, IBM, Cisco, McAfee Intrushield M-Series, and Fortinet. Also other generi ...
OverviewIntercept X for Mobile protects your Android device without compromising performance or battery life. Real-time synchronization with SophosLabs ensures that your mobile device is always protected from the latest malware and online threats – just l ...
Inundator is a multi-threaded, queue-driven, anonymous intrusion detection false positives generator with support for multiple targets. At a high level, Inundator builds an attack queue, organized by destination port, by parsing the content: and uricon ...
3 years Full Time
3 years Full Time
Add deep context, intelligence and security to decisions about which users should have access to your organization’s data and applications, on-premises or in the cloud. Modernized, modular IBM Security Verify solution provides deep, AI-powered context fo ...
Winfrasoft IAG Appliance solution running IAG 2007 (Microsoft Forefront Edge Security and Access) provides mobile and remote workers an easy to use method of accessing corporate resources from any location, using a variety of end-point devices such kiosks ...