There are a number of organisations who score the reputation of hosts on the Internet, security products then quiz this source of information and apply this knowledge to source and destination addresses as well as other content which is detected on the networks which they are monitoring
Geolocation
file reputation
website reputation
email reputation
network address reputation
Every second of the day, the Forcepoint ThreatSeeker Intelligence scours the vast expanse of online content for potential threats. It’s up to the task. It receives global input from over 155 countries and, working in parallel with Forcepoint ACE, analyzes ...
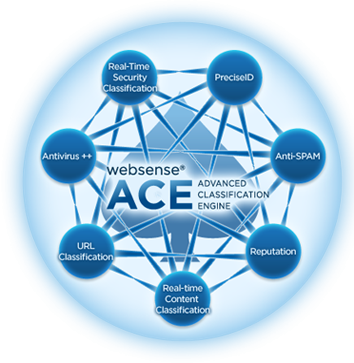
Forcepoint’s Advanced Classification Engine (ACE) delivers optimized threat defenses through deep content inspection of traffic, which is performed in real time. ACE’s eight defense assessment areas enable Forcepoint solutions to protect against emerging ...
Maltego is a platform developed to deliver a clear threat picture to the environment that an organization owns and operates. Maltego’s demonstrates the complexity and severity of single points of failure as well as trust relationships that exist currently ...
VIPRE ThreatIQ gives you the real-time intelligence you need to strengthen your cyber-defense and stop attackers cold. Up-to-the-minute data VIPRE ThreatIQ compiles real-time, global threat intelligence to help you understand where attackers are coming ...
Every day, Shadowserver sends custom remediation reports to more than 7000 vetted subscribers, including over 133 national governments (201 National CSIRTs) covering 175 countries and territories, as well as many Fortune 500 companies. These reports are d ...
DARKBEAST provides incident responders, threat hunters, investigators, and intelligence analysts with a robust technology to dive into the cybercrime underground and investigate through KELA's cybercrime data lake. Gain visibility into underground operati ...