List Categories and Listings by M
Viewer for standalone files containing Microsoft Outlook Express 4,5 and 6 message database (*.idx/*.mbx/*.dbx), Windows Vista Mail/Windows Live Mail and Mozilla Thunderbird message databases as well as standalone EML files. This application is based on ...
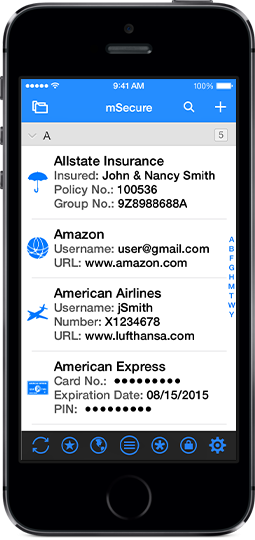
mSecure is a leading password manager and digital wallet. Your data is safe in mSecure because it uses 256bit Blowfish encryption to protect your most personal information, account numbers, usernames, passwords and more! Guard your passwords with confi ...
ModSecurity is an open source, cross-platform web application firewall (WAF) module. Known as the "Swiss Army Knife" of WAFs, it enables web application defenders to gain visibility into HTTP(S) traffic and provides a power rules language and API to imple ...
A free tool that provides a simple, safe and effective mechanism for security teams and administrators to run their own phishing tests inside their organization. Simply install the application on a server or workstation and create a url email/sms/etc. cam ...
Endpoint Central (formerly Desktop Central) is a unified endpoint management and security solution that helps in managing servers, laptops, desktops, smartphones, and tablets from a central location. It's a modern take on desktop management that can be sc ...
The Center for Cybersecurity Education and Leadership at Montreat College provides guidance and oversight to our academic program, to the distribution of cyber defense information, and to collaborative efforts in cybersecurity with an emphasis on combinin ...
Configuration Manager simplifies the complex task of delivering and managing updates to IT systems across the enterprise. Use Configuration Manager to help you with the following systems management activities: Increase IT productivity and effici ...
M-Guard is an XML guard that is used at a network boundary to control traffic. An M-Guard instance is an application level data diode, with traffic flowing in one direction only. Commonly, M-Guard instances will be deployed in pairs, one controlling flow ...
Real-time threat protection - 24/7 protection for everyone’s devices from ever-evolving malware and online threats.Easy to use - Connect all your computers and smartphones and easily manage them from a single dashboard. All products include:Award-winning ...
MDaemon AntiVirus provides the next generation of antivirus and spam protection for the MDaemon Email Server by halting viruses on all inbound and outbound email at the server before it's passed on to the client, providing a shield to stop security troubl ...
MiniStumbler is a tool for Windows CE that allows you to detect Wireless Local Area Networks (WLANs) using 802.11b, 802.11a and 802.11g. It has many uses: * Verify that your network is set up the way you intended. * Find locations with poor co ...
McAfee® Internet Security makes PC and online protection easy for everyone. This set-it-and-forget-it solution comes with award-winning McAfee SiteAdvisor® web security, so you know the safety of web sites before you visit, bank, shop or trade online. Thi ...
Sadly, m0n0wall has reached it's End-of-Life. m0n0wall is a project aimed at creating a complete, embedded firewall software package that, when used together with an embedded PC, provides all the important features of commercial firewall boxes (including ...
Our server is ready to send traffic to your computer. You may select either of two methods. If you would like to simply generate some event traffic on your computer to test the event notification dialog and see some events in the log choose the simple pro ...
Includes file encryption tools that can encrypt with either 3-DES or IDEA.
Maresware: The Suite provides an essential set of tools for investigating computer records plus powerful data analysis capabilities. This bundled suite of over 40 separate, highly-targeted programs gives you the flexibility to accomplish a wide variety of ...
md5deep is a set of programs to compute MD5, SHA-1, SHA-256, Tiger, or Whirlpool message digests on an arbitrary number of files. md5deep is similar to the md5sum program found in the GNU Coreutils package, but has the following additional features: Re ...
mac-robber is a digital investigation tool that collects data from allocated files in a mounted file system. This is useful during incident response when analyzing a live system or when analyzing a dead system in a lab. The data can be used by the mactime ...
Becrypt have worked closely with the UK National Cyber Security Centre (NCSC) to support the enhanced security characteristics of NCSC’s Advanced Mobile Solutions program, resulting in the first MDM platform that can support dynamic Deep Packet Inspection ...
NAP is one of the most desired and highly anticipated features of Microsoft® Windows® Server 2008. NAP is a new platform and solution that controls access to network resources based on a client computer’s identity and compliance with corporate governance ...