LogRhythm NDR
Real-time threat detections across endpoints, data centers, and the cloud.
Securing your network against advanced persistent threats (APTs) requires greater visibility to detect actors and their actions so that you can reduce your response time. As threats increase, real-time network detection and response (NDR) solutions are more critical than ever.
While other NDR solutions rely solely on machine learning (ML) based threat detection, LogRhythm uses hybrid analytics that combine machine learning, rules-based detection, and threat intelligence to analyze network, user, and host activity. This holistic approach provides a true representation of all activity within the enterprise domain, making it possible to detect lateral movement, exfiltration, malware compromise, ransomware, and other threats in real time.
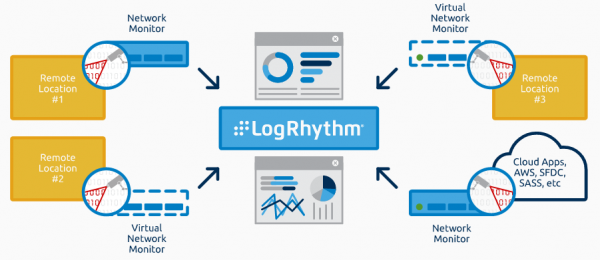
LogRhythm NDR helps you address new security use cases for desktops, supply chains, data centers, public cloud, and IoT/OT. You can use the SaaS-based threat detection solution alone or with the LogRhythm SIEM Platform to quickly spot threats and minimize your organization’s risk.
Powered by patent-pending TensorMist-AI™ technology, LogRhythm NDR uses mesh computing to scale data collection and analytics and lower operating costs. Key features of LogRhythm NDR include:
- Real-time detection of actors and actions - Provides end-to-end enterprise activity at the network, host, user, and process level to help you detect threats like lateral movement, exfiltration, malware compromise, and ransomware in real time.
- Integration with extended detection and response (EDR) and firewall solutions - Adds network visibility to your existing threat detection to extend coverage across endpoints, data centers, and the cloud.
- Agentless cloud collection - Ingests cloud data and models OS and workload behaviors across virtual machine and Kubernetes/containerized environments.
- TensorMist-AI - Uses mesh computing to scale data collection and analytics and lower bandwidth costs.
- Comprehensive and accurate threat detection - Reduces false positives by over 90% and blocks advanced attacks.
- Built-in MITRE ATT&CK Engine - Provides smart threat hunting of tactics, techniques, and threat groups across multiple attack vectors.
- Easy deployment - Getting up and running is easy with our cloud-native security stack and out-of-the-box integrations for existing firewall and EDR solutions.