List Categories and Listings by A
Avast! Mobile security protects your device from viruses, amlware, adware and spyware. it can also help you locate your lost phone through its web-based phone locate feature. The antivirus engine scans installed apps, memory card content, and new apps au ...
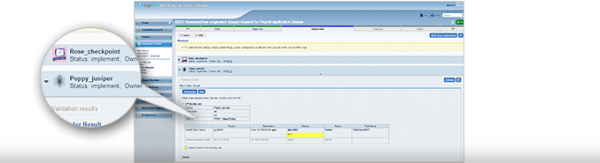
AlgoSec FireFlow automates the entire security policy change workflow – from submission and design to risk analysis, implementation, validation and audit - enabling security and operations teams to: Reduce the time required to process firewall changes ...
Avira Free Antivirus 2015 protects against viruses, malware, and phishing, and the new Dropbox partnership offers secure syncing for your data. In security tests, Avira's latest update continues to deliver top-tier protection.
The Annual Computer Security Applications Conference (ACSAC) is an internationally recognized forum where practitioners, researchers, and developers in information and system security meet to learn and to exchange practical ideas and experiences. If you a ...
AppWall - Radware’s Web Application Firewall (WAF), ensures delivery of mission-critical Web applications and APIs for corporate networks and in the cloud. AppWall is a WAF that combines positive and negative security models to provide complete protection ...
Access Assurance Suite is an intelligent identity and access management (IAM) software solution that enables organizations to deliver informed provisioning, meet ongoing regulatory compliance, and leverage actionable analytics for improved identity govern ...
AlertBoot offers a cost-effective, web-based secure disk encryption service for companies of any size who want highly scalable, easy-to-deploy hard disk encryption, USB encryption and laptop data security. Centrally managed via the Internet, AlertBoot is ...
Virtual Intranet Agent (VIA) - VIA is a software agent for Windows platforms that you can think of effectively as a software RAP for laptops. Once installed, it just disappears into the background and engages itself when needed. If the user is in the offi ...
Built to protect your PC, and your online life Malware protectionStops viruses, spyware, and malware with six powerful layers of protection Email ShieldBlocks dangerous email attachments and phishing links that could steal your data Real-time updatesUp ...
AVG Internet Security blocks viruses and malware, keeps your emails secure, protects your personal files, passwords, and webcam from hackers, and lets you shop and bank online without worry. Advanced Antivirus: Scans your PC for viruses, ransomware, spyw ...
AVG Internet Security Business Edition * Ultimate endpoint security for your employees’ laptops and PCs * File Server protection to prevent malware from spreading across your network * Email Server protection against spam, phishing and em ...
It is a tool for reengineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making some modifications; it makes possible to debug smali code step by step. Also it makes working with app eas ...
Malware protection for Windows and Mac. Advanced detection system for preventing novel ransomware and zero-day exploitsComplete web protection for safe online shopping and bankingEnhanced performance to keep your system fast and optimized Web protection ...
AIR is a GUI front-end to dd/dc3dd designed for easily creating forensic images. by Steve Gibson and Nanni Bassetti Features: * auto-detection of IDE and SCSI drives, CD-ROMs, and tape drives * choice of using either dd or dc3dd (Note: dc3d ...
Autopsy is a digital forensics platform and graphical interface to The Sleuth Kit® and other digital forensics tools. It is used by law enforcement, military, and corporate examiners to investigate what happened on a computer. You can even use it to recov ...
3 years Full Time
Android Antivirus Once installed, it runs silently to protect you from the latest viruses, malware, spyware, unsafe apps and settings, and other nasty threats. Anti-Theft Phone Tracker Just visit our Anti-Theft website from another de ...
A.R.E, the Android Reverse Engineering Virtual Machine. This VirtualBox-ready VM includes the latest Android malware analysis tools as follows: * Androguard * Android sdk/ndk * APKInspector * Apktool * Axmlprinter * Ded * Dex2jar * DroidBox * Ja ...
A powerful tool for analyzers to analyze the Android malware samples manually. The important features of our tool are listed as follows: (1) Graph-based UI displaying control flow of the code. (2) Links from graph view to source view. (3) Func ...
Androguard (Android Guard) is a tool written in python to play with : .class (Java virtual machine) .dex (Dalvik virtual machine) APK (Android application) JAR (Java application) Android's binary xml Androguard has the following ...