List Categories and Listings by T
The fully assembled and enclosed brother to the Throwing Star LAN Tap Kit. The pro model sports all of the same 10BASET and 100BASETX monitoring goodness ready to go in your kit bag, no soldering necessary. To a target network this little guy looks just ...
The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database. This tool is intended to help Penetration tester ...
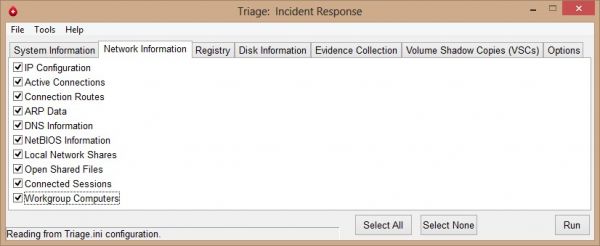
Triage-IR is a script written by Michael Ahrendt, which will collect system information, network information, registry hives, disk information and will also dump memory. One of the capabilities of Triage-IR is collecting information from Volume Shadow Cop ...
The weakest link in most systems is invariably the human element. How do you ensure that confidential files do not get uploaded to the cloud?, how can you tell if a disgruntled employee is carrying out malicious activities which compromise the integrity o ...
Tcpflow is a program that captures data transmitted as part of TCP connections (flows), and stores the data in a way that is convenient for protocol analysis and debugging. Each TCP flow is stored in its own file. Thus, the typical TCP flow will be stored ...
ThreatSim attack simulation product provides a phishing-focused security awareness training program. The ThreatSim mock attack system allows you to deliver simulated phishing emails with embedded Teachable Moments, which display targeted "just-in-time tea ...
Get complete data security - Empower the enterprise to discover, monitor, and protect sensitive data, centralize management and reporting, and synchronize on-premises and cloud policies. Secure data wherever it resides - Protect business-critical informa ...
TetherFilter Anti-Spam and Anti-Virus Appliance Solutions. Tethernet’s TetherFilter offers a complete anti spam and anti-virus solution in an easy to deploy appliance. With accurate anti-spam technology, near-zero administration and simple deployment Tet ...
Web Application Firewall & Intrusion Prevention Software for Microsoft IISServer 2016/2019/IIS 10 Support ThreatSentry combines a state-of-the-art Web Application Firewall and port-level firewall with advanced behavioral filtering to block unwanted I ...
The Tenable Passive Vulnerability Scanner (PVS) can find out what is happening on your network without actively scanning it. Each PVS monitors your network for vulnerable systems, watches for potential application compromises, client and server trust rela ...
If you have a large network, the Security Center can be used to place multiple Nessus scanners throughout your infrastructure. Using multiple scanners decreases your scan time, but also has several other advantages. The Security Center can help any org ...
tiger is a set of scripts that scan a Un*x system looking for security problems, in the same fashion as Dan Farmer's COPS. 'tiger' was originally developed to provide a check of UNIX systems on the A&M campus that want to be accessed from off campus (clea ...
TheGreenBow VPN Client is an on demand IPSec VPN Client, compliant with most of popular VPN gateways with network tools to deploy security in large and medium Enterprises. Highly efficient and easy to configure, the VPN Client also allows peer-to-peer VPN ...
Tectia SSH Features Tectia SSH supports FIPS 140-2 certified cryptography Professional support & maintenance, including 24x7 support for business-critical applications Support for business platforms (Windows, Unix/Linux, IBM z/OS Mainframes) Integra ...
TrustWay® VPN Appliance: reliable solutions for corporate network security The benefits * An EAL2+ Common Criteria certified solution that is DCSSI approved * A range suited to all types of network infrastructure * High performance ...
We Resell This Product
If you're looking for a free firewall test, you have come to the right place. Our computer security test is designed to scan your firewall and security software for vulnerabilities. It takes less than a minute to run our all-in-one spyware removal test. ...
Tracks Eraser Pro is designed to protect you by cleaning up all the tracks of Internet activities on your computer. With only one click, Tracks Eraser allows you to erase the cache, cookies, history, typed URLs, autocomplete memory, index.dat from your br ...
TCT is a collection of programs by Dan Farmer and Wietse Venema for a post-mortem analysis of a UNIX system after break-in. The software was presented first in a Computer Forensics Analysis class in August 1999 (handouts can be found here). Examples of us ...
Tripwire File Integrity Monitoring (FIM) has the unique, built-in capability to reduce noise by providing multiple ways of determining low-risk change from high-risk change as part of assessing, prioritizing and reconciling detected change. Auto-promoting ...