List Categories and Listings by A
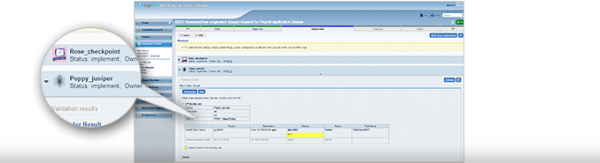
AlgoSec FireFlow automates the entire security policy change workflow – from submission and design to risk analysis, implementation, validation and audit - enabling security and operations teams to: Reduce the time required to process firewall changes ...
Avast! Mobile security protects your device from viruses, amlware, adware and spyware. it can also help you locate your lost phone through its web-based phone locate feature. The antivirus engine scans installed apps, memory card content, and new apps au ...
AlienVault USM is an all-in-one platofrm designed and priced to ensure that mid-market organisations can effectively defend themselves against todays' advanced threats. The AlienVault (USM) platform provides five security capabilities in a single console ...
ADD is a physical memory anti-analysis tool designed to pollute memory with fake artifacts. This tool was first presented at Shmoocon 2014. Please note that this is a proof of concept tool. It forges OS objects in memory (poorly). It would be easy (very e ...
The ANXTunnelz service combines the in-house IPSec expertise of ANX with a standardized hardware offering that eliminates the complexity and resource constraints related to the issue of network interoperability. Some of the features of the ANXTunnelz ser ...
The International Conference on Availability, Reliability and Security will bring together researchers and practitioners in the area of dependability. This conference highlights the various aspects of dependability - with special focus on the crucial link ...
AppSentry is a new generation of security scanner and vulnerability assessment tool. Unlike other security scanners, AppSentry knows the application it is validating – its technology and data model. The security audits and checks are written specifically ...
Protect your business Endpoints today against ransomware, malware, hackers and much more. Features: CyberCapture - When an unrecognized file is downloaded onto one of your PCs, a copy will be sent to our experts at our Threat Labs to identify if it’s ...
Easy-to-use business protection with features specific to Windows servers. Don’t overlook protecting your infrastructure - securing Windows servers is a vital part of comprehensive cybersecurity for businesses that use them. Keep your network protected, ...
AVG File Server Business Edition's network virus scanner helps keep your customer and business data safe from hackers and malware: hassle and worry you just don't need. Hackers and malware can sneak in and disrupt your operations, costing you time and mon ...
The manual audit of a firewall policy is a very subjective and laborious process which is dependent on the user?s skill set and experience. The AlgoSec Firewall Analyzer (FA) automatically and non-intrusively analyzes a firewall?s policy. Within a matter ...
Firewall Test 1 - If you're new to computer security, then Firewall Test 1 is for you. It checks your system for commonly used ports. It also tests for ports commonly used by Viruses and Trojans. On average, your computer [should not] have any open ports. ...
The AstroFlowGuard security and bandwidth appliance addresses security issues by incorporating a firewall, intrusion detection and prevention system (IDS and IDP), VPN Server, Bandwidth Management, and other security aware features in an easy to use, simp ...
The Fortress product family provides the most robust, scalable and easy-to-manage line of security gateway solutions for ensuring privacy of wireless networks and mission-critical enterprise applications. These FIPS certified security products provide use ...
An international conference focussing on IT security for CFOs, CIOs, CTOs and technical staff from government agencies, universities and industry. Featuring local and international IT security experts.
Array Networks SPX Series?the industry's gold standard for SSL VPN. Engineered from the ground up for high-performance security and access control, the SPX Series delivers blazing fast local and remote network access that supercharges productivity and use ...
AstroFlowGuard is a Linux-based multi-function tool for network engineers - it incorporates all the proven bandwidth management functionality of AstroFlow, but also incorporates a statefull firewall, intrusion detection system and vpn server. With it's us ...
AEP Net: Purpose-designed IP encryption to meet stringent VPN security standards. AEP Net is an independently assured encryptor that protects IP traffic across networks. AEP Net provides both data confidentiality and source authentication for network tra ...
Traditionally, IPSec or SSL VPN concentrators have been deployed to serve remote users, adding both cost and complexity. For organizations that have deployed Aruba's campus or branch solutions, the answer is already there – at no additional cost. ...
Aker Firewall 5.1 provides the implementation of advanced security measures for corporative networks and systems connected to the Internet: Security, Availability, Reliability and Privacy.