Michele M Jordan
The BrightCloud IP Reputation Service helps enterprise customers augment their defenses by adding a dynamic IP reputation service. Through a continuously updated feed of known malicious IP addresses, IT security administrators can easily identify threats ...
The BrightCloud File Reputation Service provides next-generation Webroot threat intelligence by offering customers a dynamic, up-to-the-minute file reputation service to protect their data and assets. This real-time lookup service of known malicious and w ...
The BrightCloud Mobile App Reputation Service helps vendors who provide mobile management and security solutions address the new security vulnerabilities that mobility creates. Powered by the Webroot® Intelligence Network (WIN), the service continuously a ...
The BrightCloud Mobile Security SDK for Android™ and iOS® addresses mobile device vulnerabilities by enabling mobile management partners to offer enhanced security for their customers. It features antivirus, antimalware, device and application interrogati ...
Know and control your network with Easy NAC, the simple and affordable Network Access Control solution. Easy NAC automatically discovers devices, profiles them, and controls access to the network. Easy NAC’s unique technology requires no network changes ...
Mobile security and complexity don’t have to go hand in hand. Check Point Capsule is one seamless solution that addresses all your mobile security needs. Capsule protects your mobile devices from threats, provides a secure business environment for mobile ...
Safend Reporter automatically generates reports on intentional and unintentional misuse of private company information. Reports can be strategic and periodic and built-in or customized by an administrator. Each report is set in a comprehensive interface a ...
Safend Inspector prevents transfer of sensitive company information. As information is processed it is classified and its access permissions and security profile are configured. During data transfer Inspector checks for sensitive information in its c ...
Passwords are weak. Tokens are expensive. Don’t compromise on security or price. Wave Virtual Smart Card does anything your physical smart cards and tokens do, but it starts with hardware you already have: the Trusted Platform Module (TPM), a hardware se ...
PentesterLab is an easy and great way to learn penetration testing. PentesterLab provides vulnerable systems that can be used to test and understand vulnerabilities. Hands-on There is only one way to properly learn web penetration testing: by getting y ...
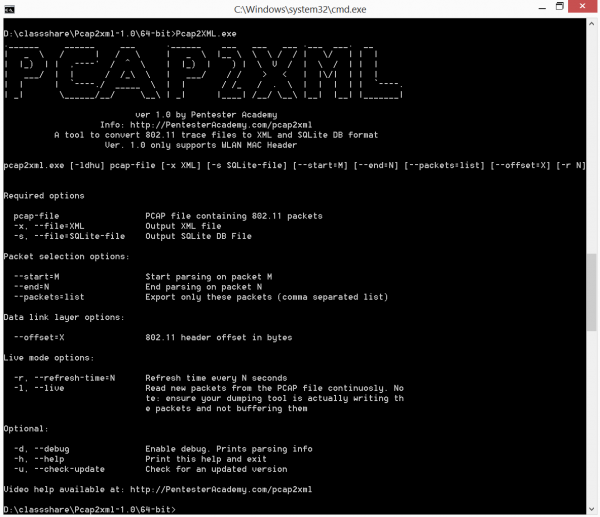
PCAP2XML is a tool suite which takes 802.11 PCAP trace files as input and can convert them into XML or SQLITE representations. This allows a pentester to run arbitrary queries on the packet header fields. Why do we need this? Wireshark is great when it ...
Simple site used to test firewall rules. Select TCP ports, click test, and it will attempt to connect to the target server you specify. Free, but does contain ads in header and footer.
REMnux™ is a free Linux toolkit for assisting malware analysts with reverse-engineering malicious software. It strives to make it easier for forensic investigators and incident responders to start using the variety of freely-available tools that can exami ...
This popular course explores malware analysis tools and techniques in depth. FOR610 training has helped forensic investigators, incident responders, security engineers, and IT administrators acquire the practical skills to examine malicious programs that ...
SourceMeter is an innovative tool built for the precise static source code analysis of C/C++, Java, C#, Python, and RPG projects. This tool makes it possible to find the weak spots of a system under development from the source code only, without the need ...
Extensive threat visibilityKroll Responder provides extensive threat visibility across on-premises, cloud and hybrid environments, 24/7. Continual detection of attacksKroll Responder leverages the latest security tools and threat intelligence to ensure y ...
DB Audit and Security 360 is a complete out-of-the-box database security & auditing solution for Oracle, Sybase, MySQL, DB2 and MS SQL Server. DB Audit allows database and system administrators, security administrators, auditors and operators to track and ...
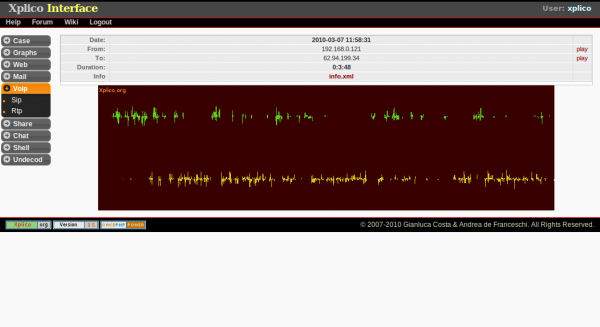
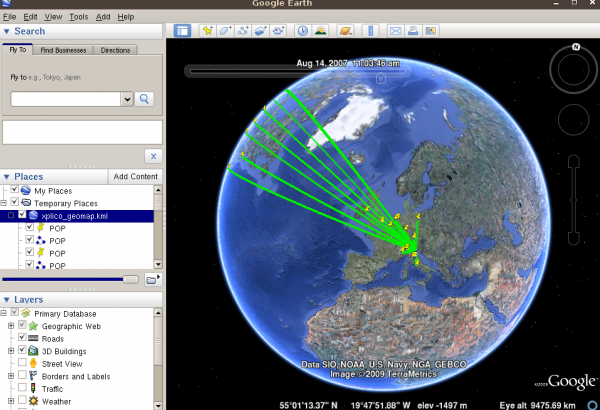
The goal of Xplico is extract from an internet traffic capture the applications data contained. For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on. Xplico ...
ImmuniWeb - Web Penetration Testing. ImmuniWeb is a web application security and penetration testing service from High-Tech Bridge. It combines managed vulnerability scanning with manual penetration testing.
The Certificate in Information Security Management Principles (CISMP) is an internationally recognised qualification which was developed by the British Computer Society and provides a requisite foundation of knowledge necessary for individuals new to the ...