Michele M Jordan
Passwords are weak. Tokens are expensive. Don’t compromise on security or price. Wave Virtual Smart Card does anything your physical smart cards and tokens do, but it starts with hardware you already have: the Trusted Platform Module (TPM), a hardware se ...
PentesterLab is an easy and great way to learn penetration testing. PentesterLab provides vulnerable systems that can be used to test and understand vulnerabilities. Hands-on There is only one way to properly learn web penetration testing: by getting y ...
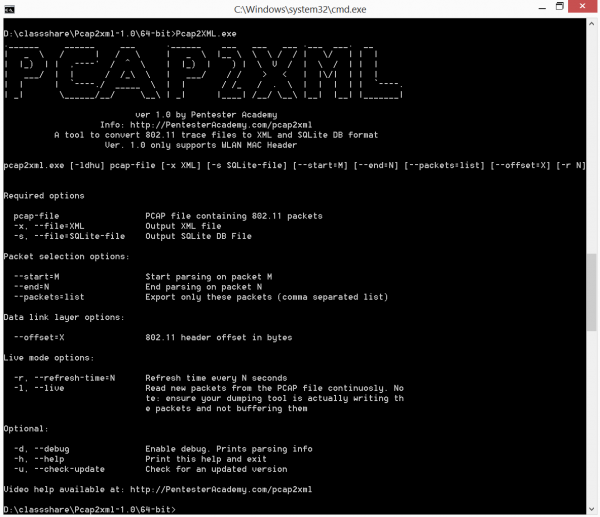
PCAP2XML is a tool suite which takes 802.11 PCAP trace files as input and can convert them into XML or SQLITE representations. This allows a pentester to run arbitrary queries on the packet header fields. Why do we need this? Wireshark is great when it ...
Use this service to test your firewall rules. If you intend to allow or deny connections through your firewall, you can check to see what will happen when an Internet user attempts to connect. Behind the scenes, this firewall test uses NMap to attempt to ...
REMnux™ is a free Linux toolkit for assisting malware analysts with reverse-engineering malicious software. It strives to make it easier for forensic investigators and incident responders to start using the variety of freely-available tools that can exami ...
This popular course explores malware analysis tools and techniques in depth. FOR610 training has helped forensic investigators, incident responders, security engineers, and IT administrators acquire the practical skills to examine malicious programs that ...
SourceMeter is an innovative tool built for the precise static source code analysis of C/C++, Java, C#, Python, and RPG projects. This tool makes it possible to find the weak spots of a system under development from the source code only, without the need ...
Pompem is an open source tool, which is designed to automate the search for exploits in major databases. Developed in Python, has a system of advanced search, thus facilitating the work of pentesters and ethical hackers. In its current version, performs s ...
Arkime (formerly Moloch) is an open source, large scale, full packet capturing, indexing and database system. A simple web interface is provided for PCAP browsing, searching, and exporting. APIs are exposed that allow PCAP data and JSON-formatted ses ...
Tcpflow is a program that captures data transmitted as part of TCP connections (flows), and stores the data in a way that is convenient for protocol analysis and debugging. Each TCP flow is stored in its own file. Thus, the typical TCP flow will be stored ...
Intrusion Prevention System (IPS) for ssh (default port 22), this IPS responds to the suspicious activity by setting the linux firewall (iptables) to block network traffic from the suspected malicious source. Suspicious activity is determined via auth or ...
ntopng is the next generation version of the original ntop, a network traffic probe that shows the network usage, similar to what the popular top Unix command does. ntopng is based on libpcap and it has been written in a portable way in order to virtually ...
Sagan is an open source (GNU/GPLv2) high performance, real-time log analysis & correlation engine that run under *nix operating systems (Linux/FreeBSD/OpenBSD/etc). It is written in C and uses a multi-threaded architecture to deliver high performance log ...
A tool to collect DNS records passively to aid Incident handling, Network Security Monitoring (NSM) and general digital forensics. PassiveDNS sniffs traffic from an interface or reads a pcap-file and outputs the DNS-server answers to a log file. Passive ...
ngrep strives to provide most of GNU grep's common features, applying them to the network layer. ngrep is a pcap-aware tool that will allow you to specify extended regular or hexadecimal expressions to match against data payloads of packets. It currently ...
Justniffer is a network protocol analyzer that captures network traffic and produces logs in a customized way, it can emulate Apache web server log files, track response times and extract all "intercepted" files from the HTTP traffic. It lets you interac ...
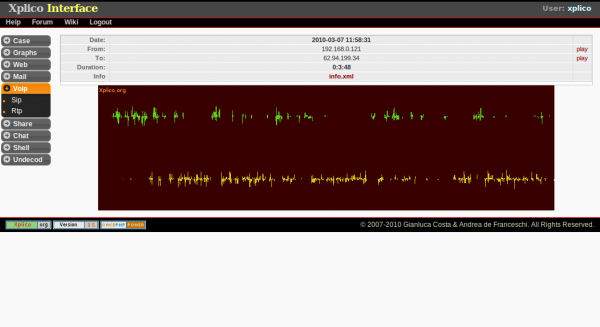
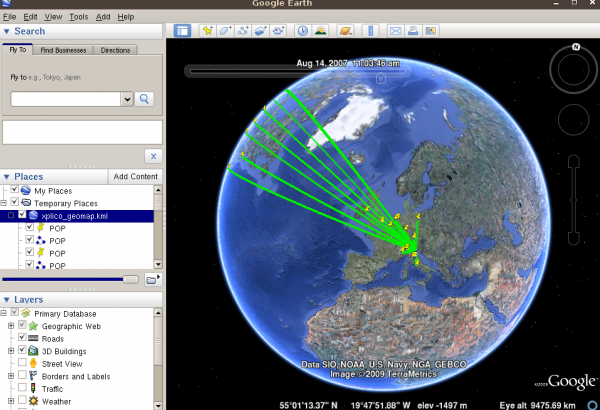
The goal of Xplico is extract from an internet traffic capture the applications data contained. For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on. Xplico ...
ImmuniWeb - Web Penetration Testing. ImmuniWeb is a web application security and penetration testing service from High-Tech Bridge. It combines managed vulnerability scanning with manual penetration testing.
The Certificate in Information Security Management Principles (CISMP) is an internationally recognised qualification which was developed by the British Computer Society and provides a requisite foundation of knowledge necessary for individuals new to the ...
DB Audit and Security 360 is a complete out-of-the-box database security & auditing solution for Oracle, Sybase, MySQL, DB2 and MS SQL Server. DB Audit allows database and system administrators, security administrators, auditors and operators to track and ...
Page 17 of 56