Michele M Jordan
Guarantee your data has been erased from any type of?drive in?desktop/laptop computers, servers and storage environments. Blancco’s secure erasure methods ensure data is written across the full logical capacity of the drive (and not just compressed). &nb ...
Blancco Mobile is designed to securely erase your smartphone’s internal and external memory. Restoring factory settings does not ensure that data is permanently destroyed, because your data can still be recovered afterwards. With Blancco Mobile, all user ...
Comodo Antispam Gateway (CASG) is cloud based SaaS which prevents junk mail from ever entering your mail server, and its employee inboxes. It is able to filter virus, phishing, malware and harvesting spam attacks. Being cloud based makes it ideally suite ...
Our wireless internet security service creates a shield around your laptop, desktop or handheld. This prevents criminals from attacking or scanning the system from the local network that you're using to connect to the Internet. It also encrypts all traffi ...
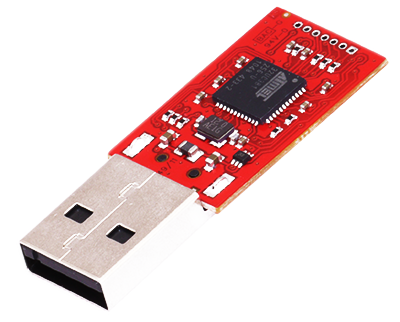
'Since 2010 the USB Rubber Ducky has been a favorite among hackers, penetration testers and IT professionals. With origins as a humble IT automation proof-of-concept using an embedded dev-board, it has grown into a full fledged commercial Keystroke I ...
The WiFi Pineapple is a unique device developed by Hak5 for the purpose of WiFi auditing and penetration testing. Since 2008 the WiFi Pineapple has grown to encompass the best rogue access point features, unique purpose-built hardware, intuitive web inter ...
The fully assembled and enclosed brother to the Throwing Star LAN Tap Kit. The pro model sports all of the same 10BASET and 100BASETX monitoring goodness ready to go in your kit bag, no soldering necessary. To a target network this little guy looks just ...
Hacker Guardian PCI Compliance Scanning is designed for Website owners and E-commerce Merchants to secure transactions, in accordance with PCI Standards. HackerGuardian PCI Scanning is a vulnerability assessment scanning solution designed to achieve and ...
Elcomsoft Phone Password Breaker enables forensic access to password-protected backups for smartphones and portable devices based on RIM BlackBerry and Apple iOS platforms. The password recovery tool supports all Blackberry smartphones as well as Apple de ...
Perform full file system and logical acquisition of iPhone, iPad and iPod Touch devices. Image device file system, extract device secrets (passwords, encryption keys and protected data) and decrypt the file system image. Features and Benefits: ...
Perform the complete forensic analysis of encrypted disks and volumes protected with desktop and portable versions of BitLocker, PGP and TrueCrypt. Elcomsoft Forensic Disk Decryptor allows decrypting data from encrypted containers or mounting encrypted vo ...
Elcomsoft Wireless Security Auditor examines the security of your wireless network by attempting to break into the network from outside or inside. Elcomsoft Wireless Security Auditor works completely in off-line, undetectable by the Wi-Fi network being pr ...
Avast! Mobile security protects your device from viruses, amlware, adware and spyware. it can also help you locate your lost phone through its web-based phone locate feature. The antivirus engine scans installed apps, memory card content, and new apps au ...
The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database. This tool is intended to help Penetration tester ...
FOR572: Advanced Network Forensics and Analysis, was built from the ground up to cover the most critical skills needed to mount efficient and effective post-incident response investigations. It focuses on the knowledge necessary to expand the forensic min ...
Oxygen Forensic Extractor offers OEM system builders and hardware manufacturers a unique opportunity to integrate a time-proven forensic acquisition system to their hardware-based solution without spending years developing in-house software. Oxygen Forens ...
Oxygen Forensic Extractor for Clouds is a forensic program that allows to extract data from cloud services and save it on PC in a readable format. Authentication is required to get access to the cloud data. A forensic expert needs to enter account credent ...
This course will teach you Python scripting and its application to problems in computer and network security. This course is ideal for penetration testers, security enthusiasts and network administrators who want to learn to automate tasks or go beyond ju ...
The SecurityTube Linux Assembly Expert, or SLAE, is an online course and certification which focuses on teaching teh basics of 32-bit assembly language for the Intel Architecture (IA-32) family of processors of the Linux platform and applying it to infose ...
The SecurityTube iOS Security Expert, or SISE, is an online course and certification which focuses on the iOS platform and application security. This course is ideal for pentesters, researchers and the casual iOS enthusiast who would like to dive de ...
Page 47 of 56