Michele M Jordan
The Palo Alto Networks VM-Series comprises three virtualized next-generation firewall models – VM-100, VM-200, and VM-300, supported on VMware ESXi 4.1 and ESXi 5.0 platforms. 2, 4 or 8 CPU cores on the virtualized server platforms can be assign ...
Every second of the day, the Forcepoint ThreatSeeker Intelligence scours the vast expanse of online content for potential threats. It’s up to the task. It receives global input from over 155 countries and, working in parallel with Forcepoint ACE, analyzes ...
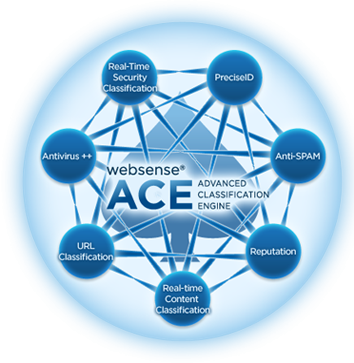
Forcepoint’s Advanced Classification Engine (ACE) delivers optimized threat defenses through deep content inspection of traffic, which is performed in real time. ACE’s eight defense assessment areas enable Forcepoint solutions to protect against emerging ...
This product controls network management traffic as it passes between the enterprise networks and the management system. Its self-defending architecture means it can exert the required control without itself becoming vulnerable to attack. Feature ...
Web Guard is an HTTP(s), ICAP and Deep Secure File Sharing (DSFSP) proxy. It uses policy-based rules to detect threats and enforce compliance, accountability and brand protection on Web downloads and uploads as well as Webmail attachments and cross domain ...
This product controls web traffic entering and leaving the organisation, defending against advanced attacks and misuse. It is increasingly used by organisations that need to tightly control Internet browsing traffic or need to use web protocols to transfe ...
WANGUARD is a professional commercial software for IP traffic monitoring and accounting, traffic anomalies detection and DDoS mitigation. It contains a network traffic analyzer and collector that supports NetFlow, sFlow, IPFIX, IPv6 and Port Mirroring. It ...
A professional commercial software that provides in-depth IP traffic analysis, traffic accounting and bandwidth monitoring. It contains a network traffic analyzer and collector that supports NetFlow, sFlow, IPFIX, IPv6 and Port Mirroring. It provides cust ...
Lawfully access locked devices with easeBypass pattern, password or PIN locks and overcome encryption challenges quickly on popular Android and iOS devices Support for the broadest range of devicesCollect data from mobile phones, drones, SIM Cards, SD ca ...
Forensic Explorer analysis software. Suitable for new or experienced investigators, Forensic Explorer combines a flexible and easy to use GUI with advanced sort, filter, keyword search, data recovery and script technology. Quickly process large volumes o ...
McAfee Policy Auditor helps you report consistently and accurately against key industry mandates and internal policies across your infrastructure or on specific targeted systems. Policy Auditor is an agent-based IT audit solution that leverages the Securi ...
Trellix Email Security – Server leads the industry in identifying, isolating, and immediately stopping URL and attachment-based attacks, before they enter an organization’s environment. Email Security - Server provides real-time detection and preve ...
McAfee VirusScan Enterprise combines anti-virus, anti-spyware, firewall, and intrusion prevention technologies to stop and remove malicious software. It also extends coverage to new security risks and reduces the cost of responding to outbreaks with low i ...
CrowdStrike Falcon is a Big Data Active Defense platform focused on raising the adversaries' costs and giving the strategic advantage back to defenders. Designed to continuously monitor, share, and mitigate the adversary's Tactics, Techniques, and Pr ...
UMRA is a complete User Management System that simplifies Active Directory Management across all your systems. While managing user account and authorization processes in Active Directory and adjacent systems, UMRA also offers delegation of user account ma ...
McAfee Application Control software provides an effective way to block unauthorized applications and code on servers, corporate desktops, and fixed-function devices. This centrally managed whitelisting solution uses a dynamic trust model and innovative se ...
Trellix Endpoint Security provides your prioritized security needs—from preventing threats and hunting them to tailoring security controls. Machine learning to identify and prevent new malwareMachine-learning behavior classification detects zero-day thre ...
McAfee Total Protection for Data Loss Prevention (DLP) safeguards intellectual property and ensures compliance by protecting sensitive data wherever it lives — on premise, in the cloud, or at the endpoints. McAfee DLP is delivered through low-maintenance ...
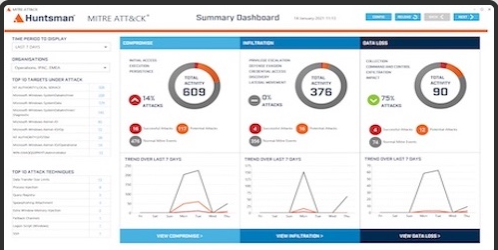
An ‘Always On’ Cyber Security Analytics Tool that deploys from a single SOC platform managed by your team. DEFENCE-GRADE CYBER SECURITY for all organisation types and sizesLIVE MITRE ATT&CK THREAT HEATMAP with easy to access alerts and reportingRESPO ...
IPS Visio Stencils Popular
Stencils for many popular IPS products, including Nitro SIEM (McAfee ESM), Palo Alto Intrusion Prevention, Enterasys (Dragon) Intrusion Prevention, SourceFire, TippingPoint, Juniper, IBM, Cisco, McAfee Intrushield M-Series, and Fortinet. Also other generi ...
Page 44 of 57