Directory: Random Listings
3 years Full Time
Nortel?s VPN Gateway portfolio is a remote access security solution that extends the reach of enterprise applications to remote employees, partners, and customers. By leveraging the native capability of widely deployed SSL enabled Web browsers, while also ...
HIBUN Data Encryption encrypts data on hard drive, removable media, and file server to protect the secrecy of the information.
The WPScan CLI tool is a free, for non-commercial use, black box WordPress security scanner written for security professionals and blog maintainers to test the security of their sites.
AIR is a GUI front-end to dd/dc3dd designed for easily creating forensic images. by Steve Gibson and Nanni Bassetti Features: * auto-detection of IDE and SCSI drives, CD-ROMs, and tape drives * choice of using either dd or dc3dd (Note: dc3d ...
Webroot Business Endpoint Protection helps businesses keep critical systems, intellectual property, customer data, employees and guests safe from ransomware, phishing, malware and other cyberattacks. Stop sophisticated cyberattacks Next-generation pro ...
Strong security starts with a malware-free device. Two eyes are better than one – Emsisoft has combined two powerful antivirus technologies into one lightning-fast scanner. Designed to be as efficient as possible, this dual-engine scanner allows you to de ...
Bluesnarfer will download the phonebook of any mobile device vulnerable to bluesnarfing.
Unleash the power of your SOC with the LogRhythm NextGen SIEM Platform Detect threats earlier and fasterWhen it comes to stopping threats, seconds matter. That’s why we built our NextGen SIEM platform for speed. You’ll quickly identify threats, automate ...
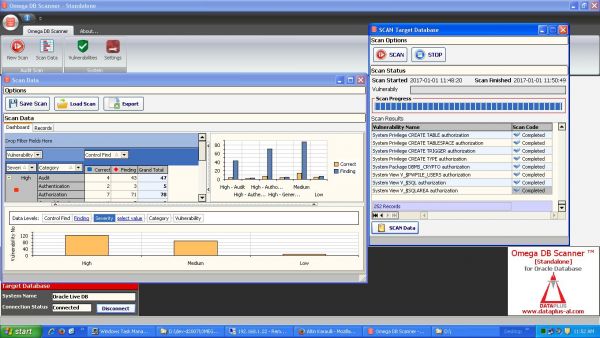
Omega DB Security Reporter is a security auditing and software-only solution for Oracle Databases. Implementing quick reporting, visualisation and documentation of the security posture of the Oracle database on the following security areas: System Priv ...
3 years Full Time
Welcome to the home of POC. POC is organized by Korean hackers & security experts. It is an international security & hacking conference in Korea. POC concentrates on technical and creative discussion and shows real hacking and security. POC wears both bla ...
SpamSentinel has been stopping spam and viruses natively on Domino servers since 2003. Our motto "It just works." Included also, InboxGenius and MacroKiller The InboxGeniusSpamSentinel comes with our proprietary Inbox Genius built-in, which learns from w ...
Continually tracking your network’s endpoints, Safend Auditor silently pinpoints all usage of USB, FireWire, PCMCIA, PCI, internal storage and WiFi connections. Displaying complex information comprehensively, Auditor reports can be exported and manipulat ...
For phishing, SET allows for sending spear-phishing emails as well as running mass mailer campaigns, as well as some more advanced options, such as flagging your message with high importance and adding list of target emails from a file. SET is Python base ...
The Practitioner level Certificate in Information Risk Management (PCIIRM) is aimed at information security and information assurance professionals. The qualification covers the core concepts of Information Risk in a hands-on approach which will require ...
DirX Identity offers an extensive identity management solution for enterprises and organizations. It gives the right people the right access to the right resources at the right time and thus leads to productivity, information security, a perceptible reduc ...
Check Point endpoint security includes data security, network security, advanced threat prevention, forensics, endpoint detection and response (EDR), and remote access VPN solutions. To offer simple and flexible security administration, Check Point’s enti ...
Trend Micro Internet Security provides smart, up-to-date protection for your home network against present and future threats without slowing down your PC. Surf the web without worry Smart security features in Trend Micro Internet Security protect the comp ...
A content filter monitors the use of a computer. With the help of content filter software, you decide which websites can and cannot be accessed, or which applications can be run. Content filters are popular with parents who want to make sure that their ch ...