Directory: A-Z
Powerful security for your online world, with convenience. 1 platform, 3 products to choose from. Whether you need to make managing your passwords a no-brainer, or share files securely with your team members, or keep hackers out of your life, we can make ...
Real-time threat detections across endpoints, data centers, and the cloud. Securing your network against advanced persistent threats (APTs) requires greater visibility to detect actors and their actions so that you can reduce your response time. As threa ...
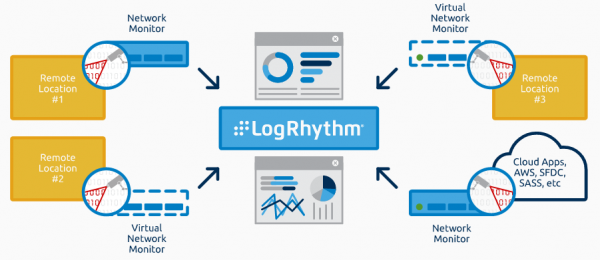
Unleash the power of your SOC with the LogRhythm NextGen SIEM Platform Detect threats earlier and fasterWhen it comes to stopping threats, seconds matter. That’s why we built our NextGen SIEM platform for speed. You’ll quickly identify threats, automate ...
Logsurfer is a program for monitoring system logs in real-time, and reporting on the occurrence of events. It is similar to the well-known swatch program on which it is based, but offers a number of advanced features which swatch does not support. Logsur ...
The Look'n'Stop personal firewall blocks intrusion threats and makes your PC invisible to anyone on the Internet. Look 'n' Stop Firewall provides key features to protect your computer against cyber threats. It prevents malicious programs from transmittin ...
A web application penetration testing tool that can extract data from SQL Server, MySQL, DB2, Oracle, Sybase, Informix, and Postgres. Further, it can crawl a website as a vulnerability scanner looking for sql injection vulnerabilities. Features ...
Application vulnerability mitigation is the next wave of cybersecurity. By analyzing source code, AVM systems are able to scan for, identify, and automatically mitigate application vulnerabilities. This process dramatically increases the security threshol ...
Hackerproof - The LuciGate Firewall is a piece of dedicated hardware (sometimes referred to as a Firewall Appliance) that sits between your network and the outside world. Without its smartcard key, it will not allow ANY data to pass through it. It is not ...
Hackerproof - The LuciGate Firewall is a piece of dedicated hardware (sometimes referred to as a Firewall Appliance) that sits between your network and the outside world. Without its smartcard key, it will not allow ANY data to pass through it. It is not ...
The LUCY Social Engineering Suite and Malware Testing Suite (or CYBERSECURITY CRASH TEST DUMMY) facilitate multiple application areas. They can be used for: – People testing and education – Technology assessments – An inoffensive penetration test sho ...
LutelWall (formerly known as Lutel Firewall) is high-level linux firewall configuration tool. It uses human-readable and easy to understand configuration to set up Netfilter in most secure way. Its flexibility allows firewall admins build from very simple ...
M-Guard is an XML guard that is used at a network boundary to control traffic. An M-Guard instance is an application level data diode, with traffic flowing in one direction only. Commonly, M-Guard instances will be deployed in pairs, one controlling flow ...
The main target of M-ICE are hostbased ID Systems but it is also possible to interoperate with other IDS architectures as long as they use the open and standarized message format IDMEF. The main goal of M-ICE is to fit for every infrastructure and to be h ...
Mailbox Filter is the only spam filter that automatically learns to think like you -- not for you -- about your email. Unlike spam blockers, Mailbox Filter is a "SMART" spam filter so it won't lose your important email. Our exclusive Smart Filter Technolo ...
Sadly, m0n0wall has reached it's End-of-Life. m0n0wall is a project aimed at creating a complete, embedded firewall software package that, when used together with an embedded PC, provides all the important features of commercial firewall boxes (including ...
Mac Forensics Training Featured
This forensics training course (3 days) gives delegates a practical understanding of Data structures and potential evidence as produced in Apple Mac OS X environments and Implementing forensic tools on Mac OS X-based file systems. Highlights of this t ...
mac-robber is a digital investigation tool that collects data from allocated files in a mounted file system. This is useful during incident response when analyzing a live system or when analyzing a dead system in a lab. The data can be used by the mactime ...
Viewer for standalone files containing Microsoft Outlook Express 4,5 and 6 message database (*.idx/*.mbx/*.dbx), Windows Vista Mail/Windows Live Mail and Mozilla Thunderbird message databases as well as standalone EML files. This application is based on ...
MailScan is the world's most advanced Real-Time Anti-Virus and Anti-Spam solution for Mail Servers. MailScan safeguards organizations against Virus, Worm, Trojan and many other malware breeds with futuristic and proactive technologies. Employing an array ...
Mailshell Anti-Spam Universal works with most desktop email applications including Outlook Express, Outlook, Netscape Messenger, and Eudora. You choose the filter strength and decide if you want spam put in its own folder, deleted or simply marked so you' ...