Directory: A-Z
FIRST conferences promote worldwide coordination and cooperation among Computer Security Incident Response Teams (CSIRTs). The conference provides a forum for sharing goals, ideas, and information on how to improve global computer security. The five-day e ...
Flawfinder is a simple program that examines C/C++ source code and reports possible security weaknesses (“flaws”) sorted by risk level. It’s very useful for quickly finding and removing at least some potential security problems before a program is widely ...
floppyfw is a router with the advanced firewall-capabilities in Linux that fits on one single floppy disc.
The FlowMon solution delivers the flow-based (NetFlow/IPFIX) monitoring for all organizations and all networks from 10 Mbps to 10 Gbps. It provides the statistics necessary for network monitoring, security, troubleshooting, IP accounting and billing, capa ...
FlowNBA is a complete solution for network monitoring based on NetFlow/IPFIX. Thanks to the used technology it enables complete overview of the network traffic, detailed information about all communications and provides information about who communicates ...
FlowScan analyzes and reports on Internet Protocol (IP) flow data exported by routers. Consisting of Perl scripts and modules, FlowScan binds together (1) a flow collection engine (a patched version of cflowd), (2) a high performance database (Round Robin ...
FOR572: Advanced Network Forensics and Analysis, was built from the ground up to cover the most critical skills needed to mount efficient and effective post-incident response investigations. It focuses on the knowledge necessary to expand the forensic min ...
This popular course explores malware analysis tools and techniques in depth. FOR610 training has helped forensic investigators, incident responders, security engineers, and IT administrators acquire the practical skills to examine malicious programs that ...
Exports to SFlow
One-way data transfer with optical isolation for uncompromising network security & protection Create boundaries between trusted & untrusted networks by creating a physically secure one-way communication channel. Send data from one secure network ...
With Forcepoint Email Security you can: Identify threatsUse deep content inspection to mitigate advanced malware and ransomware threat. Block data theftUse context-aware DLP to detect data exfiltration using optical character recognition (OCR) i ...
Forcepoint Next-Generation Firewall (NGFW) combines fast, flexible networking (SD-WAN and LAN) with industry-leading security to connect and protect people and the data they use throughout diverse, evolving enterprise networks. Forcepoint NGFW provides co ...
The Forcepoint™ Stonesoft Next Generation Firewall meets both demands by integrating application control, sophisticated evasion prevention and an intrusion prevention system (IPS) into a single solution that is cost-effective and easy to deploy. It has a ...
Every second of the day, the Forcepoint ThreatSeeker Intelligence scours the vast expanse of online content for potential threats. It’s up to the task. It receives global input from over 155 countries and, working in parallel with Forcepoint ACE, analyzes ...
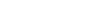
Forcepoint’s Advanced Classification Engine (ACE) delivers optimized threat defenses through deep content inspection of traffic, which is performed in real time. ACE’s eight defense assessment areas enable Forcepoint solutions to protect against emerging ...
Foremost is a console program to recover files based on their headers, footers, and internal data structures. This process is commonly referred to as data carving. Foremost can work on image files, such as those generated by dd, Safeback, Encase, etc, or ...
The first forensic browser able to quickly and easly capture web pages that are to be brought to trial in criminal and civil proceedings. Acquisition of all websitesFAW acquires websites of any type: HTML5, CMS, static, dynamic, with frames, blogs, e-com ...
What Will You Learn? This course will give you an in-depth study of the computer forensics process. Starting from creating evidentiary disk images to recognizing the often-faint trail of unauthorized activity, Foundstone updates this class continuously by ...
3 years Full Time
4 years Sandwich Course