Directory: A-Z
Packed with 49 powerful tools, Engineer’s Toolset delivers the network management, monitoring, and troubleshooting tools you need to easily and effectively manage your infrastructure – all in one extremely affordable package. The toolset includes the SNM ...
Network software with over 60 must-have tools Key Features Automated network discovery Real-time monitoring and alerting Powerful diagnostic capabilities Enhanced network security Integration with SolarWinds NPM solution
Enpass is a secure vault to store everything in one place using a single master password. Secure online shopping Fill your credit cards and banking information automatically on shopping websites, and save yourself from phishing attacks. Password audit ...
When combined with the XSR?s powerful IP routing, the integrated VPN (XSR-XXXX-V PN) dramatically increases the performance and functionality for enterprise networking. The addition of enterprise-class VPN complements the XSR?s industry-leading IP WAN rou ...
The Enterprise Intrusion Analysis course provides students with the skills needed to discover and analyze enterprise intrusions in a UNIX environment. Upon completion of this course, students should be able to: * 1. Detect an enterprise system i ...
The Wireless LAN Security course consists of hands on learning using the latest enterprise wireless LAN security and auditing equipment. This course addresses in detail the most up-to-date WLAN intrusion and DoS tools and techniques, functionality of the ...
Error Prone is a static analysis tool for Java that catches common programming mistakes at compile-time.
eScan Corporate Edition is a comprehensive security solution for your corporate network. The new and improved eScan Corporate Edition (with Hybrid Network Support) safeguards your corporate network from all kinds of cyber threats. As Informatio ...
EtherApe is a graphical network monitor for Unix modeled after etherman. Featuring link layer, IP and TCP modes, it displays network activity graphically. Hosts and links change in size with traffic. Color coded protocols display. It supports Ethernet, F ...
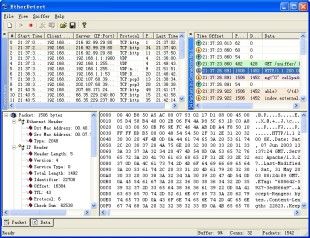
This protocol analyser will Organize captured packets in a connection-oriented view. Capture IP packets on your LAN with nearly no packets losing. Its real-time analyzer enables on-the-fly content viewing while capturing and analyzing, parse and decode an ...
16 months Full Time
4 years Full Time
4 years Sandwich Course
"This four-day course is based on Sun Tzu's principle that knowing one's enemy will strengthen one's defenses and more adequately prepare one for battle. It is better for us to find the vulnerabilities in our systems ourselves and fix them, before th ...
This boot camp teaches you how to use the tools and techniques used by cybercriminals to perform an ethical hack on your organization. You’ll learn ethical hacking methodologies and gain hands-on hacking experience in our cloud-hosted cyber range, i ...
Discover vulnerabilities before cybercriminals do! Our most popular information security and hacking training goes in-depth into the techniques used by malicious actors with attention-getting lectures and hands-on labs. Earn your CEH and PenTest+, guaran ...
4 Years
SecureLogix delivers the world?s first Voice Firewall to secure corporate resources from telephony borne attacks and security risks, and defend your VoIP and legacy voice systems from service disruption and abuse, unauthorized access, toll fraud, and othe ...
Passive scanning of the LAN: you can retrieve info about: hosts in the lan, open ports, services version, type of the host (gateway, router or simple host) and estimated distance in hops.
The theme of the conference is the protection of computer networks. The conference will draw participants from academia and industry in Europe and beyond to discuss hot topics in applied network and systems security. Topics include but are not limited to ...