Michele M Jordan
3 day hands-on journey into the hacking mindset, including the CSTA certification exam. Practically apply the tools and techniques that penetration testers use. The course is ideal for network administrators, security officers & crime prevention ...
CWSA Wireless Security: Hands-On Featured
2 day wireless security training course followed by CSWA certification exam (optional). The course follows the evolution of wireless security, teaching the underlying principles so that delegates leave not only with an understanding of the ...
Mac Forensics Training Featured
This forensics training course (3 days) gives delegates a practical understanding of Data structures and potential evidence as produced in Apple Mac OS X environments and Implementing forensic tools on Mac OS X-based file systems. Highlights of this t ...
4 day highly practical course designed to equip information security specialists with the knowledge and skills to deal effectively with incident response situations. It also gives investigators valuable insight into forensic acquisition under di ...
Qualys is the leading provider of on demand IT security risk and compliance solutions - delivered as a service. Qualys solutions enable organizations of all sizes to easily and cost-effectively ensure that their business technology systems remain highly s ...
2-day practical penetration testing course - Build on the knowledge gained in CSTA Ethical Hacking: Hands-On, using the frameworks & tools used by professional penetration testers to: audit & compromise system security, assess weaknesses in w ...
Trust your inbox again with cloud email security protecting your people and critical information from malware, as well as malware free phishing and impersonation attempts. Keep Imposters OutAutomatically identify your high-profile targets for malware-fre ...
Capsa Popular
Capsa is a portable network analyzer application for both LANs and WLANs which performs real-time packet capturing capability, 24x7 network monitoring, advanced protocol analysis, in-depth packet decoding, and automatic expert diagnosis. Capsa's comprehen ...
Core Impact is designed to enable security teams to conduct advanced penetration tests with ease. With guided automation and certified exploits, the powerful penetration testing software enables you to safely test your environment using the same technique ...
The Metasploit Framework is a development platform for creating security tools and exploits. The framework is used by network security professionals to perform penetration tests, system administrators to verify patch installations, product vendors to perf ...
NOD32 Antivirus provides well balanced, state-of-the-art protection against threats endangering your PC and enterprise systems running various platforms. Anti-phishing - Secure your data and money against digital fraud.No slowdowns - Enjoy the full power ...
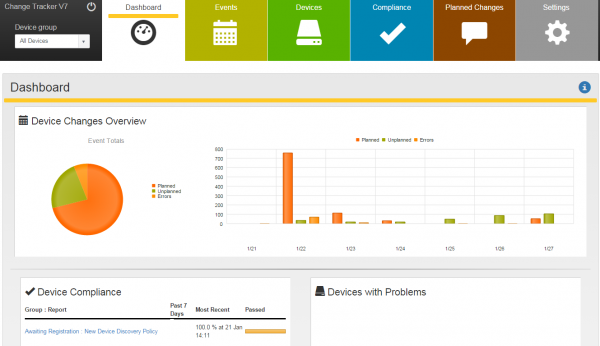
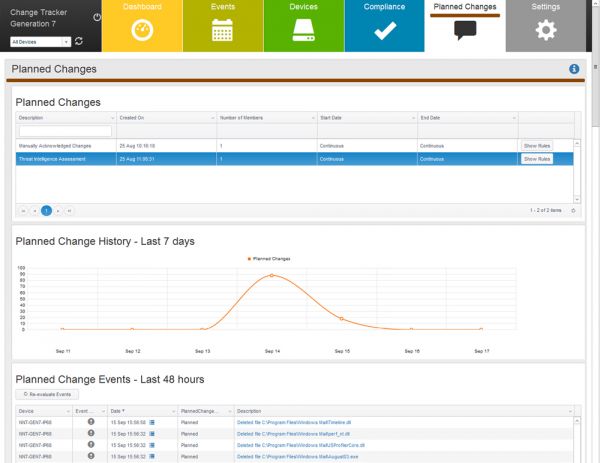
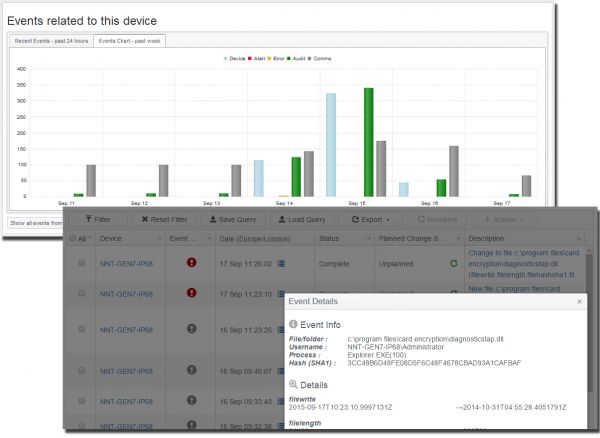
NNT Change Tracker Gen 7 R2 provides critical and fundamental cyber security prevention and detection. It does this by leveraging the required security best practice disciplines of system configuration and integrity assurance combined with the most compre ...
OSSIM provides all of the features that a security professional needs from a SIEM offering – event collection, normalization, and correlation. Established and launched by security engineers out of necessity, OSSIM was created with an understanding of the ...
Nmap ("Network Mapper") is a free open source utility for network exploration or security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts ...
WEPCrack is an open source tool for breaking 802.11 WEP secret keys
Learn to turn malware inside out! This popular course explores malware analysis tools and techniques in depth. FOR610 training has helped forensic investigators, incident responders, security engineers, and IT administrators acquire the practical skills t ...
Kismet is a 802.11b wireless network sniffer. It is capable of sniffing using almost any wireless card supported in Linux, including Prism2 based cards supported by the Wlan-NG project (Linksys, Dlink, Rangelan, etc), cards which support standard packet c ...
SecureTrack empowers large corporations to automate and streamline Firewall management activities. With Tufin SecureTrack, you can effectively audit your Firewall, monitor policy changes in real-time and test changes for compliance with corporate policies ...
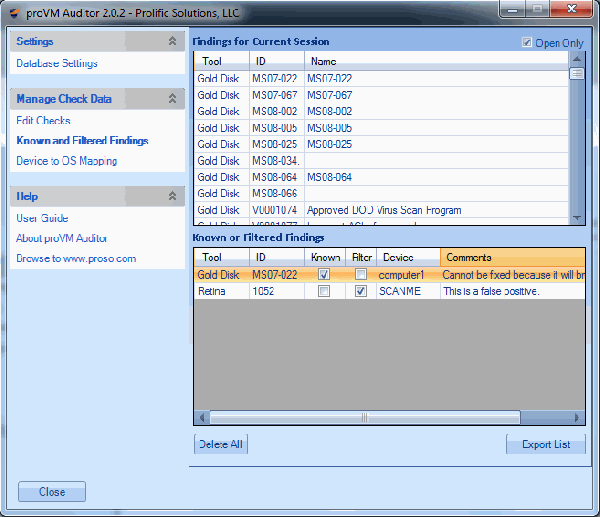
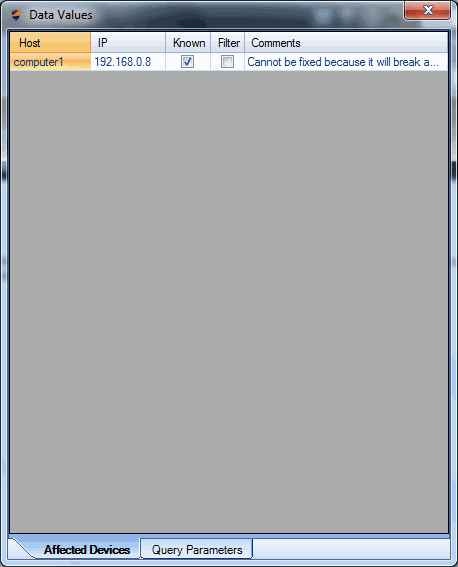
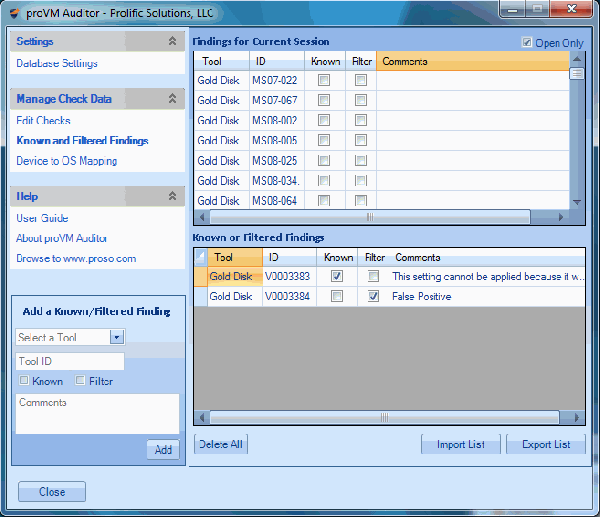
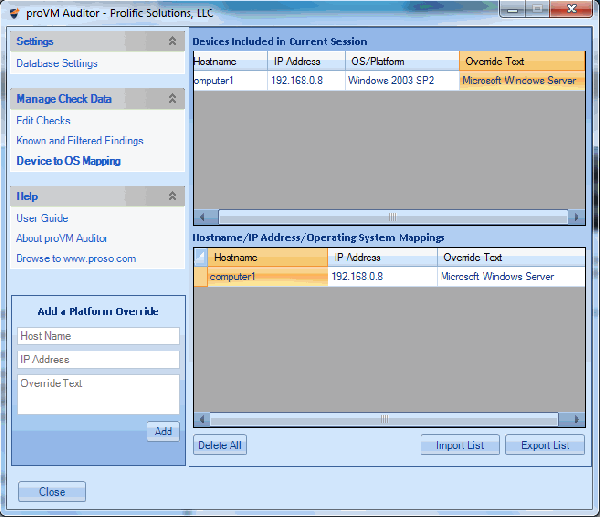
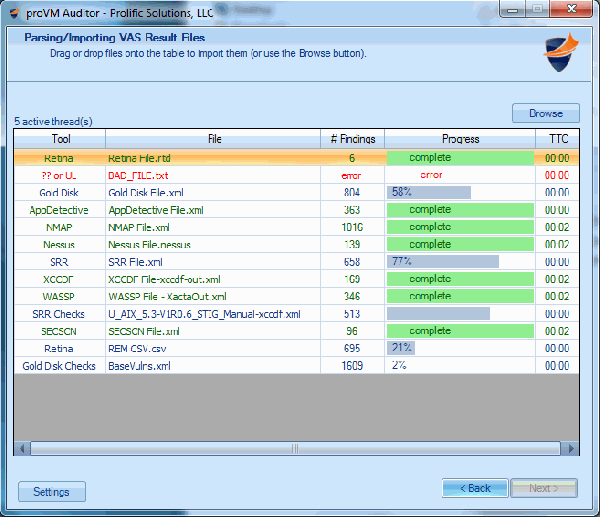
Manage all of your vulnerability data from 3rd party scanners with one console. proVM Auditor ingests data from vulnerability assessment scanners and allows you to perform centralized analysis of all of your findings. The SQL database supports features su ...
Next generation of pytbull, IDS/IPS testing framework
Page 1 of 56