Michele M Jordan
Wireless technology fundamentally changes accepted security paradigms. With the pervasive deployment of wireless technology, attackers have latched on with sophisticated and effective techniques to exploit wireless systems at work, at home, or on the road ...
SEC542 enables students to assess a web application's security posture and convincingly demonstrate the business impact should attackers exploit the discovered vulnerabilities. You will practice the art of exploiting web applications to find flaws in your ...
Learn to turn malware inside out! This popular reversing course explores malware analysis tools and techniques in depth. FOR610 training has helped forensic investigators, incident responders, security engineers, and threat analysts acquire the practical ...
Computer-based evidence is widely accepted in courts of law and is increasingly a mainstay of success--even where the crime or dispute in question is not "high-tech." SANS has worked hard to train forensic analysts and investigators to acquire, process, a ...
DEV522: Defending Web Applications Security Essentials is intended for anyone tasked with implementing, managing, or protecting Web applications. It is particularly well suited to application security analysts, developers, application architects, pen test ...
You will learn the skills required to reverse-engineer applications to find vulnerabilities, perform remote user application and kernel debugging, analyze patches for one-day exploits, perform advanced fuzzing, and write complex exploits against targets s ...
Maximize your training time and turbo-charge your career in security by learning the full SANS Security Essentials curriculum needed to qualify for the GSEC certification. In this course you will learn the language and underlying theory of computer securi ...
The Certified Computer Examiner (CCE) certification is a challenging test of the knowledge required to work in computer forensics, involving an on-line proctored exam and a thorough practical component involving correct investigation of several physical i ...
Intense School offers the finest Cisco Firewall Specialist certification training in the industry. During our intense boot camp, we guide you through configuring, troubleshooting and administering Cisco firewalls (PIX) and ASA (Adaptive Security Appliance ...
This boot camp teaches you how to use the tools and techniques used by cybercriminals to perform an ethical hack on your organization. You’ll learn ethical hacking methodologies and gain hands-on hacking experience in our cloud-hosted cyber range, i ...
Intense School is committed to giving students the best security training possible by proudly offering our CompTIA Security+ Boot Camp, a 5-day intense, accelerated course covering the most critical issues and practices of information security today. O ...
Course Description RHS429 introduces advanced system administrators, security administrators, and applications programmers to SELinux policy writing. Participants in this course will learn how SELinux works; how to manage SELinux; and how to write an S ...
Control users and devices across your networks with granular visibility and in-depth control. ExtremeControl extends the functionality within ExtremeCloud IQ – Site Engine. From a single screen, it enables the enforcement of consistent, highly secure acc ...
The AirMagnet WiFi Analyzer PRO automatically detects and diagnoses dozens of common Wi-Fi network performance problems, security threats, and wireless network vulnerabilities, enabling IT staff to quickly solve end-user issues. This tool detects throughp ...
Avira AntiVir Server ensures that the central receiving and distributing stations of your network under Windows and Unix are protected against virus attacks. Avira AntiVir does not only have innovative technologies for reliable virus and malware detection ...
Trustway Globull is a highly-secure external drive that allows users to address mobility issues and respond to the need for high levels of security — up to defense-level security.
Total Defense Essential Anti-Virus Internet Security Malware protection – simple, smart, and reliable protection from viruses, spyware, ransomware and other malware threats on up to 3 of your PCsMulti-layer technology – real-time and on-demand malware sc ...
Defeat business email compromise using advanced heuristics, BEC scam analysis, sender authentication enforcement & controls, and domain intelligence to help block typo squatting and identity spoofing.Protect your brand reputation by using automation t ...
FlowScan analyzes and reports on Internet Protocol (IP) flow data exported by routers. Consisting of Perl scripts and modules, FlowScan binds together (1) a flow collection engine (a patched version of cflowd), (2) a high performance database (Round Robin ...
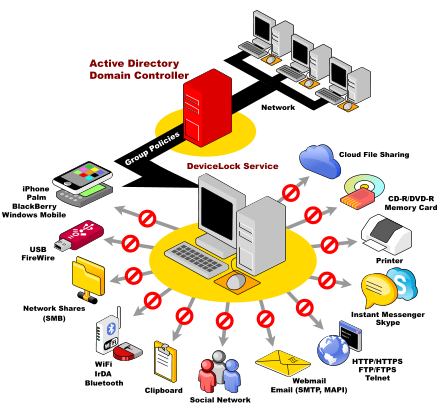
DeviceLock DLP Suite consists of five modules that protect your organization from data leak threats: DeviceLock provides network administrators the ability to set and enforce contextual policies for how, when, where to, and by whom data can or can&rsqu ...
Page 29 of 56