Kelsey Chalmers
Provides learners in Ireland with a range of learning courses through which they can improve their knowledge of cyber security
CoursesOnline offers professionals the opportunity to hone their cyber security skills via a wide selection of online learning courses. There are options available for those new to the sector and likewise with those with more experience. The courses are p ...
SanerNow Featured
SecPod’s SanerNow is an ADVANCED VULNERABILITY MANAGEMENT solution for preventing cyberattacks and achieving a security risk compliance posture. IT Security Teams use SanerNow to effectively reduce the risk imposed by vulnerabilities, misconfigurations, a ...
Become an Ethical Hacker Featured
This course bundle includes access to 6 accredited courses, providing IT professionals with a strong overview of everything that they need to know about cyber security, IT, and networking. Learners will gain a complete understanding as to how systems are ...
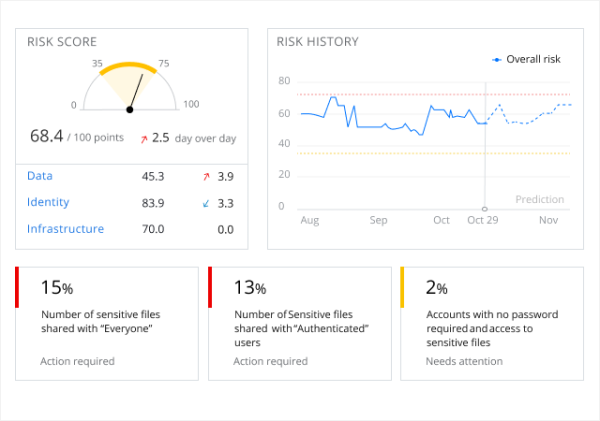
Cerebral is an AI-powered security platform that integrates User & Entity Behavior Analytics (UEBA) with User Activity Monitoring (UAM), allowing rapid Data Breach Response (DBR). The ability to hunt threats by proactively recognizing signs of risk, l ...
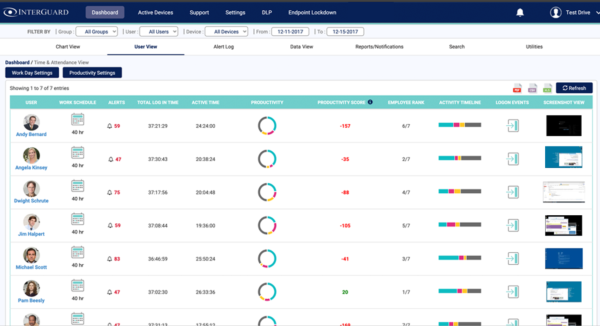
InterGuard’s employee monitoring software lets you track all employees activity from any endpoint - even when they work from home. Monitoring employee computer activity helps you proactively identify which employees are being productive and how much time ...
ActivTrak is more than just an insider threat management solution. It gives you a zoomed-in perspective of what your employees actually do in their digital workspaces. For example, it monitors what applications they use and how they divide their time betw ...
Netwrix analyzes user behavior, informing you of any deviations from the norm and mitigating risks related to sensitive data, regardless of its location. It smoothly integrates with Active Directory, Azure AD, Exchange, Office 365, and numerous other 3rd ...
Improve your security posture and quickly demonstrate compliance with a lightweight, ready-to-use, and affordable security information and event management solution. Identify and respond to threats faster Security Event Manager (SEM) will be another pai ...
Integrated Data Loss Prevention (DLP) solution for enterprises. ManageEngine Endpoint DLP Plus is a dedicated DLP software designed to protect sensitive data on managed endpoint devices from data disclosure and theft by leveraging advanced data loss prev ...
Protect against data loss at the endpoint Proofpoint Endpoint Data Loss Prevention (DLP) takes a modern, people-centric approach to protecting your data. It provides you with integrate content awareness and behavioural and threat awareness. This gives yo ...
Splunk Security Orchestration, Automation and Response (SOAR) Go from overwhelmed to in-control Automate manual tasks. Address every alert, every day. Establish repeatable procedures that allow security analysts to stop being reactive and focus on missi ...
Powerful security for your online world, with convenience. 1 platform, 3 products to choose from. Whether you need to make managing your passwords a no-brainer, or share files securely with your team members, or keep hackers out of your life, we can make ...
RememBear is a friendly app that saves and autofills your passwords to save you time and keep you safe online. Benefits: Friendly, approachable design Log in faster - let a Bear type your passwords and login to website with one click Faster on ...
Zoho Vault offers a robust free plan for individuals, with easy-to-use unlimited password storage, and flexible business plans for teams. Powerful security dashboards Get clear security insights into both your personal and business passwords. Identify a ...
Keep your credit cards safe and ready for checkout. Encrypted vault for your credit card numbers, synced to all your devices, for easy one-click payment. Protects your private notes and other text data. Keep your secrets, licenses, passport information ...
Avira Password Manager - Remember only one master password, it does the rest. Automatically logs you in to your online accounts. Generates strong, unique passwords and securely stores them. Checks for weak or reused passwords. Notifies you if an onl ...
Features: Intelligent insights across environments - provides visibility and applies context to on-prem and cloud-based resources; leverages continuous monitoring for a zero trust approach to security. Built-in analytics to accurately detect threats - ...
Easy to use and fast to deploy Privileged Access Management (PAM) available both on-premises or in the cloud. IBM Security Verify Privilege Vault makes it easy to identify and secure all service, application, administrator, and root accounts across your ...
Built and vetted by expertsInsightIDR has internal and external threat intel for our post-perimeter era, and the world’s most used penetration testing framework Metasploit. We do relentless research with Projects Sonar and Heisenberg. And because “we drin ...
Page 1 of 3