Michele M Jordan
McAfee Endpoint Protection — Advanced Suite delivers integrated, proactive security that blocks malware and zero-day threats. It protects Windows, Mac, and Linux systems on and off your network. With centralized policy-based management and auditing, Endpo ...
IPS Visio Stencils Popular
Stencils for many popular IPS products, including Nitro SIEM (McAfee ESM), Palo Alto Intrusion Prevention, Enterasys (Dragon) Intrusion Prevention, SourceFire, TippingPoint, Juniper, IBM, Cisco, McAfee Intrushield M-Series, and Fortinet. Also other generi ...
Every second of the day, the Forcepoint ThreatSeeker Intelligence scours the vast expanse of online content for potential threats. It’s up to the task. It receives global input from over 155 countries and, working in parallel with Forcepoint ACE, analyzes ...
E3 Forensic Platform provides processing options for smartphones, computers, cloud data, email, and more. A comprehensive review of data together to find the gaps that hold the keys to your investigation. Universal Data ProcessingData processing in ...
F-Response is a vendor neutral, patented software utility that enables an investigator to conduct live forensics, Data Recovery, and eDiscovery over an IP network using their tool(s) of choice. F-Response is not another analysis tool. F-Response is a util ...
The Remote Forensics architecture allows companies to reduce their investigation budgets and enable analysts to work more productively by providing a fast, secure and effective incident response framework that enforces a consistent methodology allowing an ...
GRR is an Incident Response Framework focused on Remote Live Forensics. State of the Project August 2011 GRR is in proof of concept stage and is not considered production-ready. The basic principles have been proven, but there is significant work to be d ...
The McAfee Application Data Monitor appliance decodes an entire application session to Layer 7, providing a full analysis of everything from the underlying protocols and session integrity all the way up to the contents of the application (such as the text ...
The non-intrusive design of McAfee Database Event Monitor for SIEM supports your expanding compliance auditing and reporting requirements and enhances security operations. While it monitors all database transactions, Database Event Monitor for SIEM provid ...
OpenDLP Popular
OpenDLP is a free and open source, agent- and agentless-based, centrally-managed, massively distributable data loss prevention tool released under the GPL. Given appropriate Windows, UNIX, MySQL, or MSSQL credentials, OpenDLP can simultaneously id ...
Email is the No. 1 threat vector. Social actions such as phishing and email scams arrive via email 96% of the time, and these security threats are always evolving. Proofpoint delivers the most effective unified solution to protect your people and critical ...
Proofpoint Enterprise Privacy provides powerful data loss prevention, protection, encryption capabilities – the easiest and most cost-effective way for organizations to prevent leaks of sensitive data. Powerful policies help organizations protect email da ...
Besides the general data extracted by similar products, Oxygen Forensic Suite can extract a lot of unique information Using low-level protocols allows the program to extract: phone basic information and SIM-card data, contacts list, caller groups, speed ...
The Annual Computer Security Applications Conference (ACSAC) is an internationally recognized forum where practitioners, researchers, and developers in information and system security meet to learn and to exchange practical ideas and experiences. If you a ...
360-FAAR (Firewall Analysis Audit and Repair) is an offline, command line, Perl firewall policy manipulation tool to filter, compare to logs, merge, translate and output firewall commands for new policies, in Checkpoint dbedit, Cisco PIX/ASA or Netscreen ...
MOBILedit Forensic is a phone extractor, data analyzer and report generator all in one solution. A powerful 64-bit application using both the physical and logical data acquisition methods, MOBILedit Forensic is excellent for advanced application analyzer, ...
The Open Vulnerability Assessment System (OpenVAS) is a framework of several services and tools offering a comprehensive and powerful vulnerability scanning and vulnerability management solution. OpenVAS is a framework of several services and too ...
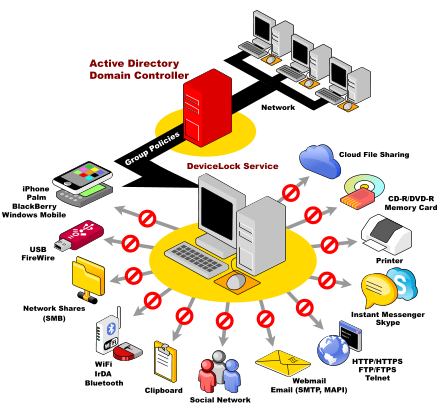
DeviceLock DLP Suite consists of five modules that protect your organization from data leak threats: DeviceLock provides network administrators the ability to set and enforce contextual policies for how, when, where to, and by whom data can or can&rsqu ...
The Palo Alto Networks VM-Series comprises three virtualized next-generation firewall models – VM-100, VM-200, and VM-300, supported on VMware ESXi 4.1 and ESXi 5.0 platforms. 2, 4 or 8 CPU cores on the virtualized server platforms can be assign ...
Trellix Email Security – Server leads the industry in identifying, isolating, and immediately stopping URL and attachment-based attacks, before they enter an organization’s environment. Email Security - Server provides real-time detection and preve ...
Page 25 of 56