Michele M Jordan
The SecurityTube iOS Security Expert, or SISE, is an online course and certification which focuses on the iOS platform and application security. This course is ideal for pentesters, researchers and the casual iOS enthusiast who would like to dive de ...
This course is ideal for penetration testers, security enthusiasts and network administrators. A non-exhaustive list of topics to be taught includes: Metasploit Basics and Framework Organization Server and Client Side Exploitation Meterpreter – Exte ...
The SecurityTube Wi-Fi Security Expert (SWSE) is an online certification for Wi-Fi Security and Penetration Testing. This course is ideal for penetration testers, security enthusiasts and network administrators. The course leading to the certification exa ...
AlgoSec FireFlow automates the entire security policy change workflow – from submission and design to risk analysis, implementation, validation and audit - enabling security and operations teams to: Reduce the time required to process firewall changes ...
Justniffer is a network protocol analyser that captures network traffic and produces logs in a customised way, can emulate Apache web server log files, track response times and extract all 'intercepted' files from the HTTP traffic. It let's you interacti ...
AVL is developed by Antiy Labs, that is applicable for Android systems. This app displays the mobile anti-virus engine of AVL SDK, which provides the basic functionality of virus scan to protect your Android system and applications. AVL SDK Mobile provid ...
Free mobile antivirus for Android, by ESET. Fire OS optimized experience Antivirus with Automatic Scan of downloaded applications and files On-demand Scan triggered by user On-access Scan of downloaded applications and files ...
Nogotofail is a network security testing tool designed to help developers and security researchers spot and fix weak TLS/SLL connections and sensitive cleartext traffic on devices and applications in a flexible, scalable, powerful way. It includes testing ...
vFeed framework is an open source naming scheme concept that provides extra structured detailed third-party references and technical characteristics for a CVE entry through an extensible XML schema. It also improves the reliability of CVEs by providing a ...
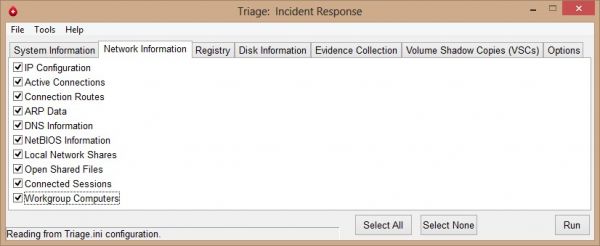
Triage-IR is a script written by Michael Ahrendt, which will collect system information, network information, registry hives, disk information and will also dump memory. One of the capabilities of Triage-IR is collecting information from Volume Shadow Cop ...
Vistumbler is an open source Windows application that finds Wireless access points - Uses the Vista command 'netsh wlan show networks mode=bssid' to get wireless information. It displays the basic AP details, including the exact authentication and e ...
Wifi Analyzer is a free Android app you can use for finding APs on your Android-based smartphone or tablet. It lists the basic details for APs on the 2.4-GHz band, and on supported devices on the 5-GHz band as well. You can export the AP list (in XML form ...
Encrypted Disk Detector is a command-line tool that can quickly, and non-intrusively, check for encrypted volumes on a computer system during incident response. The decision can then be made to investigate further and determine whether a live acquisition ...
AXIOM Cyber is a robust digital forensics and incident response solution for businesses that need to perform remote acquisitions and collect & analyze evidence from computers, the cloud, and mobile devices.Off-Network CollectionAXIOM Cyber enables you ...
The first forensic browser able to quickly and easly capture web pages that are to be brought to trial in criminal and civil proceedings. Acquisition of all websitesFAW acquires websites of any type: HTML5, CMS, static, dynamic, with frames, blogs, e-com ...
Belkasoft Live RAM Capturer is a tiny free forensic tool that allows to reliably extract the entire contents of computer’s volatile memory—even if protected by an active anti-debugging or anti-dumping system. Separate 32-bit and 64-bit builds are availabl ...
Belkasoft X (Belkasoft Evidence Center X) is a flagship tool by Belkasoft for computer, mobile and cloud forensics. It can help you to acquire and analyze a wide range of mobile devices, run various analytical tasks, perform case-wide searches, bookm ...
Belkasoft X (Belkasoft Evidence Center X) is a flagship tool by Belkasoft for computer, mobile and cloud forensics. It can help you to acquire and analyze a wide range of mobile devices, run various analytical tasks, perform case-wide searches, bookmark a ...
Kernel Exhcnage EDB Viewer is an Exchange Mailbox viewer tool, that assists system administrators in opening EDB files even in the absence of MS Exchange Servers. Now recover your corrupt exchange database files for free and review their entire contents ...
Viewer for standalone files containing Microsoft Outlook Express 4,5 and 6 message database (*.idx/*.mbx/*.dbx), Windows Vista Mail/Windows Live Mail and Mozilla Thunderbird message databases as well as standalone EML files. This application is based on ...