Directory: A-Z
NetStumbler is a Windows utility for 802.11b based wireless network auditing
A complete solution deployed in the cloud or on-premise, with carrier-grade performance and reliability Dynamic CategorizationNetsweeper’s dynamic categorization engine scans and sorts the content of billions of websites and adds this information to a da ...
Our feature-rich NetVanta Routers deliver the power and performance needed for high-quality VoIP and other bandwidth-intensive applications.
NetWall is the first truly manageable business-oriented firewall and VPN software solution to protect each IT zone according to its specific security requirements, providing the right security. Its innovative DdMZ architecture allows you to tightly contro ...
Network Box provides an enterprise security solution using best of breed technology.
Network Critical is the premier provider of Access Technology Solutions for today’s datacenter. Our Network TAPs give you the ability to safely, securely and economically see what is happening on your network. We provide enterprise Ethernet TAP access sol ...
Computer-based evidence is widely accepted in courts of law and is increasingly a mainstay of success--even where the crime or dispute in question is not "high-tech." SANS has worked hard to train forensic analysts and investigators to acquire, process, a ...
3 years Full Time
2 years Full Time
3 years Full Time
4 years Full Time
The Network Pump is a Cross Domain Solution (CDS) providing network domain separation through a failsafe and redundant security architecture. It performs high assurance validation, inspection, sanitization, and/or transliteration, as required, per data fl ...
Every day, Shadowserver sends custom remediation reports to more than 7000 vetted subscribers, including over 133 national governments (201 National CSIRTs) covering 175 countries and territories, as well as many Fortune 500 companies. These reports are d ...
2 years Full Time / 3 years Sandwich Course
NetworkMiner is an open source Network Forensic Analysis Tool (NFAT) for Windows (but also works in Linux / Mac OS X / FreeBSD). NetworkMiner can be used as a passive network sniffer/packet capturing tool in order to detect operating systems, sessions, ho ...
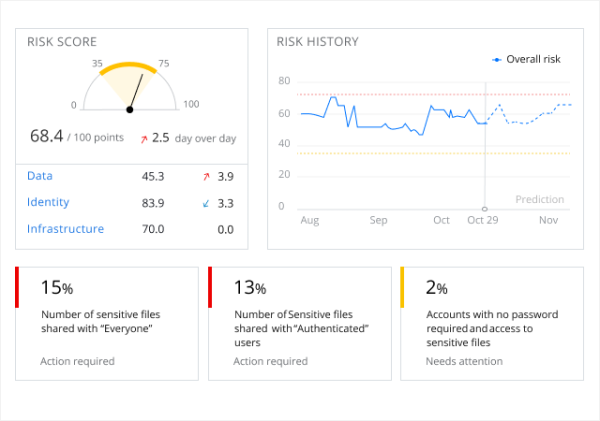
Netwrix analyzes user behavior, informing you of any deviations from the norm and mitigating risks related to sensitive data, regardless of its location. It smoothly integrates with Active Directory, Azure AD, Exchange, Office 365, and numerous other 3rd ...
The Nexor Data Diode is an EAL7+* evaluated solution to the information sharing problem by only allowing data transfers in one direction, guaranteeing that no data will leak back from the secure to the less secure network.
NeXpose is an enterprise-level vulnerability assessment and risk management product that identifies security weaknesses in a network computing environment. It offers a comprehensive, one-stop solution for data gathering, reporting and remediation, elimina ...
This course will put you through the paces in Linux as it stands itself (the operating system), and then move you into Linux and Data Forensics. The idea here is to take someone new to Linux and get them up and running with enough knowledge and hands on e ...
NextGen UTM-Firewall. Simple. Fast. Secure. Reliable ransomware protection The UTM Firewall is automatically updated with the latest security patches by Securepoint’s Cyber Defence Cloud in real time. Comprehensive protection Using a firewall protects ...