Michele M Jordan
AlgoSec BusinessFlow makes it easy to securely provision, maintain and decommission connectivity for business applications. By automatically mapping application connectivity requirements to the underlying network infrastructure, BusinessFlow accelerates a ...
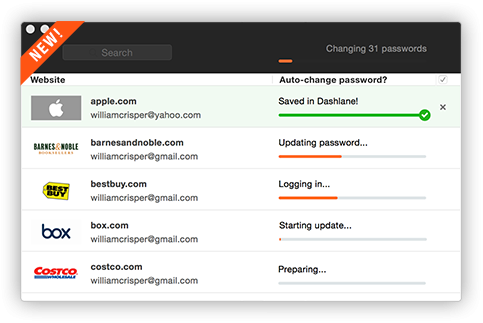
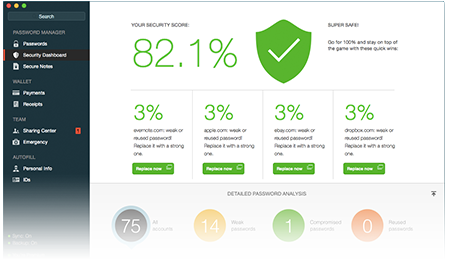
Dashlane fills all your passwords, payments, and personal details wherever you need them, across the web, on any device. Every password, Everywhere Save passwords and logins as you browse. Store an unlimited number of passwords and access them anywhe ...
Developed with the German Federal Office for Information Security (BSI), the fully virtualized R&S Browser in the Box surfing environment offers an innovative, multi-level concept for secure and convenient Internet surfing and optimum protection again ...
BUFFERZONE is a virtual container that protects any content source that you define as potentially insecure including web browsers, email, Skype, FTP and even removable storage. You are able to definite granular containment poloicies according to network s ...
Sandboxie runs your programs in an isolated space which prevents them from making permanent changes to other programs and data on your computer. Running your Web Browser under the protection of Sandboxie means that all malicous software downloaded by the ...
Visualize your entire network Instantly visualize your entire hybrid network security topology – in the cloud, on-premises, and everything in between. Understand the impact of network security policies on traffic, quickly troubleshoot connectivity issues ...
CodeSonar is GrammaTech's flagship static analysis software, designed for zero-tolerance defect environments. CodeSonar analyzes source code and binaries, identifying programming bugs that can result in system crashes, memory corruption, leaks, data races ...
About Real time, system wide monitoring Monitoring technology knows what every process on your machine is doing at every given moment - and is specially designed to be lightweight and with a small footprint. Behavioural based detection Purely behaviou ...
PistolStar, Inc. maker of PortalGuard offers an on-premise turnkey user authentication solution-set for companies with external-facing web applications to their employees, contractors, suppliers, and vendors. This all-in-one integrated design includes two ...
RFD-01 Wide Range RF Signal Detector is a super heterodyne receiver with low IF and frequency synthesizer. Scanning and analyzing cycle period is 1.0-1.5 sec. It can operate within guard, sweep, search, difference search modes and monitoring of digital si ...
FlowNBA is a complete solution for network monitoring based on NetFlow/IPFIX. Thanks to the used technology it enables complete overview of the network traffic, detailed information about all communications and provides information about who communicates ...
NetworkMiner is an open source Network Forensic Analysis Tool (NFAT) for Windows (but also works in Linux / Mac OS X / FreeBSD). NetworkMiner can be used as a passive network sniffer/packet capturing tool in order to detect operating systems, sessions, ho ...
The Barracuda Firewall provides extensive application control and user identity functions in an easy-to-use solution. This firewall is optimised for bandwidth-sensitive tasks like packet forwarding and routing layer 7 applications, Intrusion Prevention (I ...
ADD is a physical memory anti-analysis tool designed to pollute memory with fake artifacts. This tool was first presented at Shmoocon 2014. Please note that this is a proof of concept tool. It forges OS objects in memory (poorly). It would be easy (very e ...
The iVe Ecosystem is a collection of tools that supports investigators throughout the entire vehicle forensics process with a mobile application for identifying vehicles, a hardware kit for acquiring systems, and forensic software for analyzing data. &nb ...
The Barracuda Web Filter lets organizations benefit from online applications and tools without exposure to web-borne malware and viruses, lost user productivity, and misused bandwidth. As a comprehensive solution for web security and management, it unite ...
McAfee Endpoint Protection — Advanced Suite delivers integrated, proactive security that blocks malware and zero-day threats. It protects Windows, Mac, and Linux systems on and off your network. With centralized policy-based management and auditing, Endpo ...
Snare pairs well with any SIEM or Security Analytics platform and is trusted by public and private sector organizations worldwide to meet evolving log management requirements including Zero Trust. Snare helps companies around the world improve their log ...
DFLabs IncMan Suite, Collaborative Incident Response and Threat Intelligence PlatformIncMan Suite is a comprehensive CyberSecurity incident and data breach investigation & response platform that simplifies the collaborative management of every k ...
With the signature Emperor scorpion shape and outline, an industrial grade steel structure, tilting capabilities, integrated audio system, LED lighting and much more, the Emperor is the future of high-end home and office computer work environments. The E ...
Page 23 of 56