Michele M Jordan
BlackArch Linux is an Arch Linux-based distribution for penetration testers and security researchers.
The EZ-Tap Pro is an industry leading protocol analyzer.
Get protection from malware and unauthorized application for your business. Keep your business running smoothly without downtime by protecting your network from outside threats. Deliver collaborative approach to complex security threats with unified manag ...
Zyxel's ZyWALL Security solutions provide real-time protection that ensure service continuity, optimal CP performance and improved network control. Three product lines to address every size from SMB to Enterprise.
Reinforce security for hybrid network with SecuExtender as the Zero Trust agent, integrated always-on IPSec VPN, traffic shaping, IKEv2/EAP, supporting devices insight and more granular control over remote workplaces.
Omega Core Audit provides a software security solution to help customers approach the complex and difficult security challenges in Oracle Database Systems - protecting against outsider and/or insider threats, unauthorized access and enforcing duty separat ...
Adversaries want your data and assets. Fidelis Deception makes them believe they’ve struck gold. But what they’ve really done is trapped themselves and alerted your cyber defenders. Automatically create and deploy authentic deception layers based o ...
Gophish is an open-source phishing toolkit meant to help pentesters and businesses conduct real-world phishing simulations. It is a phishing framework in the Go programming language, released as compiled binaries with no dependencies.
The LUCY Social Engineering Suite and Malware Testing Suite (or CYBERSECURITY CRASH TEST DUMMY) facilitate multiple application areas. They can be used for: – People testing and education – Technology assessments – An inoffensive penetration test sho ...
Phishing Frenzy is an Open Source Ruby on Rails application that is leveraged by penetration testers to manage email phishing campaigns. The goal of the project is to streamline the phishing process while still providing clients the best realistic phishi ...
SPF (SpeedPhish Framework) is a python tool designed to allow for quick recon and deployment of simple social engineering phishing exercises. SPF includes many features that allow you to quickly configure and perform effective phishing attacks, including ...
For phishing, SET allows for sending spear-phishing emails as well as running mass mailer campaigns, as well as some more advanced options, such as flagging your message with high importance and adding list of target emails from a file. SET is Python base ...
SecurityIQ combines a phishing simulator and computer-based security awareness training in one cloud-based service.
ThreatSim attack simulation product provides a phishing-focused security awareness training program. The ThreatSim mock attack system allows you to deliver simulated phishing emails with embedded Teachable Moments, which display targeted "just-in-time tea ...
Duo Insight is a free phishing assessment tool by Duo Security that allows you to find vulnerable users and devices in minutes and start protecting them right away.
A free tool that provides a simple, safe and effective mechanism for security teams and administrators to run their own phishing tests inside their organization. Simply install the application on a server or workstation and create a url email/sms/etc. cam ...
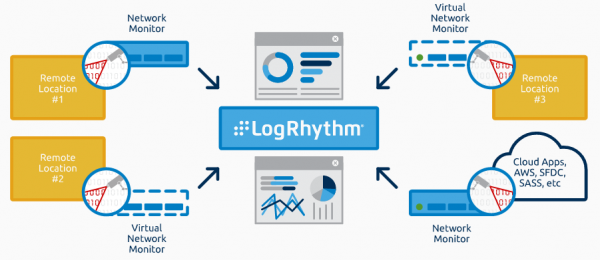
Unleash the power of your SOC with the LogRhythm NextGen SIEM Platform Detect threats earlier and fasterWhen it comes to stopping threats, seconds matter. That’s why we built our NextGen SIEM platform for speed. You’ll quickly identify threats, automate ...
Real-time threat detections across endpoints, data centers, and the cloud. Securing your network against advanced persistent threats (APTs) requires greater visibility to detect actors and their actions so that you can reduce your response time. As threa ...
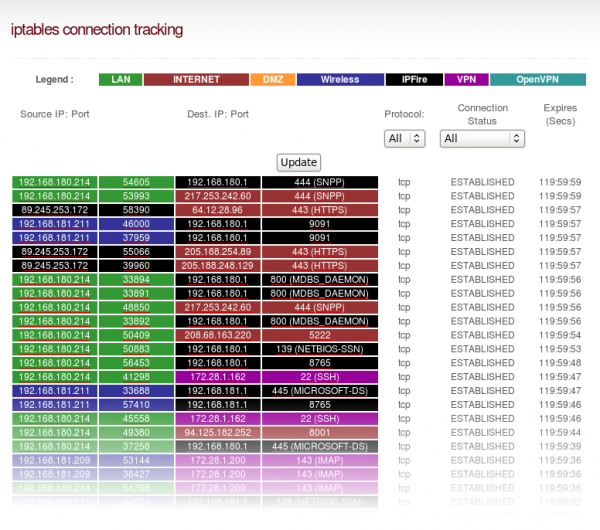
With IPFire you can easily deploy many variations of it, such as a firewall, a proxy server or a VPN gateway. IPFire forms the base of a secure network. It has the power to segment networks based on their respective security levels and makes it easy to cr ...
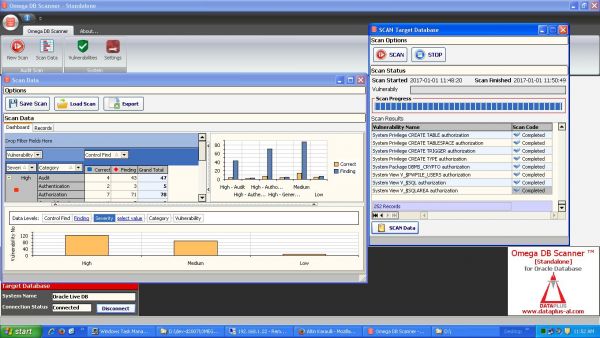
Omega DB Security Reporter is a security auditing and software-only solution for Oracle Databases. Implementing quick reporting, visualisation and documentation of the security posture of the Oracle database on the following security areas: System Priv ...