Michele M Jordan
Wapiti - Web application vulnerability scanner / security auditor Wapiti allows you to audit the security of your web applications. It performs "black-box" scans, i.e. it does not study the source code of the application but it will scan the webpages of ...
Websecurify is a powerful web application security testing platform designed from the ground up to provide the best combination of automatic and manual vulnerability testing technologies. Some of the main features of Websecurify include: Availab ...
Cross Site "Scripter" is an automatic -framework- to detect, exploit and report XSS vulnerabilities in web-based aplications. It contains several options to try to bypass certain filters, and various special techniques of code injection.
NTT Application Security provides complete web application security at a scale and accuracy unmatched in the industry. No matter how many websites or how often they change, we can concurrently scan an unlimited number of sites without slowing you down. Wo ...
HackerTarget.com provides free security scans for websites. You can purchase a Scan Membership, which then removes the scan limits per day. They provide scans using known, Open Source tools, including: * Nmap Port Scan * Nikto Web Scan * OpenVas ...
WSSA examines your website pages, applications and web servers to find security weaknesses and vulnerabilities that would give hackers an opportunity to do damage. Every scan starts by testing the equipment that hosts your site. No matter how carefully c ...
GamaSec is a remote online web vulnerability assessment service delivered via SaaS (software as a service) and is designed to identify security weakness in web application, as well as site exposure risks. GamaScan tests the security of your web applicati ...
SecPoint delivers online vulnerability scanning service. You get the following benefits: Online Vulnerability Scanning Get HTML, XML, PDF Reports Get Clear Solutions how to fix the found vulnerabilities User Friendly interface Scan any operating ...
Veracode's automated web security scanning, also known as dynamic analysis or black-box testing empowers companies to identify and remediate security issues in their running web applications before hackers can exploit them. By testing web security in a ru ...
Safend Reporter automatically generates reports on intentional and unintentional misuse of private company information. Reports can be strategic and periodic and built-in or customized by an administrator. Each report is set in a comprehensive interface a ...
SourceMeter is an innovative tool built for the precise static source code analysis of C/C++, Java, C#, Python, and RPG projects. This tool makes it possible to find the weak spots of a system under development from the source code only, without the need ...
This popular course explores malware analysis tools and techniques in depth. FOR610 training has helped forensic investigators, incident responders, security engineers, and IT administrators acquire the practical skills to examine malicious programs that ...
REMnux™ is a free Linux toolkit for assisting malware analysts with reverse-engineering malicious software. It strives to make it easier for forensic investigators and incident responders to start using the variety of freely-available tools that can exami ...
Use this service to test your firewall rules. If you intend to allow or deny connections through your firewall, you can check to see what will happen when an Internet user attempts to connect. Behind the scenes, this firewall test uses NMap to attempt to ...
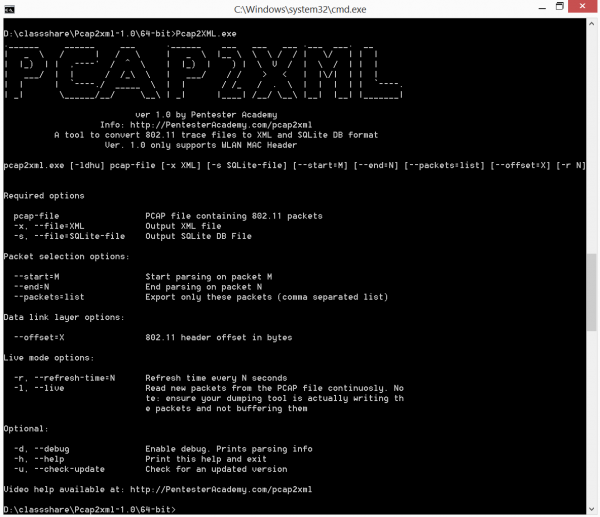
PCAP2XML is a tool suite which takes 802.11 PCAP trace files as input and can convert them into XML or SQLITE representations. This allows a pentester to run arbitrary queries on the packet header fields. Why do we need this? Wireshark is great when it ...
PentesterLab is an easy and great way to learn penetration testing. PentesterLab provides vulnerable systems that can be used to test and understand vulnerabilities. Hands-on There is only one way to properly learn web penetration testing: by getting y ...
Passwords are weak. Tokens are expensive. Don’t compromise on security or price. Wave Virtual Smart Card does anything your physical smart cards and tokens do, but it starts with hardware you already have: the Trusted Platform Module (TPM), a hardware se ...
Safend Inspector prevents transfer of sensitive company information. As information is processed it is classified and its access permissions and security profile are configured. During data transfer Inspector checks for sensitive information in its c ...
Add a layer of real-time security to your web defenses by accurately assessing the risk posed when opening a URL. This critical layer of proactive protection helps defend against emerging threats by determining a website's risk level – independent of its ...
The BrightCloud File Reputation Service provides next-generation Webroot threat intelligence by offering customers a dynamic, up-to-the-minute file reputation service to protect their data and assets. This real-time lookup service of known malicious and w ...
Page 16 of 56