Michele M Jordan
Nmap ("Network Mapper") is a free open source utility for network exploration or security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts ...
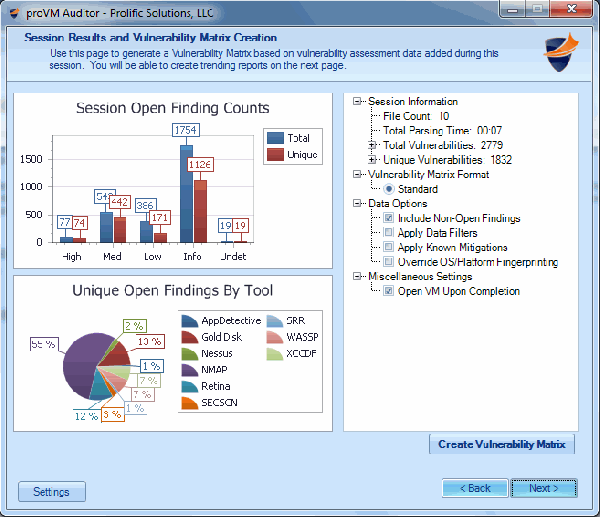
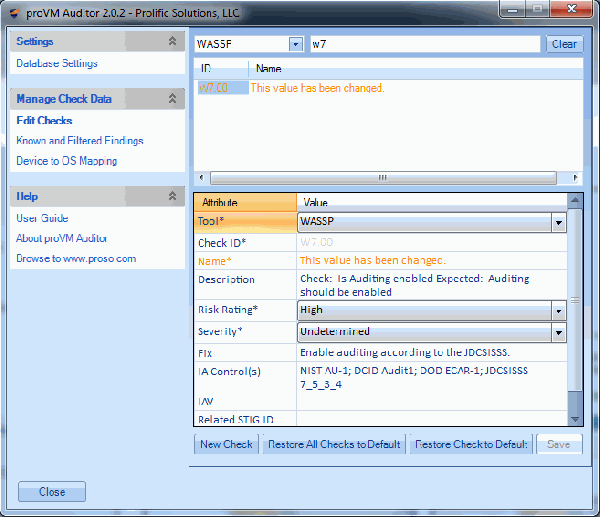
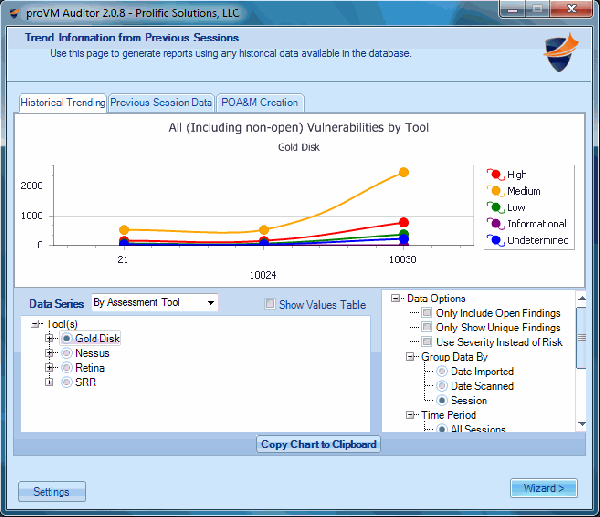
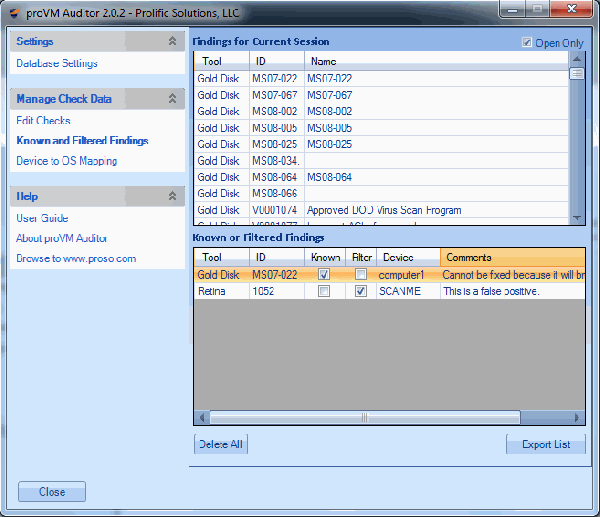
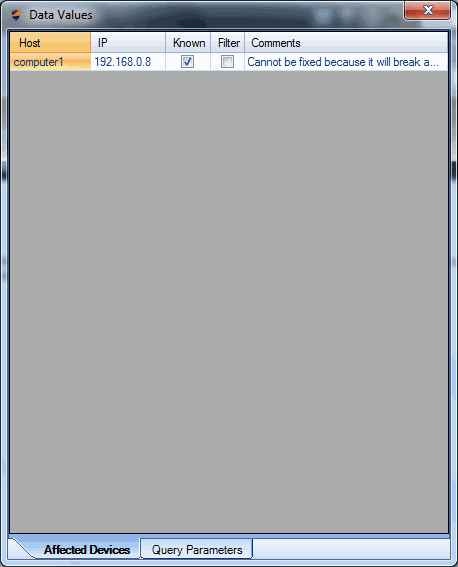
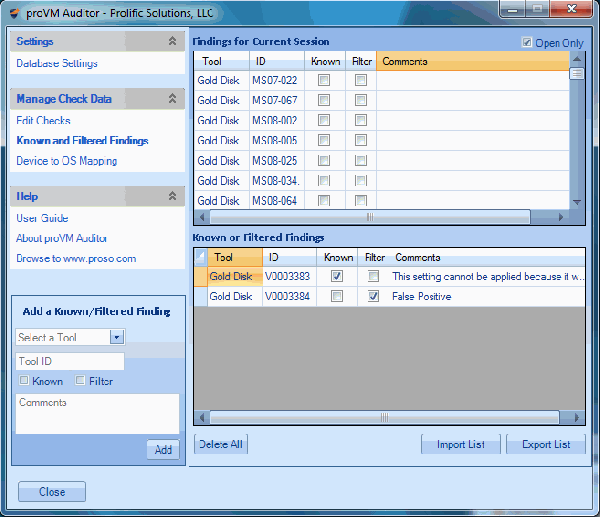
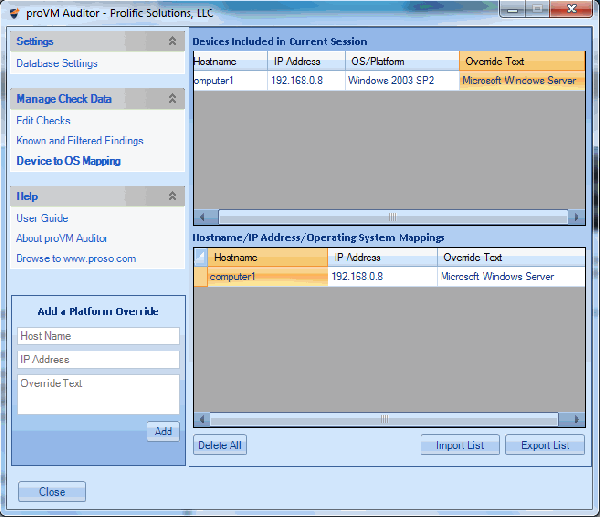
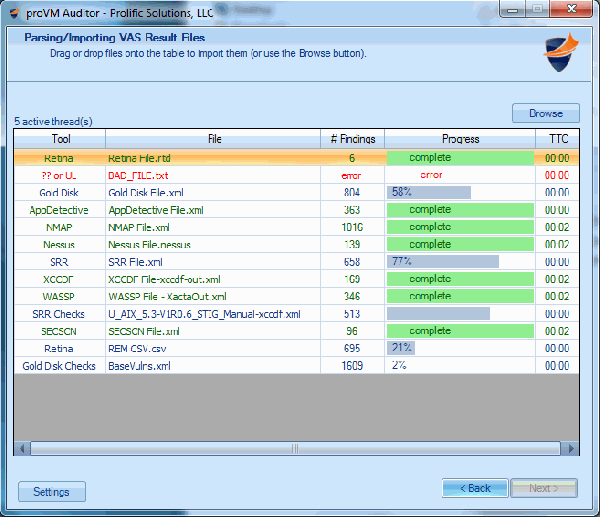
Manage all of your vulnerability data from 3rd party scanners with one console. proVM Auditor ingests data from vulnerability assessment scanners and allows you to perform centralized analysis of all of your findings. The SQL database supports features su ...
SecureTrack empowers large corporations to automate and streamline Firewall management activities. With Tufin SecureTrack, you can effectively audit your Firewall, monitor policy changes in real-time and test changes for compliance with corporate policies ...
Kismet is a 802.11b wireless network sniffer. It is capable of sniffing using almost any wireless card supported in Linux, including Prism2 based cards supported by the Wlan-NG project (Linksys, Dlink, Rangelan, etc), cards which support standard packet c ...
Learn to turn malware inside out! This popular course explores malware analysis tools and techniques in depth. FOR610 training has helped forensic investigators, incident responders, security engineers, and IT administrators acquire the practical skills t ...
WEPCrack is an open source tool for breaking 802.11 WEP secret keys
MailXaminer is a comprehensive email examination tool to carry out a thorough analysis of a bunch of emails and its header. With the help of this tool; forensicators can preview more than 20 email file types and perform advanced search operation within th ...
This hands-on track offers a practical working knowledge in intrusion detection and traffic analysis, taught by top practitioners/authors in the field. This is the most advanced program in network intrusion detection that has ever been taught. All of the ...
Exports to NetFlow
The Black Hat Briefings brings together a unique mix in security: the best minds from government agencies and global corporations with the most respected independent researchers and hackers. These forums take place regularly in Las Vegas, Amsterdam, Tokyo ...
Disk EncryptionIncreased remote working makes it more important than ever to secure computers and the data on them. With the huge number of laptops lost, stolen, or misplaced every day, a crucial first line of defense against the loss or theft of devices ...
The SmartWall family of DDoS protection solutions mitigates a wide range of attacks all while maintaining the availability of applications and services it is protecting and without disrupting the delivery of legitimate traffic. It is designed to handle la ...
floppyfw is a router with the advanced firewall-capabilities in Linux that fits on one single floppy disc.
Do you need to analyze multiple variations of essentially the same program ? Do you need to understand the changes between two versions of a program ? Are you trying to detect code theft ? SABRE BinDiff uses a unique graph-theoretical approach to allow co ...
The @stake Sleuth Kit (TASK) allows an investigator examine the file systems of a suspect computer in a non-intrusive fashion. TASK is a collection of UNIX-based command line tools that can analyze NTFS, FAT, FFS, EXT2FS, and EXT3FS file systems. TASK rea ...
This course will give you a firm understanding of advanced incident response and computer forensics tools and techniques to investigate data breach intrusions, tech-savvy rogue employees, advanced persistent threats, and complex digital forensic cases. ...
TThe goal of this seven-day accelerated course is to provide information security professionals a fully-immersed, zero-distraction, all-inclusive CISSP CBK training and certification experience. Our CISSP Firebrand Training encompasses the (ISC)2 CISSP CB ...
CyberGatekeeper LAN and CyberGatekeeper Remote let systems access the network only after verifying they comply with security policies. If systems are not in compliance or do not participate in the audit, they are kept in a quarantine network. With network ...
Arbor Sightline Popular
Arbor Sightline provides robust capabilities from network-wide capacity planning, to identifying and managing the mitigation of threats to the network. Network Peering Analysis Your network delivers value to customers and users when it connects to ...
NetStumbler is a Windows utility for 802.11b based wireless network auditing
Page 3 of 56