Michele M Jordan
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience functions, interactive help, and command completion, Recon-ng provides a powerful environment in whic ...
BlackArch Linux is an Arch Linux-based distribution for penetration testers and security researchers.
The EZ-Tap Pro is an industry leading protocol analyzer.
Get protection from malware and unauthorized application for your business. Keep your business running smoothly without downtime by protecting your network from outside threats. Deliver collaborative approach to complex security threats with unified manag ...
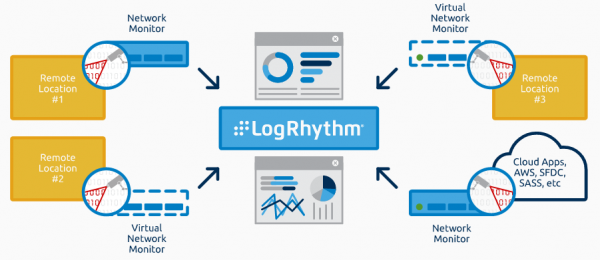
Zyxel's ZyWALL Security solutions provide real-time protection that ensure service continuity, optimal CP performance and improved network control. Three product lines to address every size from SMB to Enterprise.
Reinforce security for hybrid network with SecuExtender as the Zero Trust agent, integrated always-on IPSec VPN, traffic shaping, IKEv2/EAP, supporting devices insight and more granular control over remote workplaces.
Omega Core Audit provides a software security solution to help customers approach the complex and difficult security challenges in Oracle Database Systems - protecting against outsider and/or insider threats, unauthorized access and enforcing duty separat ...
Adversaries want your data and assets. Fidelis Deception makes them believe they’ve struck gold. But what they’ve really done is trapped themselves and alerted your cyber defenders. Automatically create and deploy authentic deception layers based o ...
Gophish is an open-source phishing toolkit meant to help pentesters and businesses conduct real-world phishing simulations. It is a phishing framework in the Go programming language, released as compiled binaries with no dependencies.
The LUCY Social Engineering Suite and Malware Testing Suite (or CYBERSECURITY CRASH TEST DUMMY) facilitate multiple application areas. They can be used for: – People testing and education – Technology assessments – An inoffensive penetration test sho ...
Real-time threat detections across endpoints, data centers, and the cloud. Securing your network against advanced persistent threats (APTs) requires greater visibility to detect actors and their actions so that you can reduce your response time. As threa ...
Cybercriminals exploit unpatched vulnerabilities in operating systems and common applications (Java, Adobe, Internet Explorer, Microsoft Office, etc.) as part of targeted attacks against businesses of every size. This risk is compounded by increasing IT ...
The Center for Cybersecurity Education and Leadership at Montreat College provides guidance and oversight to our academic program, to the distribution of cyber defense information, and to collaborative efforts in cybersecurity with an emphasis on combinin ...
RVAsec is the first Richmond, VA based security convention that showcases local talent as well as brings the best speakers to the midatlantic region. RVAsec attracts over 400 security professionals from across the country. The conference is dual-track a ...
VulnDB is the most comprehensive and timely vulnerability intelligence available and provides actionable information about the latest in security vulnerabilities via an easy-to-use SaaS Portal, or a RESTful API that allows easy integration into GRC tool ...
Bitraser is a certified and secure data erasing software which permanently deletes hard disk data beyond the scope of data recovery. It supports multiple international erasure standards such as DoD 3 passes / 7 passes and NIST.
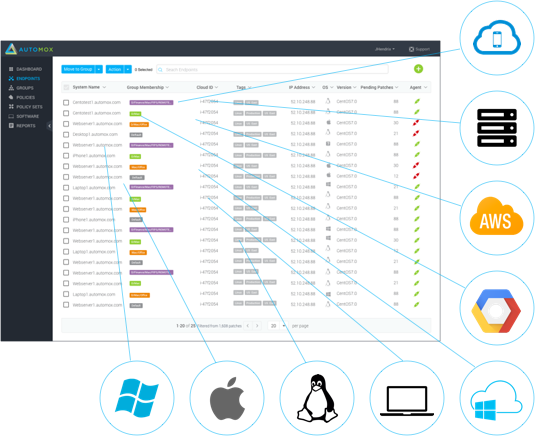
Automox is fully automated and able to patch every operating system (Windows, Mac OSX, and Linux) along with critical applications like Java, Firefox, Adobe, Chrome and others - all from a single dashboard.Our platform enables you to see the vulnerability ...
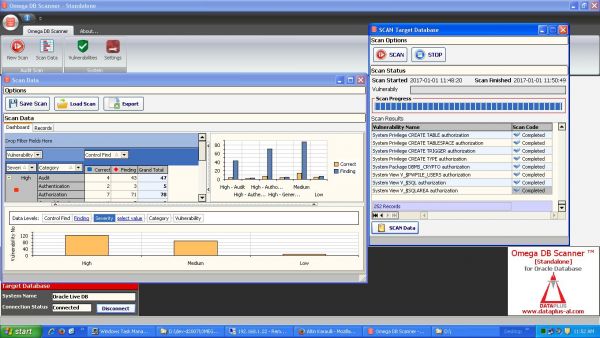
Omega DB Security Reporter is a security auditing and software-only solution for Oracle Databases. Implementing quick reporting, visualisation and documentation of the security posture of the Oracle database on the following security areas: System Priv ...
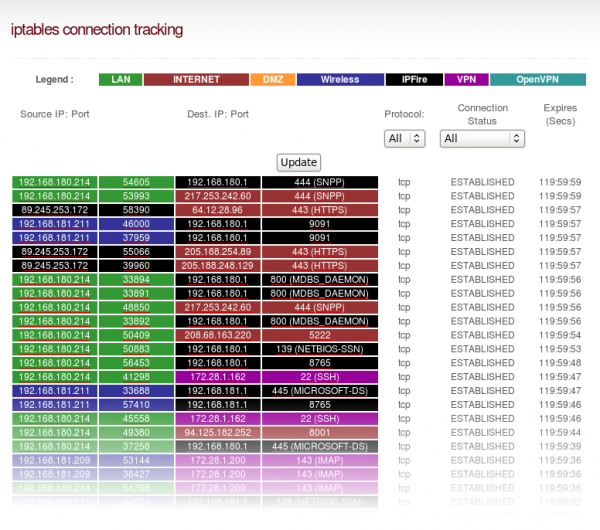
With IPFire you can easily deploy many variations of it, such as a firewall, a proxy server or a VPN gateway. IPFire forms the base of a secure network. It has the power to segment networks based on their respective security levels and makes it easy to cr ...
For phishing, SET allows for sending spear-phishing emails as well as running mass mailer campaigns, as well as some more advanced options, such as flagging your message with high importance and adding list of target emails from a file. SET is Python base ...
Page 22 of 56