Michele M Jordan
The Deep-Secure Chat Guard is one of our family of Content Inspection Guards. It controls the use of Internet standard chat, to allow an organisation to make use of chat without putting sensitive information or critical business processes at risk.   ...
Enjoy the freedom and flexibility of remote working with the peace of mind that your files will remain safe on your secure USB, even in the event of loss or theft with the SafeToGo® Solo. Prevent unauthorised access – with the device’s AES 256-bit XTS en ...
WebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons. You can install and practice with WebGoat in either J2EE (this page) or [WebGoat for .Net] in ASP.NET. In each lesson, users must d ...
Sqlninja is a tool targeted to exploit SQL Injection vulnerabilities on a web application that uses Microsoft SQL Server as its back-end. Its main goal is to provide a remote access on the vulnerable DB server, even in a very hostile environment. It shou ...
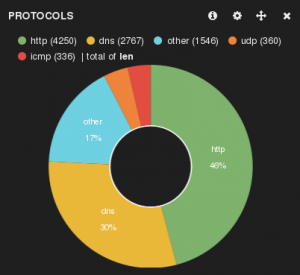
EtherApe is a graphical network monitor for Unix modeled after etherman. Featuring link layer, IP and TCP modes, it displays network activity graphically. Hosts and links change in size with traffic. Color coded protocols display. It supports Ethernet, F ...
Maltego is a platform developed to deliver a clear threat picture to the environment that an organization owns and operates. Maltego’s demonstrates the complexity and severity of single points of failure as well as trust relationships that exist currently ...
Nipper accurately audits the security of firewalls, switches and routers to detect exploitable misconfigurations that pose risk to the network, prioritized by criticality. Applying Nipper’s compliance lens to the findings also provides the evidence needed ...
Ike-scan is a command-line tool that uses the IKE protocol to discover, fingerprint and test IPSec VPN servers. It is available for Linux, Unix, MacOS and Windows under the GPL license.
E-Detective is a real-time Internet interception, monitoring and forensics system that captures, decodes, and reconstructs various types of Internet traffic. It is commonly used for organization Internet behavioral monitoring, auditing, record keeping, fo ...
VIPRE ThreatAnalyzer is a dynamic malware analysis sandbox that lets you safely reveal the potential impact of malware on your organization—so you can respond faster and smarter in the event of a real threat.
VIPRE ThreatIQ gives you the real-time intelligence you need to strengthen your cyber-defense and stop attackers cold. Up-to-the-minute data VIPRE ThreatIQ compiles real-time, global threat intelligence to help you understand where attackers are coming ...
Hakabana is an open source monitoring tool, which allows users to visiualizes Haka network traffic using Kibana and Elasticsearch. It leverages on the Haka framework to capture packets, dissect them and extract various pieces of information from the ...
Security Onion is a Linux distro for intrusion detection, network security monitoring, and log management. It's based on Ubuntu and contains Snort, Suricata, Bro, OSSEC, Sguil, Squert, Snorby, ELSA, Xplico, NetworkMiner, and many other security tools. The ...
Firewalk is an active reconnaissance network security tool that attempts to determine what layer 4 protocols a given IP forwarding device will pass. Firewalk works by sending out TCP or UDP packets with a TTL one greater than the targete ...
Unisys Stealth™ is an innovative, software-based security solution that: ?Conceals communication endpoints making them undetectable to all unauthorized parties inside and outside the enterprise Implements with no disruption to your existing IT infrast ...
Every day, Shadowserver sends custom remediation reports to more than 7000 vetted subscribers, including over 133 national governments (201 National CSIRTs) covering 175 countries and territories, as well as many Fortune 500 companies. These reports are d ...
Kernel Exhcnage EDB Viewer is an Exchange Mailbox viewer tool, that assists system administrators in opening EDB files even in the absence of MS Exchange Servers. Now recover your corrupt exchange database files for free and review their entire contents ...
Nuix Evidence Mover is designed to copy evidence files images from one storage location, to antoher. It creates a hash of the files before and after moving to ensure the data has been copied accurately, and to maintain the chain of custody.
Viewer for standalone files containing Microsoft Outlook Express 4,5 and 6 message database (*.idx/*.mbx/*.dbx), Windows Vista Mail/Windows Live Mail and Mozilla Thunderbird message databases as well as standalone EML files. This application is based on ...
Agent Ransack is a free file search tool for finding files on your PC or network drives. It has a Lite mode, which is FREE for both personal and commercial use but also a Professional mode that includes optional pay-for features. First released in April ...
Page 26 of 56