Directory: Random Listings
The Nessus vulnerability scanner is the world leading vulnerability scanner, with over five million downloads to-date. Nessus is currently rated among the top vulnerability scanners throughout the security industry and is endorsed by professional security ...
A fully automated, active web application security reconnaissance tool. Key features: * High speed: pure C code, highly optimized HTTP handling, minimal CPU footprint - easily achieving 2000 requests per second with responsive targets. * ...
Spam Sleuth monitors your e-mail box behind the scenes and analyzes e- mail messages for spam, Web bugs, phishing scams, and virus characteristics. When your e-mail program gets your e- mail, the spam has already been removed and you can read your message ...
Cisco IOS NetFlow efficiently provides a key set of services for IP applications, including network traffic accounting, usage-based network billing, network planning, security, Denial of Service monitoring capabilities, and network monitoring. NetFlow pro ...
CleanMail is the first anti-spam & anti-virus filter, that was designed from the beginning to provide complete email security - protecting you from spam and all kinds of email-borne malware like viruses and phishing mails - while at the same time maki ...
4 years Full Time / 5 years Sandwich Course
Bitwarden makes it easy to generate, store, and secure unique passwords from any location or device. Bitwarden is Open Source and third party audited. Install and Sync all of your devices Secure cloud syncing features allow you to access your data from ...
Blooover II is the successor of the very popular application Blooover. After 150000 downloads of Blooover, a new version of this mobile phone auditing toool is on its ready. Besides the BlueBug attack, Blooover II supports the HeloMoto attack (which is qu ...
CoursesOnline offers professionals the opportunity to hone their cyber security skills via a wide selection of online learning courses. There are options available for those new to the sector and likewise with those with more experience. The courses are p ...
ISACA (Information Systems Audit and Control Association and Foundation), a recognized global leader in IT governance, control and assurance, is dedicated to offering the most dynamic and inclusive conferences to keep you abreast of the latest advances in ...
Complete line-of-defense against the most extreme forms of malware and cyber threats, Ad-Aware Pro Security provides the most advanced anti-spyware and antivirus detection and threat blocking algorithms, complemented with a powerful two-way firewall, web ...
Originaly based on Prelude OSS project, Prelude SIEM provides open-source excellence in quality and performance. From this strong base, the Prelude team has designed ergonomic interface and added many features for the most demanding security teams. Among ...
SACMAT is a successful series of symposiums that continue the tradition, first established by the ACM Workshop on Role-Based Access Control, of being the premier forum for presentation of research results and experience reports on leading edge issues of a ...
Citrix Web App and API Protection service offers holistic, proven, and layered protection against known and zero-day application attacks. The cloud-based service keeps all application types secure across multi-cloud with a web app firewall, bot management ...
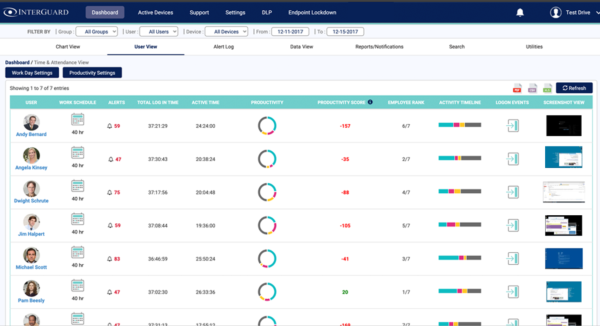
InterGuard’s employee monitoring software lets you track all employees activity from any endpoint - even when they work from home. Monitoring employee computer activity helps you proactively identify which employees are being productive and how much time ...
Sucuri is a managed security service provider for websites. Their cloud-based platform gives you complete website security, including an antivirus and firewall for your website. Monitors for security incidents, fixes website hacks, and protects your site ...
EdenWall is the hardware firewall developed by INL. It provides authentication and user-based network flow management. Thanks to EdenWall, network filtering policies based on actual user identity is now possible. Sole IP-based filtering time is over! ...
Blancco Removable Media Eraser?is?deliverable?as a simple desktop application,?or?an?MSI package delivered to multiple users, allowing single data erasure processes or simultaneous erasure. Achieve Compliance?Securely erase removable media to improve dat ...
A Java Hijacking tool for web application session security assessment. A simple Java Fuzzer that can mainly be used for numeric session hijacking and parameter enumeration.
The extremely easy handling of gateProtect?s solution reduces the potential for these security flaws to a minimum, while still incorporating the latest security standards. If desired, a fully automatic wizard creates a working default configuration for ea ...