Directory: Random Listings
The Conference, co-sponsored since 1998 by the NYS Office of Cyber Security and Critical Infrastructure Coordination (CSCIC) and the New York State Forum, added a new government sponsor, the NYS Center for Information Forensics and Assurance (CIFA) at the ...
Hosted CanIt® automatically protects email from Spam. Ads, fraud schemes, porn, viruses, phishing attempts... if it's junk e-mail, Roaring Penguin's Hosted CanIt will stop it before it reaches your mail server without the need for installing any softw ...
ShmooCon is an annual East coast hacker convention hell-bent on offering three days of an interesting atmosphere for demonstrating technology exploitation, inventive software & hardware solutions, and open discussions of critical infosec issues. The first ...
Click, Deploy, Protect Cloudflare’s WAF enables protection against malicious attacks that aim to exploit vulnerabilities including SQLi, XSS and more. To quickly protect against new and zero-day vulnerabilities, toggle to turn on Cloudflare’s Managed Rul ...
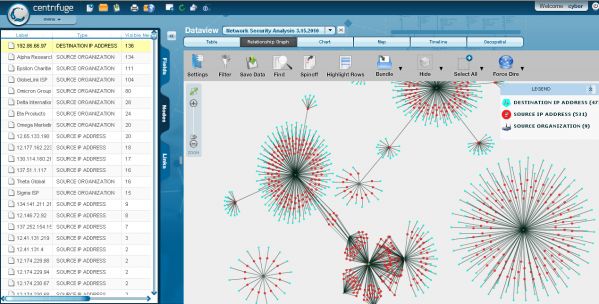
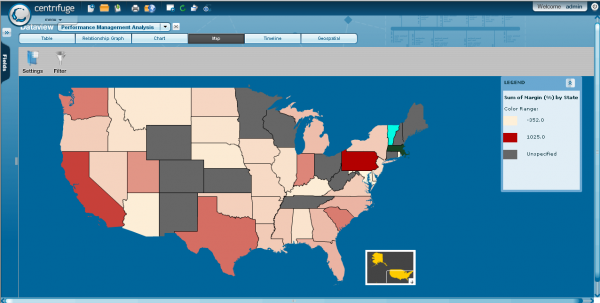
Centrifuge Analytics makes it easy to harness the power of your data, visualize discoveries, collaborate to draw conclusions and make effective predictions that will have an immediate impact to your organization. Data Discovery Not Data Processing ...
Secure Firewall helps you plan, prioritize, close gaps, and recover from disaster—stronger. Turn intent into action Unify policy across your environment and prioritize what’s important. Having security resilience is about shoring up your architecture ag ...
GlobalNet Training’s 4-day Cisco Authorized* CCNA Wireless® Training Boot Camp, taught by CCSI Todd Lammle, is a high-energy, instructor-led course that provides system engineers and field engineers with a more in-depth understanding of the latest Cisco w ...
Mobile security and complexity don’t have to go hand in hand. Check Point Capsule is one seamless solution that addresses all your mobile security needs. Capsule protects your mobile devices from threats, provides a secure business environment for mobile ...
4 years Full Time / 5 years Full Time
The Stealth SM2020 is the most advanced portable speech protection system which protects you against listening and recording devices. The Stealth SM2020 creates sound barrier interference which masks your speech and any sound to be extremely difficult or ...
WebMarshal is a Secure Web Gateway - a comprehensive solution which addresses the full spectrum of Web-based security threats as well as the many requirements and issues that arise in managing workplace Internet use. WebMarshal is the answer to managing a ...
Sqlninja is a tool targeted to exploit SQL Injection vulnerabilities on a web application that uses Microsoft SQL Server as its back-end. Its main goal is to provide a remote access on the vulnerable DB server, even in a very hostile environment. It shou ...
Security-Database provides free service focused on vulnerability and tools watch. The vulnerability database relies on open standards as CVE, CVSS, CWE, CPE and OVAL. The ToolsWatch process supplies the security community with the latest auditing and pene ...
Omega Core Audit provides a software security solution to help customers approach the complex and difficult security challenges in Oracle Database Systems - protecting against outsider and/or insider threats, unauthorized access and enforcing duty separat ...
btscanner is a tool designed specifically to extract as much information as possible from a Bluetooth device without the requirement to pair. A detailed information screen extracts HCI and SDP information, and maintains an open connection to monitor the R ...
The StealthWatch sensor appliance provides fast, accurate monitoring for unexpected or unauthorized network behavior. Using flow-based architecture it provides continuous, real-time network traffic monitoring and instant identification of attack
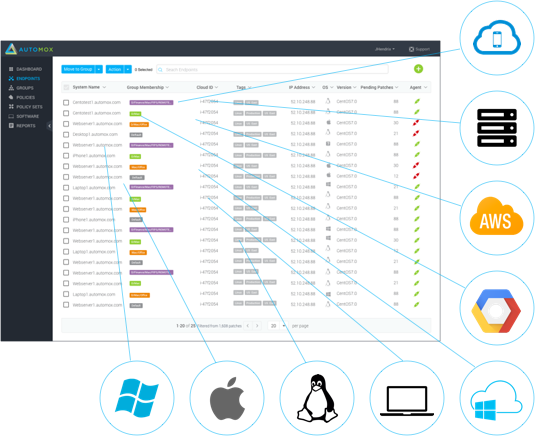
Automox is fully automated and able to patch every operating system (Windows, Mac OSX, and Linux) along with critical applications like Java, Firefox, Adobe, Chrome and others - all from a single dashboard.Our platform enables you to see the vulnerability ...
mac-robber is a digital investigation tool that collects data from allocated files in a mounted file system. This is useful during incident response when analyzing a live system or when analyzing a dead system in a lab. The data can be used by the mactime ...
Intrusion Prevention System (IPS) for ssh (default port 22), this IPS responds to the suspicious activity by setting the linux firewall (iptables) to block network traffic from the suspected malicious source. Suspicious activity is determined via auth or ...
Grabber is a web application scanner. Basically it detects some kind of vulnerabilities in your website. Grabber is simple, not fast but portable and really adaptable. This software is designed to scan small websites such as personals, forums etc. absol ...