Directory: Random Listings
A multi-layered on-premises solution that protects against advanced email threats. SonicWall Email Security is ideal for organizations that need a dedicated on-premises solution. SonicWall’s solution can be deployed as a hardened physical appliance, robu ...
The GB-2000X Firewall Appliance's powerful hardware design meets the needs of SME corporations with complex Internet connectivity and heavy network traffic demands. GTA's GB-2000X Firewall Appliance provides powerful, enterprise-level security with compre ...
BUFFERZONE is a virtual container that protects any content source that you define as potentially insecure including web browsers, email, Skype, FTP and even removable storage. You are able to definite granular containment poloicies according to network s ...
Logsurfer is a program for monitoring system logs in real-time, and reporting on the occurrence of events. It is similar to the well-known swatch program on which it is based, but offers a number of advanced features which swatch does not support. Logsur ...
The Cisco FirePOWER Next-Generation IPS (NGIPS) solution integrates: Real-time contextual awareness Intelligent security automation Superior performance with industry-leading network intrusion prevention Cisco FirePOWER NGIPS features ...
4 years Sandwich Course
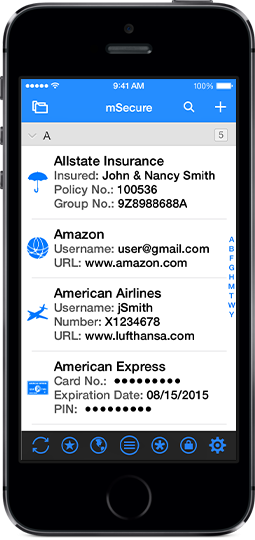
mSecure is a leading password manager and digital wallet. Your data is safe in mSecure because it uses 256bit Blowfish encryption to protect your most personal information, account numbers, usernames, passwords and more! Guard your passwords with confi ...
FTK is a digital investigations solution built for speed, stability and ease of use. It quickly locates evidence and forensically collects and analyzes any digital device or system producing, transmitting or storingdata by using a single application from ...
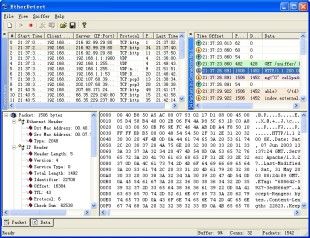
This protocol analyser will Organize captured packets in a connection-oriented view. Capture IP packets on your LAN with nearly no packets losing. Its real-time analyzer enables on-the-fly content viewing while capturing and analyzing, parse and decode an ...
tiger is a set of scripts that scan a Un*x system looking for security problems, in the same fashion as Dan Farmer's COPS. 'tiger' was originally developed to provide a check of UNIX systems on the A&M campus that want to be accessed from off campus (clea ...
An extensible network forensic analysis framework. Enables rapid development of plugins to support the dissection of network packet captures. Key features:Robust stream reassemblyIPv4 and IPv6 supportCustom output handlersChainable decoders
Omega Core Audit provides a software security solution to help customers approach the complex and difficult security challenges in Oracle Database Systems - protecting against outsider and/or insider threats, unauthorized access and enforcing duty separat ...
nTAPs are passive, full-duplex devices, offering complete visibility to monitoring devices regardless of traffic level. They work with the leading management tools for quick and easy deployment. nTAPs are transparent for monitoring critical links, and pro ...
The worlds security professionals converge to discuss new technology, and share best practices. The most significant new discoveries, technologies, and products will be presented at the annual EUSecWest conference, brought to you by the organizers of PacS ...
The only way to reliably detect wireless protocols is to use preselected chips (saw filters) which attenuate all other signals except the desired ones. This is the method implemented in the Protect Stealth 1207i which has 6 channels for different frequenc ...
The LANenforcer 2024 and 2124 LAN Security Appliances transparently integrate into existing network infrastructures, sitting between existing switches at the access and distribution layers. The LANenforcer Appliance is an ideal solution for organizations ...
Qualys Cloud Platform, previously known as QualysGuard, consists of integrated apps to help organisations simplify security operations and lower the cost of compliance by delivering critical security intelligence on demand and automating the full spectrum ...
The manual audit of a firewall policy is a very subjective and laborious process which is dependent on the user?s skill set and experience. The AlgoSec Firewall Analyzer (FA) automatically and non-intrusively analyzes a firewall?s policy. Within a matter ...
Experience in-depth coverage of Linux and Unix security issues. Examine how to mitigate or eliminate general problems that apply to all Unix-like operating systems, including vulnerabilities in the password authentication system, file system, virtual memo ...
1 year Full Time