Directory: Random Listings
UMRA is a complete User Management System that simplifies Active Directory Management across all your systems. While managing user account and authorization processes in Active Directory and adjacent systems, UMRA also offers delegation of user account ma ...
The LUCY Social Engineering Suite and Malware Testing Suite (or CYBERSECURITY CRASH TEST DUMMY) facilitate multiple application areas. They can be used for: – People testing and education – Technology assessments – An inoffensive penetration test sho ...
GajShield SecureGate Enterprise Firewall is a powerful, enterprise class ICSA certified Stateful Inspection Firewall protecting networks from intrusions. GajShield SecureGate Enterprise Firewall provides protection against DOS, DDOS, viruses and worms and ...
NetStumbler is a Windows utility for 802.11b based wireless network auditing
MOBILedit Forensic is a phone extractor, data analyzer and report generator all in one solution. A powerful 64-bit application using both the physical and logical data acquisition methods, MOBILedit Forensic is excellent for advanced application analyzer, ...
3 years Full Time / 4 years Sandwich Course
With its web browser based interface, the ProShield v1000 can be easily set up, configured and managed from any computer using a familiar interface. The complexities of configuring firewall and VPN devices has been simplified by our logical, intuitive, ea ...
Darik's Boot and Nuke ("DBAN") is a self-contained boot floppy that securely wipes the hard disks of most computers. DBAN will automatically and completely delete the contents of any hard disk that it can detect, which makes it an appropriate utility for ...
The course is ideal for individuals who conduct computer security reviews, computer based internal audits and computer related investigations. The participants in this course typically are employed by government agencies, law enforcement agencies, Fortune ...
Wide-spectrum: SpamAssassin uses a wide variety of local and network tests to identify spam signatures. This makes it harder for spammers to identify one aspect which they can craft their messages to work around. Free software: it is distributed ...
The SecurityTube Linux Assembly Expert, or SLAE, is an online course and certification which focuses on teaching teh basics of 32-bit assembly language for the Intel Architecture (IA-32) family of processors of the Linux platform and applying it to infose ...
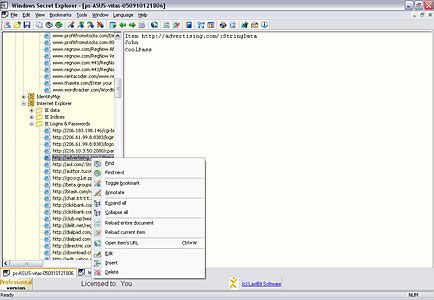
Using Secret Explorer you will be able to locate hidden information in any Windows-based system. This includes form AutoComplete data offered by Internet Explorer every time you enter something into an form on a web page; various Internet passwords: passw ...
4 Years
SecureLogix delivers the world?s first Voice Firewall to secure corporate resources from telephony borne attacks and security risks, and defend your VoIP and legacy voice systems from service disruption and abuse, unauthorized access, toll fraud, and othe ...
2 years Full Time
Core Protection for Your PC 10 years of malware experience combined in one dynamic application. Ad-Aware - Anniversary Edition offers radically improved performance and efficiency, along with comprehensive malware protection. With real-time monitoring, ...
Rifiuti2 analyses recycle bin files from Windows. Rifiuti2 can extract file deletion time, original path and size of deleted files. For more ancient versions of Windows, it can also check whether deleted items were not in recycle bin anymore (that is, eit ...
east-tec InvisibleSecrets is a steganography and file encryption software that allows you to encrypt file and folder structures that contain confidential data and hide files, making it completely invisible to any user. Other useful features include: Powe ...
RememBear is a friendly app that saves and autofills your passwords to save you time and keep you safe online. Benefits: Friendly, approachable design Log in faster - let a Bear type your passwords and login to website with one click Faster on ...
4 years Sandwich Course