Directory: Random Listings
DEV522: Defending Web Applications Security Essentials is intended for anyone tasked with implementing, managing, or protecting Web applications. It is particularly well suited to application security analysts, developers, application architects, pen test ...
The Offensive Security Web Expert (OSWE) is an entirely hands-on web application penetration testing security certification. The OSWE challenges the students to prove they have a clear and practical understanding of the web application assessment and hack ...
When it comes to security, manual monitoring just doesn't cut it. For true policy enforcement, you need something that doesn't ever get tired, bored, distracted or lazy. The active dashboard in Sentinel automates the security monitoring of IT systems and ...
2 years Full Time
Security Onion is a Linux distro for intrusion detection, network security monitoring, and log management. It's based on Ubuntu and contains Snort, Suricata, Bro, OSSEC, Sguil, Squert, Snorby, ELSA, Xplico, NetworkMiner, and many other security tools. The ...
Summercon is our chance to get together, talk to each other face-to-face, and swap information about innovations, trends, practices, and rumors in the field of computer security. We welcome all walks of life and all sides of the debate to Summercon: hacke ...
PhoneSweep is a robust multiline scanner that scales to meet specific requirements. It classifies answering devices as Phones, Faxes or Modems and identifies over 470 types of system. The scans can be conducted in Connect, Identify or Penetrate modes depe ...
Our SA Series Secure Access Appliances offer: * Market-leading, single SSL VPN security platform to serve all remote access needs * Clientless access to enterprise applications and resources * Best-in-class endpoint security, granular acc ...
TrainACE runs CISSP training classes at two locations in the Baltimore - Washington metropolitan area, as well as online: Ashburn, VA and Greenbelt, MD.
WE DON'T SELL THIS PRODUCT, check out the site above There is nothing worse than spending too many hours in a hot and cramped server room, except that is, when you crack open a warm can of Red Bull. This fridge will help engineers keep their stash of R ...
Content Analysis delivers multi-layer file inspection to better protect your organization against known and unknown threats. Unknown or suspicious content from sources like Proxy, Messaging Gateway, or other tools is delivered to Content Analysis for deep ...
CD/DVD Inspector reads all major CD and DVD filesystem formats including ISO-9660, Joliet, UDF, HSG, HFS and HFS+. When the disc being examined contains more than a single filesystem, all filesystems found are displayed. Multiple filesystems a ...
Feature-rich, reliable, lightweight log collectors. Rock solid log collection is both a compliance and security imperative. Lightweight – Under 5% of CPU and 20 megs of memory Compliance – Gather data needed for PCI DSS, SOX, GDPR, HIPAA. NISPOM, PIPEDA ...
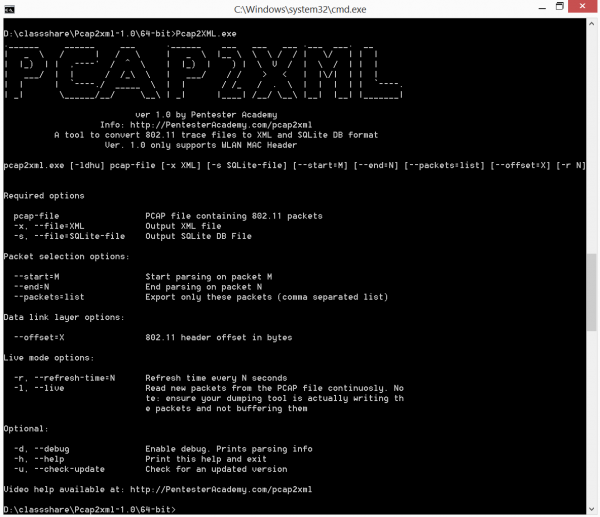
PCAP2XML is a tool suite which takes 802.11 PCAP trace files as input and can convert them into XML or SQLITE representations. This allows a pentester to run arbitrary queries on the packet header fields. Why do we need this? Wireshark is great when it ...
CYBERsitter 9.0 is designed primarily for home, educational and small business use. Even though CYBERsitter has been designed to be easily installed and used by the most inexperienced users, there are plenty of advanced features for power users too. Ne ...
Zeek has a long history in the open source and digital security worlds. Vern Paxson began developing the project in the 1990s under the name “Bro” as a means to understand what was happening on his university and national laboratory networks. Vern and the ...
FlowScan analyzes and reports on Internet Protocol (IP) flow data exported by routers. Consisting of Perl scripts and modules, FlowScan binds together (1) a flow collection engine (a patched version of cflowd), (2) a high performance database (Round Robin ...
HCL BigFix is an endpoint management platform which enables the automation of discovery, management and remediation - whether its on premise, virtual, or cloud - regardless of operating system, location or connectivity. Keep all of your endpoints patched ...
AppScan delivers application security testing tools to ensure your business, and your customers, are not vulnerable to attacks. Detect application vulnerabilities before they become a problem, remediate them and ensure compliance with regulations. Four pr ...
The CSSA Instructor-led Training is designed to reinforce the foundational knowledge in the SonicWALL Technical e*Training courses. These courses provide the hands-on experiential training that will enhance problem solving and provide dynamic feedback in ...