Directory: A-Z
SEC617 will give you the skills you need to understand the security strengths and weaknesses in wireless systems. In this course, you will learn how to evaluate the ever-present cacophony of Wi-Fi networks and identify the Wi-Fi access points and client d ...
Wireless Protector is windows software that automatically disables wireless 802.11 / Broadband devices on computers that connected to the network LAN and re-enable the devices when the LAN cable is disconnected from the protected compu ...
Elcomsoft Wireless Security Auditor examines the security of your wireless network by attempting to break into the network from outside or inside. Elcomsoft Wireless Security Auditor works completely in off-line, undetectable by the Wi-Fi network being pr ...
Wireless technology fundamentally changes accepted security paradigms. With the pervasive deployment of wireless technology, attackers have latched on with sophisticated and effective techniques to exploit wireless systems at work, at home, or on the road ...
Formerly Ethereal. Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries, Features Include: Deep inspection of hundreds of protocols, with more being added all the time L ...
WLAN Expert is a wireless client utility designed to work with the PRISM chipset by Intersil. The Linksys WPC11 is the only client card I've tested, although many manufacturers use this silicon. Intersil counts Alcatel, Cisco, Compaq, Nokia, Nortel, Samsu ...
WP Security Scan checks your WordPress website/blog for security vulnerabilities and suggests corrective actions such as: 1. Passwords 2. File permissions 3. Database security 4. Version hiding 5. WordPress admin protection/security ...
The WPScan CLI tool is a free, for non-commercial use, black box WordPress security scanner written for security professionals and blog maintainers to test the security of their sites.
What Will You Learn? Understand the key security features of the C++ language, the common security pitfalls developers make and how to build secure and reliable enterprise applications using C++. Students are lead through hands on code examples that highl ...
What Will You Learn? Understand the key security features of the J2EE platform, the common web security pitfalls developers make and how to build secure and reliable web applications using Java. Students are lead through hands on code examples that highli ...
Verify connectivity to a particular device on your network. Quantitatively test data connections between your computer and a remote system. Trace the path to a network host or device. Obtain information on host names and IP addresses. Scan your ne ...
IBM X-Force Exchange is a cloud-based threat intelligence platform that allows you to consume, share and act on threat intelligence. It enables you to rapidly research the latest global security threats, aggregate actionable intelligence, consult with exp ...
Enova X-Wall is an embedded hardware Real-time Crypto System ASIC (Application Specific Integrated Circuit) engineered specifically to handle high throughput disk I/O and providing real-time encryption and decryption using DES (Data Encryption Standard),3 ...
XCon is an Information Security Conference organized by the XFocus Security Team which brings together information security enthusiasts and professionals from all parts of China, and the world.
Despite the prevalence of broadband Internet connectivity, dial-up modems still play a crucial role in most medium to large organisations. With the increasing computerisation of infrastructure devices (network switches, HVAC, power management...) modems p ...
XP firewall control uses all the present abilities of the firewall and extends them with application level security model. XP firewall control introduces per-application named security zones and allows security zone management at application level driven ...
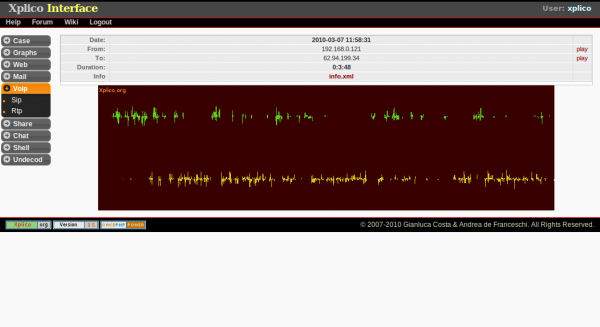
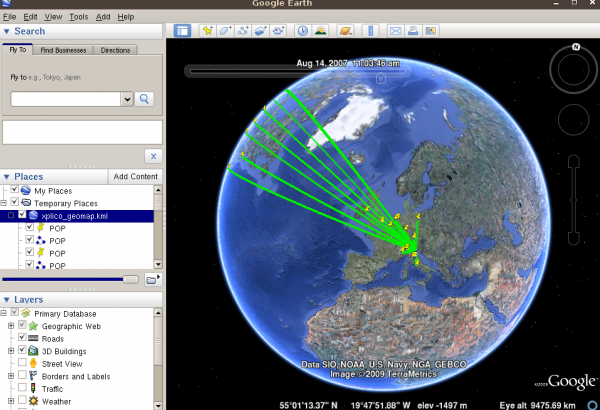
The goal of Xplico is extract from an internet traffic capture the applications data contained. For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on. Xplico ...
The XSR 3000 Series Security Router delivers simple and powerful enterprise WAN networking by combining comprehensive IP routing features; a broad range of WAN interfaces; and a rich suite of security functions, including site-to-site and remote access Vi ...
Cross Site "Scripter" is an automatic -framework- to detect, exploit and report XSS vulnerabilities in web-based aplications. It contains several options to try to bypass certain filters, and various special techniques of code injection.
Zabbix is listed here for it's Network Mapping and visualisation capabilities, but it is truly a Monitoring application. Auto discovery * Discovery by IP range, services and SNMP * Automatic monitoring of discovered devices