Directory: A-Z
TThe goal of this seven-day accelerated course is to provide information security professionals a fully-immersed, zero-distraction, all-inclusive CISSP CBK training and certification experience. Our CISSP Firebrand Training encompasses the (ISC)2 CISSP CB ...
Barracuda Web Application Firewall The Barracuda Web Application Firewall protects applications, APIs, and mobile app backends against a variety of attacks including the OWASP Top 10, zero-day threats, data leakage, and application-layer denial of ...
Trispen's @TheOffice.Wherever! provides Secure Remote Access by letting you virtually plug into your Office Network from anywhere in the world. Any PC with Internet Access can now be used as if it is directly connected to your Office LAN! There are so ...
The Linksys 10/100 4-Port VPN Router is an advanced Internet-sharing network solution for your small business needs. Like any router, it lets multiple computers in your office share an Internet connection. But the unique dual Internet ports on the 10/100 ...
WE DON'T SELL THIS PRODUCT, check out the site above There is nothing worse than spending too many hours in a hot and cramped server room, except that is, when you crack open a warm can of Red Bull. This fridge will help engineers keep their stash of R ...
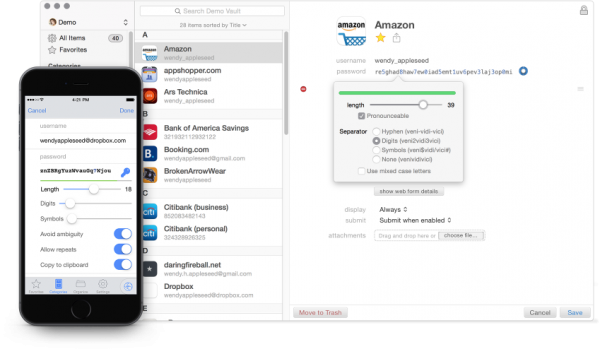
1Password gives you the security you need in today's online world without slowing you down. 1Password makes you more productive while simultaneously increasing your security with strong, unique passwords for all your accounts and keeps all of your importa ...
The 24th Chaos Communication Congress (24C3) is the annual four-day conference organized by the Chaos Computer Club (CCC) in Berlin, Germany. First held in 1984, it since has established itself as ?the European Hacker Conference?. Lectures and workshops o ...
360-FAAR (Firewall Analysis Audit and Repair) is an offline, command line, Perl firewall policy manipulation tool to filter, compare to logs, merge, translate and output firewall commands for new policies, in Checkpoint dbedit, Cisco PIX/ASA or Netscreen ...
WE DON'T SELL THIS PRODUCT, check out the site above For the ultimate geeky romantic getaway, consider a server room! Impress your other half by opening up your rack and pulling out a nice fruity Chianti. As you shout sweet nothings to each other ...
The UNIX family of operating systems, including the increasingly used Linux versions, is prized by IT professionals for its flexibility and openness. Vulnerabilities in standard configurations, however, can make UNIX systems susceptible to security threat ...
4Secure offers a flexible line of data diode cyber security products. Customers can choose from the appropriate hardware platform, which includes a base software package, and then select optional add-on software modules (at an additional cost) to meet the ...
Access Assurance Suite is an intelligent identity and access management (IAM) software solution that enables organizations to deliver informed provisioning, meet ongoing regulatory compliance, and leverage actionable analytics for improved identity govern ...
The Complete Remote Access VPN * Multiple access methods to securely connect to your email, files and applications * Enterprise-class features with simple deployment and unparalled ease-of-use * Installs on existing server without having ...
3 years Full Time
ACNS is an annual conference concentrating on current developments that advance the areas of applied cryptography and its application to systems and network security. The goal is to represent both academic research works as well as developments in industr ...
ActivTrak is more than just an insider threat management solution. It gives you a zoomed-in perspective of what your employees actually do in their digital workspaces. For example, it monitors what applications they use and how they divide their time betw ...
Acunetix has pioneered the web application security scanning technology: Its engineers have focused on web security as early as 1997 and developed an engineering lead in web site analysis and vulnerability detection. Acunetix Web Vulnerability Scanner inc ...
Complete line-of-defense against the most extreme forms of malware and cyber threats, Ad-Aware Pro Security provides the most advanced anti-spyware and antivirus detection and threat blocking algorithms, complemented with a powerful two-way firewall, web ...
Core Protection for Your PC 10 years of malware experience combined in one dynamic application. Ad-Aware - Anniversary Edition offers radically improved performance and efficiency, along with comprehensive malware protection. With real-time monitoring, ...
Computer networks are built to support business functionality and beyond communication the result of business is data. The data important to your business is your company's digital assets; it needs organisation, maintainenance and above all protection fro ...