Directory: Random Listings
Spiceworks! The free “everything IT” network management software. Inventory Your Network Monitor Your Network Run an IT Help Desk Manage Configuration Changes Map Your Network With Spiceworks you can: * Create a network map of your IT network * See networ ...
With the Clearswift SECURE Email Gateway installed, your organisation can be confident that it is protected from digital threats and data leaks while employees communicate freely by email.Policy Controls ...
NTT Application Security provides complete web application security at a scale and accuracy unmatched in the industry. No matter how many websites or how often they change, we can concurrently scan an unlimited number of sites without slowing you down. Wo ...
Sqlninja is a tool targeted to exploit SQL Injection vulnerabilities on a web application that uses Microsoft SQL Server as its back-end. Its main goal is to provide a remote access on the vulnerable DB server, even in a very hostile environment. It shou ...
snarl is a bootable forensics ISO based on FreeBSD and using @stake's autopsy and task as well as scmoo's list of known good checksums. Once you boot the iso just log in as root there is no password. You will boot into a dialog driven menu. select the fir ...
DirX Access is a comprehensive access management and identity federation solution for protecting Web services and Web applications against unauthorized access. User access is controlled and enforced on the basis of central role-based security policies ...
Cloudbric WAF+ is a fully managed web security solution for any company or organization with a website, providing protection against the full spectrum of web threats. WAFCloudbric WAF provides a fully managed web security for enterprises and SMBs with ...
4 years Sandwich Course
Packet filtering is the selective passing or blocking of data packets as they pass through a network interface. The criteria that pf(4) uses when inspecting packets are based on the Layer 3 (IPv4 and IPv6) and Layer 4 (TCP, UDP, ICMP, and ICMPv6) headers. ...
3 years Full Time
Blueprinting is a method to remotely find out details about bluetooth-enabled devices. Blueprinting can be used for generating statistics about manufacturers and models and to find out whether there are devices in range that have issues with Bluetooth sec ...
Worried about what's online? Internet filth wipes away easily with Netmop The Only Total Family Filter - Netmop not only protects your children, it protects you too. Tamper-Proof - Even tech-savvy users can't get around Netmop. Membership Benefits - Ou ...
Cisco Cloud Web Security (CWS) provides industry-leading security and control for the distributed enterprise. Users are protected everywhere, all the time when using CWS through Cisco worldwide threat intelligence, advanced threat defense capabilities, an ...
An automated and centralized identity management platform is the only viable means for delivering consistent service and maintaining control over application security. As the only Identity Lifecycle Management solution built on a platform that incorporate ...
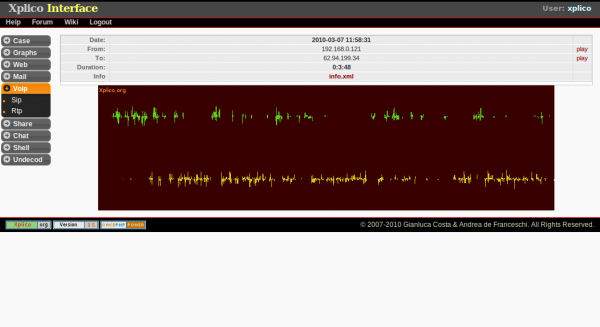
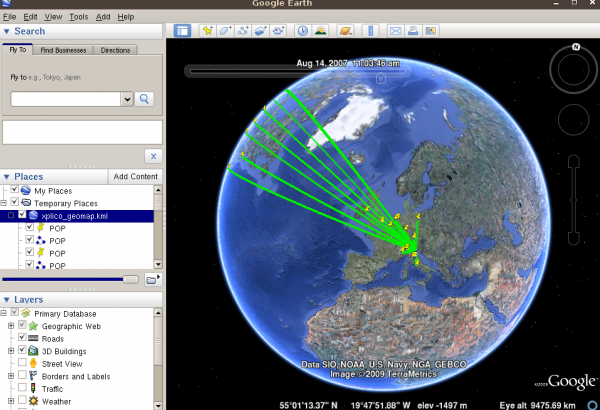
The goal of Xplico is extract from an internet traffic capture the applications data contained. For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on. Xplico ...
You will learn the skills required to reverse-engineer applications to find vulnerabilities, perform remote user application and kernel debugging, analyze patches for one-day exploits, perform advanced fuzzing, and write complex exploits against targets s ...
Exports to NetFlow
Tighten security with Firewall as a Service Legacy firewalls can protect the company’s internal perimeter, but they can’t ensure its safety across hybrid clouds. Perimeter 81's Firewall as a Service ensures that only authorized users can connect to your ...
The Guardian Digital Secure VPN Suite is a powerful Virtual Private Network solution for business operations on the Internet. Combined with a lightweight network intrusion detection system, organizations can protect their corporate online assets while mon ...