Directory: A-Z
3 years Full Time
Prepare every employee with phishing simulations and training Stop dreading the day a phishing attack slips past your cyber defenses. Get the peace of mind from knowing your employees are prepared if it happens. Choose from 1,000+ realistic phishing tem ...
The Ingate SIParator / Firewall SBC RTS-FW The Ingate SIParator is a powerful, flexible and cost-effective Enterprise Session Border Controller (E-SBC) for SIP connectivity, security and interoperability, such as connecting PBXs and Unified Communication ...
This multi-purpose Firewall readies you for the future through Deep Packet Inspection, unique multi-platform support, and market-leading IPSec VPN support. Its unparalleled network monitoring turns you into an security professional with unique real-time i ...
Complete "Deep Packet Inspection" Security Provides unprecedented broad-scoped security and enables the network administrator to effortlessly eliminate (D)DoS attacks, trojans, worms, SYN floods, ICMP floods, port-scanning, e-borne viruses, executable e-m ...
Transparent, standards-based cross-platform unified IPSec technology, extends the InJoy Firewall? with capability of building VPN's and secure channels ? allowing corporations to deploy it either as a VPN Gateway or as a secure VPN Client.
Exports to SFlow
The Innominate mGuard products offer extensive security functions such as VPNs (Virtual Private Networks), firewall and optional virus protection (powered by Kaspersky) ? regardless of the computer platform used. With the Innominate Security Configuration ...
The State Key Laboratory of Information Security (SKLOIS) of China is one of the largest research groups in China in the area of Information Security and Cryptology. The SKLOIS conference on information security and cryptology (Inscrypt, formerly CISC) wi ...
Built and vetted by expertsInsightIDR has internal and external threat intel for our post-perimeter era, and the world’s most used penetration testing framework Metasploit. We do relentless research with Projects Sonar and Heisenberg. And because “we drin ...
integrit is an alternative to file integrity verification programs like tripwire and aide. It helps you determine whether an intruder has modified a computer system. Without a system like integrit, a sysadmin can't know whether the tools he/she uses to in ...
Intercept X Endpoint Features Endpoint Detection and Response (EDR)Automatically detect and prioritize potential threats and quickly see where to focus attention and know which machines may be impacted Extended Detection and Response (XDR)Go beyond the ...
OverviewIntercept X for Mobile protects your Android device without compromising performance or battery life. Real-time synchronization with SophosLabs ensures that your mobile device is always protected from the latest malware and online threats – just l ...
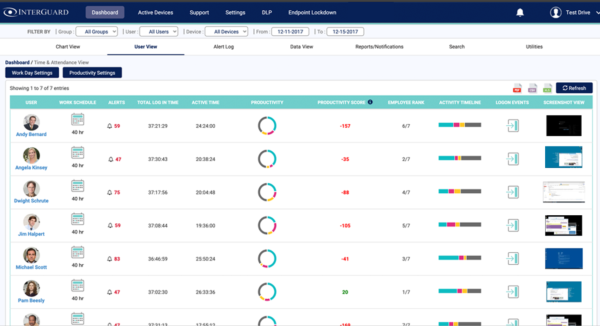
InterGuard’s employee monitoring software lets you track all employees activity from any endpoint - even when they work from home. Monitoring employee computer activity helps you proactively identify which employees are being productive and how much time ...
The main goal of this conference is to promote research on all aspects of network security and cryptology.
Information assurance and security has become an important research issue in networked and distributed information sharing environments. Finding effective ways to protect information systems, networks and sensitive data within the critical information inf ...
If2k-Only V2.3.0 Security matters ! Lockout adware, spyware, unauthorized downloads, viruses, p2p activity, pornography, legal liabilities -lockout everything except what you determine you want ! The future of your business will depend upon ...
Win the battle against email threats with Trend Micro’s InterScan Messaging Security Suite. It protects your network by integrating award-winning antivirus with zero-day protection, powerful anti-spam, and anti-phishing along with content filtering for co ...
Packet Analysis and Intrusion Detection 5 Day You'll learn how to properly read and interpret packets and packet headers including IP, TCP, ICMP, and UDP. You will learn how to distinguish between normal, abnormal, and malicious traffic. You will also c ...
Computer Forensics Core Competencies 5day This computer forensics training is meant for those without any previous experience with computer forensics. The student will be introduced to concepts and techniques that every computer forensics practitioner mu ...