Directory: A-Z
The MSA security appliance is based on new Celestix?s Scorpio-X appliance hardware platform. Specifically designed for network security, Scorpio-X, with its great capabilities and high-speed I/O device, has the best price/performance hardware platform to ...
Lawfully access locked devices with easeBypass pattern, password or PIN locks and overcome encryption challenges quickly on popular Android and iOS devices Support for the broadest range of devicesCollect data from mobile phones, drones, SIM Cards, SD ca ...
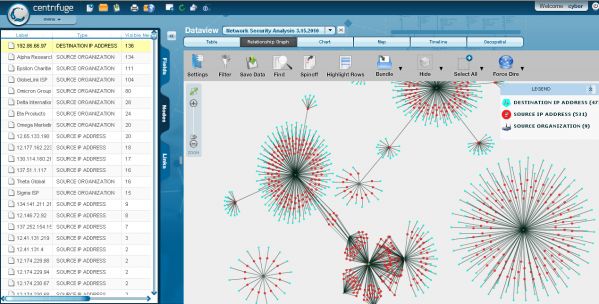
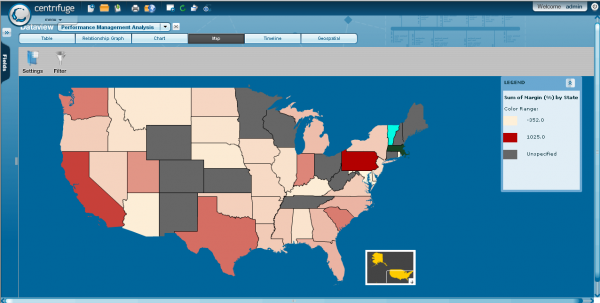
Centrifuge Analytics makes it easy to harness the power of your data, visualize discoveries, collaborate to draw conclusions and make effective predictions that will have an immediate impact to your organization. Data Discovery Not Data Processing ...
Cerebral is an AI-powered security platform that integrates User & Entity Behavior Analytics (UEBA) with User Activity Monitoring (UAM), allowing rapid Data Breach Response (DBR). The ability to hunt threats by proactively recognizing signs of risk, l ...
The program is designed to be about 70% hands-on and will give you plenty of time to practice and learn the skills necessary to conduct forensic examinations. There are a maximum of 9 students per instructor, so there will be plenty of individual instruct ...
The Certified Digital Forensics Examiner program is designed to train Cyber Crime Investigators. Students are taught electronic discovery and advanced investigation techniques. This course is essential to anyone encountering digital evidence while con ...
In this CEH training course, you are provided with the foundational knowledge needed to pass the EC-Council Certified Ethical Hacker (CEH v11) exam. You will learn how to deploy tools and techniques to protect your network through hands-on labs that mimic ...
Certified Penetration Testing Engineer graduates will obtain real world security knowledge enabling them to recognize vulnerabilities, exploit system weaknesses, and safeguard organizations against threats. Graduates will learn the art of Ethical Hacking ...
The CSSA Instructor-led Training is designed to reinforce the foundational knowledge in the SonicWALL Technical e*Training courses. These courses provide the hands-on experiential training that will enhance problem solving and provide dynamic feedback in ...
CERTStation provides tools enabling users to receive actionable security intelligence in a meaningful and timely manner. We are dedicated to providing a comprehensive enterprise view of global security information to enable our users to apply it instantly ...
3 day practical computer forensics training course - Learn about forensic principles, evidence continuity and methodology to employ when conducting a forensic investigation. Using practical case scenarios, you will be guided through the process ...
The CGX server is a VM or appliance that provides a full suite of network access control applications to create a flexible and custom NAC solution. Optionally install agents to provide granular policy compliance and to deploy Dynamic NAC to control access ...
Mobile security and complexity don’t have to go hand in hand. Check Point Capsule is one seamless solution that addresses all your mobile security needs. Capsule protects your mobile devices from threats, provides a secure business environment for mobile ...
Check Point endpoint security includes data security, network security, advanced threat prevention, forensics, endpoint detection and response (EDR), and remote access VPN solutions. To offer simple and flexible security administration, Check Point’s enti ...
The Check Point Secure Platform Boot Camp is an intensive 5-day instructor-led course, which introduces the security administrator to Check Point's Secure Platform and Check Point NG. The course provides the information and experience necessary to deploy ...
The Internet provides a flexible and cost-effective infrastructure for extending the corporate network to all employees and key partners. Yet the Internet also conceals constantly changing threats. To take full advantage of the Internet, you must prevent ...
Checkmarx SAST (CxSAST) is an enterprise-grade static analysis solution used to identify hundreds of security vulnerabilities in custom code. It is used by development, DevOps, and security teams to scan source code early in the SDLC, identify vulnerabili ...
chkrootkit: shell script that checks system binaries for rootkit modification. 45 rootkits, worms and LKMs are currently detected. The following tests are made: aliens asp bindshell lkm rexedcs sniffer wted scalper slapper z2 amd basename biff chfn chsh ...
chkrootkit is a tool to locally check for signs of a rootkit. [talisker] I used to list all the files it checked as well as all the rootkits it detected. Nelson has taken this product to become a huge project with too many features to list please check ou ...
Chocolatey is a software management solution that gives you the freedom to create a simple software package and then deploy it anywhere you have Windows using any of your familiar configuration or system management tools. Designed to be simple to use, it ...