Directory: A-Z
Sucuri is a managed security service provider for websites. Their cloud-based platform gives you complete website security, including an antivirus and firewall for your website. Monitors for security incidents, fixes website hacks, and protects your site ...
Summercon is our chance to get together, talk to each other face-to-face, and swap information about innovations, trends, practices, and rumors in the field of computer security. We welcome all walks of life and all sides of the debate to Summercon: hacke ...
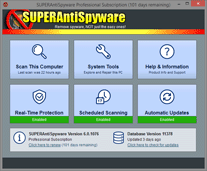
Advanced Detection and Removal: Detect and Remove Spyware, Adware and Remove Malware, Trojans, Dialers, Worms, KeyLoggers, HiJackers, Parasites, Rootkits, Rogue Security Products and many other types of threats. Light on System Resources and designed ...
The SystemWare Advanced Receiver Module (SWARM) Travel Case (STC) provides signal acquisition and analysis needs in a compact and portable package. Quick and simple to operate it can scan the RF spectrum from 1 kHz to 3GHz or 6 GHz with the internal recei ...
Safeguard your sensitive company data. Blue Coat Data Loss Prevention (DLP) enables you to detect and block potential data leaks quickly and accurately, all while achieving industry and regulatory compliance. With Blue Coat DLP, you can leverage powerful ...
Symantec Endpoint Encryption protects sensitive information and ensures regulatory compliance. It encrypts all files on the hard drive, sector-by-sector, for maximum security. It supports Windows, Mac, tablets, self-encrypting drives, and removable media ...
Securely manage desktops, laptops, and servers Symantec endpoint management solutions help manage, patch, and remediate application and OS configurations on desktops, laptops and servers throughout their lifecycle to strengthen endpoint security and maxi ...
Synopsys Static Analysis (Coverity) is a fast, accurate and scalable static analysis (SAST) solution that helps development and security teams address security and quality defects early in the software development lifecycle. Track and manage risks ac ...
SysAid Patch Management harnesses OEM technology to provide a full and seamless patch management solution from within SysAid Help Desk and SysAid ITSM. SysAid Patch Management allows IT administrators to: Get an overview of all the patches relevant to ...
The Symposium on Security for Asia Network aims to be a very different security conference from the rest of the security conferences that the information security community in Asia has come to be so familiar and frustrated with. SyScan intends to be a non ...
tiger is a set of scripts that scan a Un*x system looking for security problems, in the same fashion as Dan Farmer's COPS. 'tiger' was originally developed to provide a check of UNIX systems on the A&M campus that want to be accessed from off campus (clea ...
Tcpflow is a program that captures data transmitted as part of TCP connections (flows), and stores the data in a way that is convenient for protocol analysis and debugging. Each TCP flow is stored in its own file. Thus, the typical TCP flow will be stored ...
Techno Conferences include two distinct conferences: Techno Security Conference and Techno Forensics Conference. The Annual International Techno Security Conference has become known as a world class training and networking event now having had attendees ...
Tectia SSH Features Tectia SSH supports FIPS 140-2 certified cryptography Professional support & maintenance, including 24x7 support for business-critical applications Support for business platforms (Windows, Unix/Linux, IBM z/OS Mainframes) Integra ...
The Tenable Passive Vulnerability Scanner (PVS) can find out what is happening on your network without actively scanning it. Each PVS monitors your network for vulnerable systems, watches for potential application compromises, client and server trust rela ...
If you have a large network, the Security Center can be used to place multiple Nessus scanners throughout your infrastructure. Using multiple scanners decreases your scan time, but also has several other advantages. The Security Center can help any org ...
The weakest link in most systems is invariably the human element. How do you ensure that confidential files do not get uploaded to the cloud?, how can you tell if a disgruntled employee is carrying out malicious activities which compromise the integrity o ...
If you're looking for a free firewall test, you have come to the right place. Our computer security test is designed to scan your firewall and security software for vulnerabilities. It takes less than a minute to run our all-in-one spyware removal test. ...
TetherFilter Anti-Spam and Anti-Virus Appliance Solutions. Tethernet’s TetherFilter offers a complete anti spam and anti-virus solution in an easy to deploy appliance. With accurate anti-spam technology, near-zero administration and simple deployment Tet ...
Designed specifically for small and medium sized businesses TetherFilter: * Drastically reduces spam flow into your mail servers and users dekstops * Installs easily into your existing infastrucutre * Works alongside any existing anti-spam technologies ...