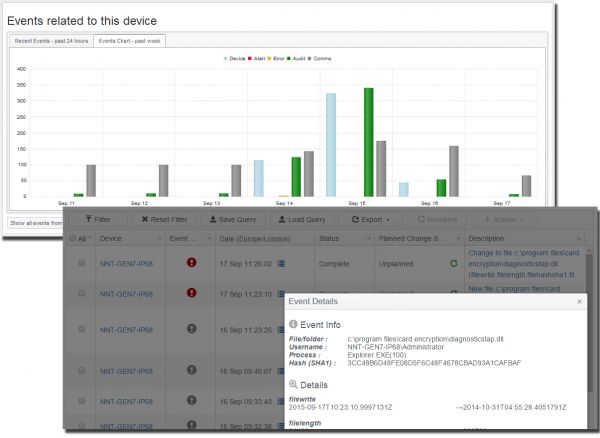
When a system is compromised an attacker will often alter certain key files to provide continued access and prevent detection. By applying a message digest (cryptographic hash) to key files and then checking the files periodically to ensure the hash hasn’t altered a degree of assurance is maintained. On detecting a change an alert will be triggered. Furthermore, following an attack the same files can have their integrity checked to assess the extent of the compromise.
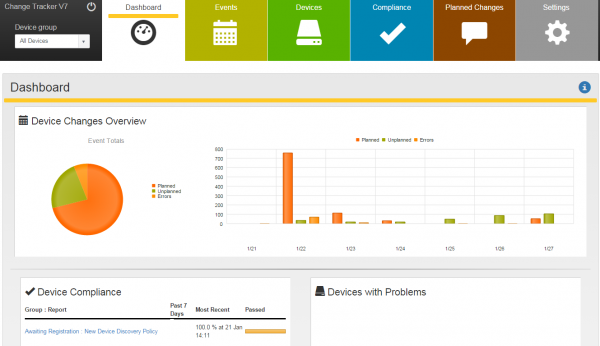
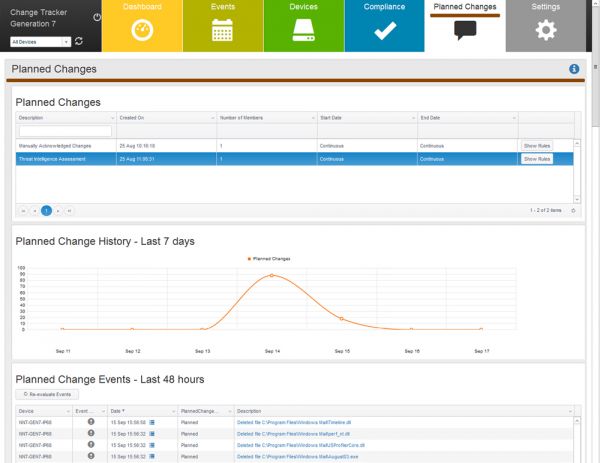
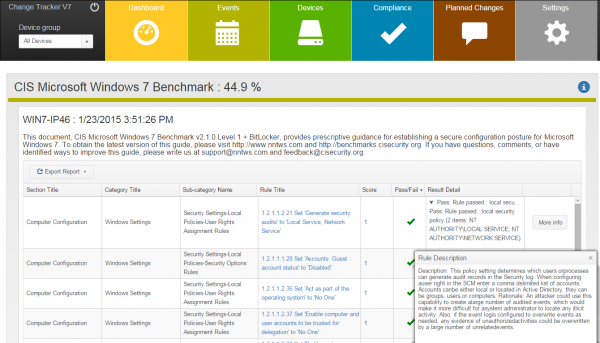
NNT Change Tracker Gen 7 R2 provides critical and fundamental cyber security prevention and detection. It does this by leveraging the required security best practice disciplines of system configuration and integrity assurance combined with the most compre ...
AIDE (Advanced Intrusion Detection Environment) is a free replacement for Tripwire. It does the same things as the semi-free Tripwire and more. It creates a database from the regular expression rules that it finds from the config file. Once this data ...
chkrootkit is a tool to locally check for signs of a rootkit. [talisker] I used to list all the files it checked as well as all the rootkits it detected. Nelson has taken this product to become a huge project with too many features to list please check ou ...
integrit is an alternative to file integrity verification programs like tripwire and aide. It helps you determine whether an intruder has modified a computer system. Without a system like integrit, a sysadmin can't know whether the tools he/she uses to in ...
samhain is an open source file integrity and host-based intrusion detection system for Linux and Unix. It can run as a daemon process, and and thus can remember file changes - contrary to a tool that runs from cron, if a file is modified you will get only ...
Tripwire File Integrity Monitoring (FIM) has the unique, built-in capability to reduce noise by providing multiple ways of determining low-risk change from high-risk change as part of assessing, prioritizing and reconciling detected change. Auto-promoting ...
Verisys is an system and file integrity monitoring solution for Windows, Linux and network devices that allows you to maintain the integrity of business critical files and data by detecting unauthorised changes. Verisys is easily configured to suit your ...
CimTrak is a comprehensive file integrity monitoring and compliance software application that is easy to use and less expensive then similar solutions. Customers worldwide look to CimTrak as an alternative to other file integrity monitoring tools such as ...
File integrity monitoring (FIM) protects sensitive information from theft, loss, and malware. Included as part of the Security Event Manager software suite.
Afick is a security tool, very close from to well known tripwire. It allows to monitor the changes on your file systems, and so can detect intrusions. It's designed to be quick and portable. For now, it has been tested on Windows XP, 2000, Vista, Seve ...