Forensic Tools
These are tools for analyzing a breach in security in some way. Typically they are used for collecting data about the breach after the fact, or analyzing software to see how it performs the attack. Many reverse engineering tools will be listed here, as well as forensic recovery tools.
Other information about Forensic Tools
- 8 Articles for Learning Android Mobile Malware Analysis - by Lenny Seltzer of the ISC
NTI's forensic software tools are used in security reviews, internal audits and computer related investigations. Some of the tools are also used to identify and eliminate sensitive data leakage in classified government agencies. They are sold separately a ...
The tools included in the PsTools suite, which are downloadable individually or as a package, are: PsExec - execute processes remotely, PsFile - shows files opened remotely, PsGetSid - display the SID of a computer or a user, PsKill - kill processes by na ...
NetAnalysis will automatically rebuild HTML web pages from an extracted cache, automatically adding the correct location of the graphics allowing you to view the page as the suspect did. NetAnalysis also allows you to easily view JPEG and other pictures t ...
chkrootkit: shell script that checks system binaries for rootkit modification. 45 rootkits, worms and LKMs are currently detected. The following tests are made: aliens asp bindshell lkm rexedcs sniffer wted scalper slapper z2 amd basename biff chfn chsh ...
Foremost is a console program to recover files based on their headers, footers, and internal data structures. This process is commonly referred to as data carving. Foremost can work on image files, such as those generated by dd, Safeback, Encase, etc, or ...
md5deep is a set of programs to compute MD5, SHA-1, SHA-256, Tiger, or Whirlpool message digests on an arbitrary number of files. md5deep is similar to the md5sum program found in the GNU Coreutils package, but has the following additional features: Re ...
Autopsy is a digital forensics platform and graphical interface to The Sleuth Kit® and other digital forensics tools. It is used by law enforcement, military, and corporate examiners to investigate what happened on a computer. You can even use it to recov ...
Ontrack PowerControls recovers individual mailboxes, messages and attachments without needing to restore the entire backup. Use the powerful search capability to rapidly find the items you need for eDiscovery and compliance. Versions for Exchange, ShareP ...
GNU Parted is a program for creating, destroying, resizing, checking and copying partitions, and the file systems on them. This is useful for creating space for new operating systems, reorganising disk usage, copying data between hard disks and disk imagi ...
mac-robber is a digital investigation tool that collects data from allocated files in a mounted file system. This is useful during incident response when analyzing a live system or when analyzing a dead system in a lab. The data can be used by the mactime ...
WinHex is in its core a universal hexadecimal editor, particularly helpful in the realm of computer forensics, data recovery, low-level data processing, and IT security. An advanced tool for everyday and emergency use: inspect and edit all kinds of files, ...
IDA Pro as a disassembler is capable of creating maps of their execution to show the binary instructions that are actually executed by the processor in a symbolic representation (assembly language). Advanced techniques have been implemented into IDA Pro s ...
OllyDbg is a 32-bit assembler level analysing debugger for Microsoft Windows. Emphasis on binary code analysis makes it particularly useful in cases where source is unavailable. OllyDbg is a shareware, but you can download and use it for free. Special hig ...
Curuncula is a tool shipped as a loadable kernel module that aims to detect rootkits based on the Intel debugging support facilities. Rootkits that set the GD access flag are also detected. It makes use of the "last branch recording" mechanism provided by ...
Simple Carver Suite is a collection of unique tools designed for a number of purposes including but not limited to forensic computing, data recovery and eDiscovery. Simple Carver originally began as a single data recovery tool, a basic file carver which h ...
Analyze Skype chat logs, contact lists, SMS messages with SkypeAlyzer a forensic tool designed to work with both the old Skype database files – found in a series of .dbb files and the newer Skype database files (main.db).
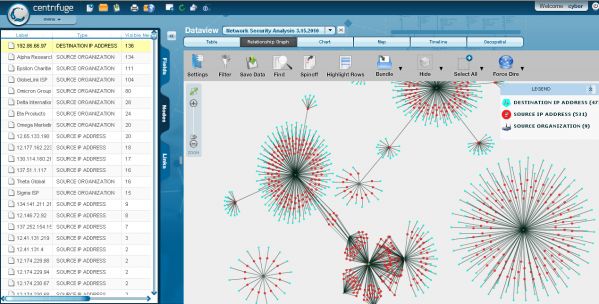
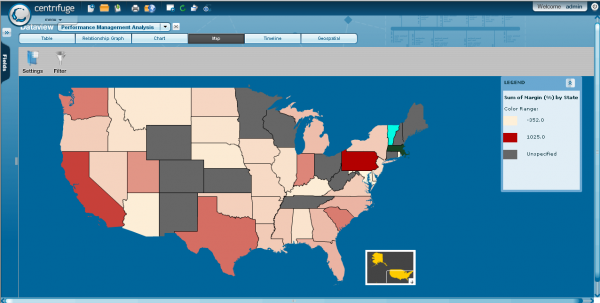
Centrifuge Analytics makes it easy to harness the power of your data, visualize discoveries, collaborate to draw conclusions and make effective predictions that will have an immediate impact to your organization. Data Discovery Not Data Processing ...
Unhide is a forensic tool to find hidden processes and TCP/UDP ports by rootkits / LKMs or by another hidden technique. // Unhide (ps) Detecting hidden processes. Implements six techniques * Compare /proc vs /bin/ps output * Compare inf ...
AIR is a GUI front-end to dd/dc3dd designed for easily creating forensic images. by Steve Gibson and Nanni Bassetti Features: * auto-detection of IDE and SCSI drives, CD-ROMs, and tape drives * choice of using either dd or dc3dd (Note: dc3d ...
log2timeline is a framework for automatic creation of a super timeline. The main purpose is to provide a single tool to parse various log files and artifacts found on suspect systems (and supporting systems, such as network equipment) and produce a timeli ...