Forensic Tools
These are tools for analyzing a breach in security in some way. Typically they are used for collecting data about the breach after the fact, or analyzing software to see how it performs the attack. Many reverse engineering tools will be listed here, as well as forensic recovery tools.
Other information about Forensic Tools
- 8 Articles for Learning Android Mobile Malware Analysis - by Lenny Seltzer of the ISC
MOBILedit Forensic is a phone extractor, data analyzer and report generator all in one solution. A powerful 64-bit application using both the physical and logical data acquisition methods, MOBILedit Forensic is excellent for advanced application analyzer, ...
Lawfully access locked devices with easeBypass pattern, password or PIN locks and overcome encryption challenges quickly on popular Android and iOS devices Support for the broadest range of devicesCollect data from mobile phones, drones, SIM Cards, SD ca ...
NetAnalysis will automatically rebuild HTML web pages from an extracted cache, automatically adding the correct location of the graphics allowing you to view the page as the suspect did. NetAnalysis also allows you to easily view JPEG and other pictures t ...
CD/DVD Inspector reads all major CD and DVD filesystem formats including ISO-9660, Joliet, UDF, HSG, HFS and HFS+. When the disc being examined contains more than a single filesystem, all filesystems found are displayed. Multiple filesystems a ...
Provides over two dozen indexed and unindexed text search options for all popular file types. Supports full-text as well as field searching in all supported file types. Has multiple relevancy-ranking and other search sorting options. dtSearch can instantl ...
Hackman 7 is a freeware hex editor and disassembler. It comes with cryptography capabilities, decoding with ready and self-made algorithms and a fully-featured editor. You can edit virtually any file, disk, ZIP drive, Ram Drive, Smart Media, Compact Flash ...
Nuix Evidence Mover is designed to copy evidence files images from one storage location, to antoher. It creates a hash of the files before and after moving to ensure the data has been copied accurately, and to maintain the chain of custody.
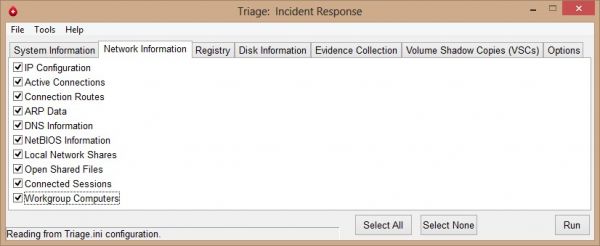
Triage-IR is a script written by Michael Ahrendt, which will collect system information, network information, registry hives, disk information and will also dump memory. One of the capabilities of Triage-IR is collecting information from Volume Shadow Cop ...
Maresware: The Suite provides an essential set of tools for investigating computer records plus powerful data analysis capabilities. This bundled suite of over 40 separate, highly-targeted programs gives you the flexibility to accomplish a wide variety of ...
The National Software Reference Library (NSRL) is designed to collect software from various sources and incorporate file profiles computed from this software into a Reference Data Set (RDS) of information. The RDS can be used by law enforcement, governmen ...
NTI's forensic software tools are used in security reviews, internal audits and computer related investigations. Some of the tools are also used to identify and eliminate sensitive data leakage in classified government agencies. They are sold separately a ...
The tools included in the PsTools suite, which are downloadable individually or as a package, are: PsExec - execute processes remotely, PsFile - shows files opened remotely, PsGetSid - display the SID of a computer or a user, PsKill - kill processes by na ...
The first forensic browser able to quickly and easly capture web pages that are to be brought to trial in criminal and civil proceedings. Acquisition of all websitesFAW acquires websites of any type: HTML5, CMS, static, dynamic, with frames, blogs, e-com ...
Process monitor is a monitoring tool for Windows that shows real-time file system, Registry and process/thread activity. it combines the features of two legacy Sysinternals utilites, Filemon, Regmon, and adds an extensive list of enhancements including ri ...
Belkasoft Live RAM Capturer is a tiny free forensic tool that allows to reliably extract the entire contents of computer’s volatile memory—even if protected by an active anti-debugging or anti-dumping system. Separate 32-bit and 64-bit builds are availabl ...
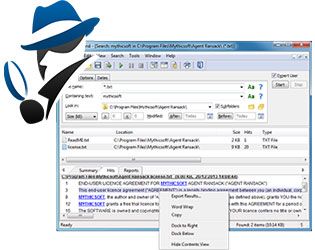
Agent Ransack is a free file search tool for finding files on your PC or network drives. It has a Lite mode, which is FREE for both personal and commercial use but also a Professional mode that includes optional pay-for features. First released in April ...
PMDump is a tool that lets you dump the memory contents of a process to a file without stopping the process. This can be useful in a forensic investigation.
Ontrack PowerControls recovers individual mailboxes, messages and attachments without needing to restore the entire backup. Use the powerful search capability to rapidly find the items you need for eDiscovery and compliance. Versions for Exchange, ShareP ...
GNU Parted is a program for creating, destroying, resizing, checking and copying partitions, and the file systems on them. This is useful for creating space for new operating systems, reorganising disk usage, copying data between hard disks and disk imagi ...
mac-robber is a digital investigation tool that collects data from allocated files in a mounted file system. This is useful during incident response when analyzing a live system or when analyzing a dead system in a lab. The data can be used by the mactime ...