Tags: Compliance
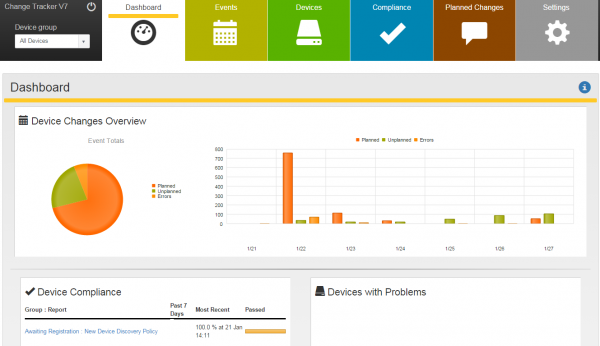
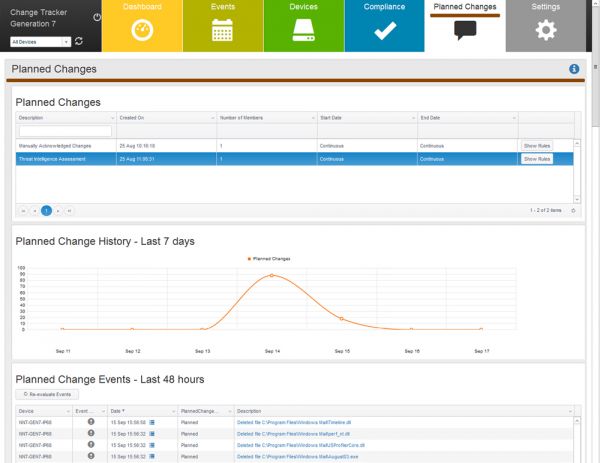
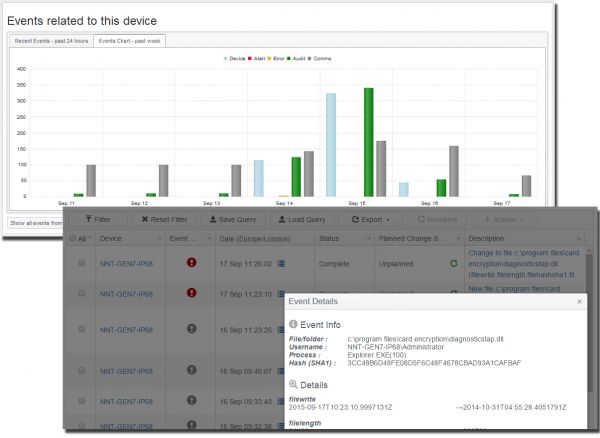
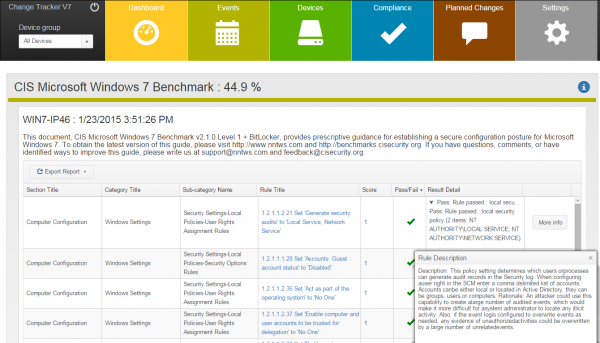
NNT Change Tracker Gen 7 R2 provides critical and fundamental cyber security prevention and detection. It does this by leveraging the required security best practice disciplines of system configuration and integrity assurance combined with the most compre ...
Verisys is an system and file integrity monitoring solution for Windows, Linux and network devices that allows you to maintain the integrity of business critical files and data by detecting unauthorised changes. Verisys is easily configured to suit your ...
CimTrak is a comprehensive file integrity monitoring and compliance software application that is easy to use and less expensive then similar solutions. Customers worldwide look to CimTrak as an alternative to other file integrity monitoring tools such as ...
The McAfee Application Data Monitor appliance decodes an entire application session to Layer 7, providing a full analysis of everything from the underlying protocols and session integrity all the way up to the contents of the application (such as the text ...
The non-intrusive design of McAfee Database Event Monitor for SIEM supports your expanding compliance auditing and reporting requirements and enhances security operations. While it monitors all database transactions, Database Event Monitor for SIEM provid ...
McAfee Policy Auditor helps you report consistently and accurately against key industry mandates and internal policies across your infrastructure or on specific targeted systems. Policy Auditor is an agent-based IT audit solution that leverages the Securi ...
McAfee Total Protection for Data Loss Prevention (DLP) safeguards intellectual property and ensures compliance by protecting sensitive data wherever it lives — on premise, in the cloud, or at the endpoints. McAfee DLP is delivered through low-maintenance ...
Nipper accurately audits the security of firewalls, switches and routers to detect exploitable misconfigurations that pose risk to the network, prioritized by criticality. Applying Nipper’s compliance lens to the findings also provides the evidence needed ...
In zero-trust architecture, ISE is the policy decision point. It gathers intel from the stack to authenticate users and endpoints, automatically containing threats. ?Harness the power of resilience? ?Resilience begins with secure connections. ISE helps ...
With hundreds of lines of code to check - and vulnerabilities often subtle and hard to find - a serious data breach is often the first sign that a web application has problems. Having secured thousands of production applications against more than 11 billi ...
Safend Inspector prevents transfer of sensitive company information. As information is processed it is classified and its access permissions and security profile are configured. During data transfer Inspector checks for sensitive information in its c ...