These products should have the ability to not only identify but also remediate vulnerabilities.
SanerNow Featured
SecPod’s SanerNow is an ADVANCED VULNERABILITY MANAGEMENT solution for preventing cyberattacks and achieving a security risk compliance posture. IT Security Teams use SanerNow to effectively reduce the risk imposed by vulnerabilities, misconfigurations, a ...
NeXpose is an enterprise-level vulnerability assessment and risk management product that identifies security weaknesses in a network computing environment. It offers a comprehensive, one-stop solution for data gathering, reporting and remediation, elimina ...
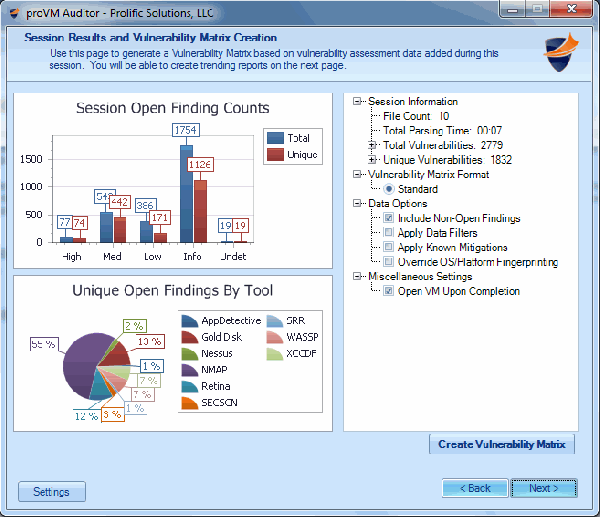
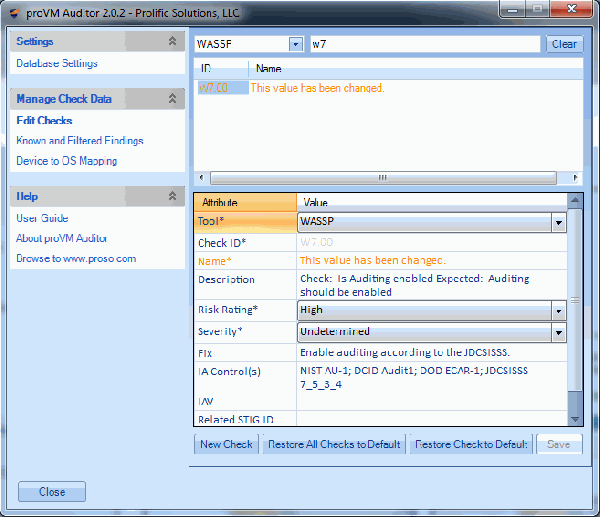
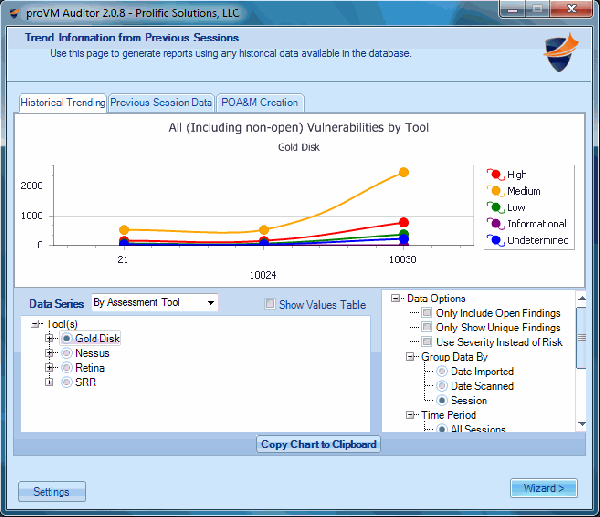
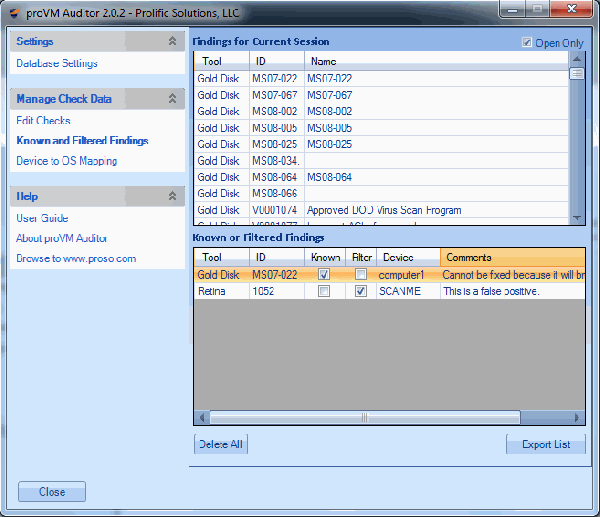
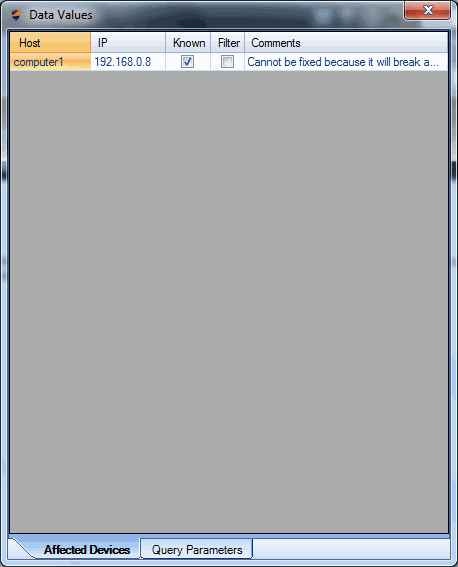
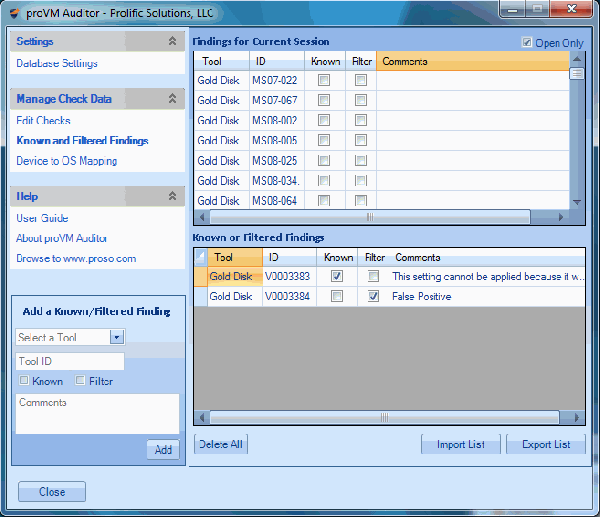
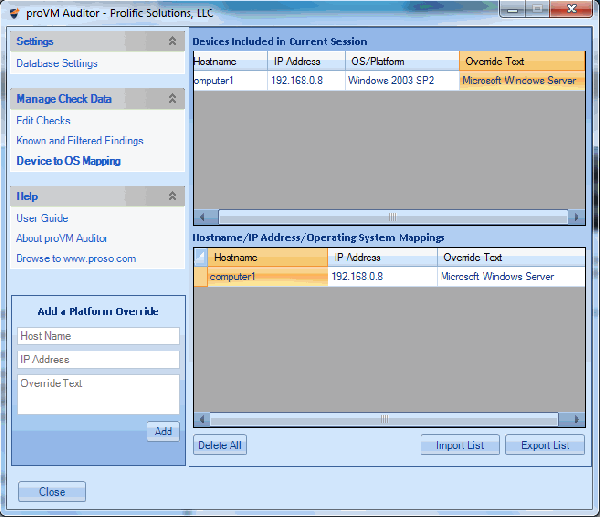
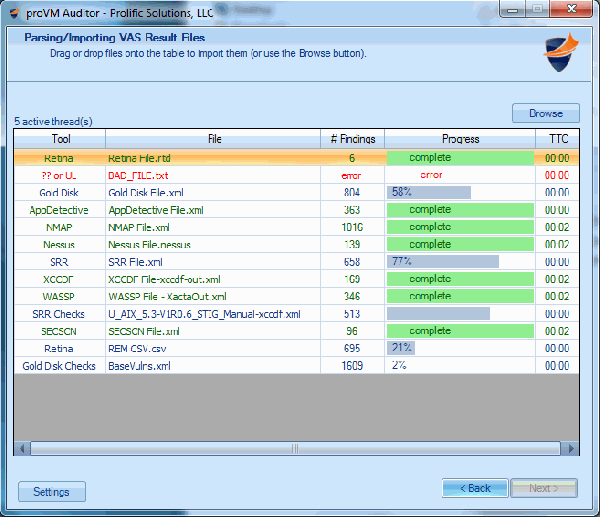
Manage all of your vulnerability data from 3rd party scanners with one console. proVM Auditor ingests data from vulnerability assessment scanners and allows you to perform centralized analysis of all of your findings. The SQL database supports features su ...
edgescan is the only hybrid cloud based solution in Europe which combines both vulnerability scanning and manual verification on an on-going basis. It is a SaaS (Software as a Service) solution which detects technical vulnerabilities in Internet-facing sy ...
Qualys Cloud Platform, previously known as QualysGuard, consists of integrated apps to help organisations simplify security operations and lower the cost of compliance by delivering critical security intelligence on demand and automating the full spectrum ...
Before you can secure a network, you have to know how it's threatened. SAINT, or the Security Administrator's Integrated Network Tool, uncovers areas of weakness and recommends fixes. With the SAINT® vulnerability scanner, you can: Identify vulnerabilitie ...
OUTSCAN combines ease-of-use with rich functionality and a powerful vulnerability scanning engine into a unique solution. OUTSCAN scans your perimeter which consists of the same Internet-facing devices that hackers target. With OUTSCAN, it is easy to dete ...
AppScan delivers application security testing tools to ensure your business, and your customers, are not vulnerable to attacks. Detect application vulnerabilities before they become a problem, remediate them and ensure compliance with regulations. Four pr ...