Network Enumeration is the discovery of hosts/devices on a network, they tend to use overt discovery protocols such as ICMP and SNMP to gather information, they may also scan various ports on remote hosts for looking for well known services in an attempt to further identify the function of a remote host and solicit host specific banners. The next stage of enumeration is to fingerprint the Operating System of the remote host. Whilst products that accomplish this are beyond the scope of this page, they can be found on the Active OS Fingerprinting Page. Most vulnerability Scanners will also perform network enumeration task and a whole lot more, if you are looking for vulnerability scanners go to Network Mapping Tools
For Wireless network discovery try Wireless Security Products
Unicornscan is a new information gathering and correlation engine built for and by members of the security research and testing communities. It was designed to provide an engine that is Scalable, Accurate, Flexible, and Efficient. It is released for the c ...
hping2 is an interactive packet costructor and responses analyzer that uses the same CLI of the ping program (but with a lot of extensions). It can be used to performs a lot of tasks, like testing of firewall rules, (spoofed) port scanning, et cetera.
Angry IP Scanner (or simply ipscan) is an open-source and cross-platform network scanner designed to be fast and simple to use. It scans IP addresses and ports as well as has many other features. It is widely used by network administrators and just curiou ...
Network Security Analysis Tool is a robust scanner which is designed for: Different kinds of wide-ranging scans, keeping stable for days Scanning on multi-user boxes (local stealth and non-priority scanning options) Professional-grade penetration tes ...
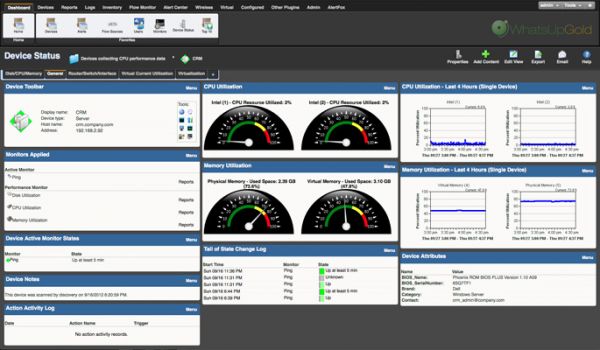
Ipswitch WhatsUp Gold is the world's leading network management software with over 70,000 networks reliably monitored worldwide. Built on a scalable and extensible architecture offering automated device discovery and network mapping, real-time SNMP and WM ...
Verify connectivity to a particular device on your network. Quantitatively test data connections between your computer and a remote system. Trace the path to a network host or device. Obtain information on host names and IP addresses. Scan your ne ...
NetCrunch can be installed in minutes - no additional downloads needed. It can be run on any Windows machine (Windows 7 or newer). For server monitoring, it does not require SNMP to be installed on Windows (or Linux, Mac OS X or BSD) and uses Act ...
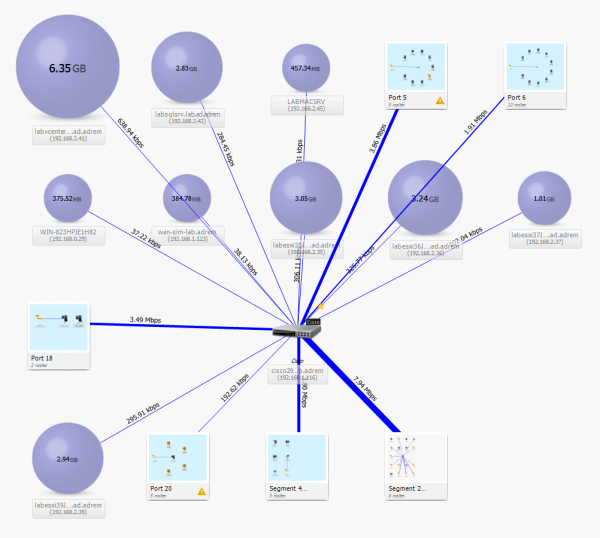
Device discovery Track assets scattered across your entire enterprise. Gather a complete and accurate view of all network endpoints, including managed and unmanaged devices, and authorized and unauthorized devices. Understand what types of devices are on ...
Nipper accurately audits the security of firewalls, switches and routers to detect exploitable misconfigurations that pose risk to the network, prioritized by criticality. Applying Nipper’s compliance lens to the findings also provides the evidence needed ...
Firewalk is an active reconnaissance network security tool that attempts to determine what layer 4 protocols a given IP forwarding device will pass. Firewalk works by sending out TCP or UDP packets with a TTL one greater than the targete ...
Pig or (Packet intruder generator) is a Linux based packet crafting tool. You can use Pig for a number of different purposes such as testing your IDS/IPS through to spoofing ARP. Pig brings with it a number of well-known attack signatures which are ready ...
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience functions, interactive help, and command completion, Recon-ng provides a powerful environment in whic ...